Web Supply Chain Visibility: Best Practices For Fearless Security

Originally published on SC Media UK here.
While businesses harden servers, attackers are exploiting trusted client-side third-party scripts that traditional security tools can’t see. A recent breach at Leeds United FC reveals a supply chain crisis every CISO must confront.
How did Leeds United’s security team miss a breach despite having “everything in place?” Get full analysis in our proactive prevention playbook with five proven strategies here →
The Hidden Vulnerability in Your Websites’ DNA
Modern websites are complex assemblies of first- and third-party code. This dynamic ecosystem enables innovation but also creates a dangerously opaque supply chain. One of the greatest threats often lies not in your own infrastructure, but in the code imported from external vendors. This client-side attack surface is a growing blind spot, and as attackers become more sophisticated, organisations without deep visibility are courting disaster.
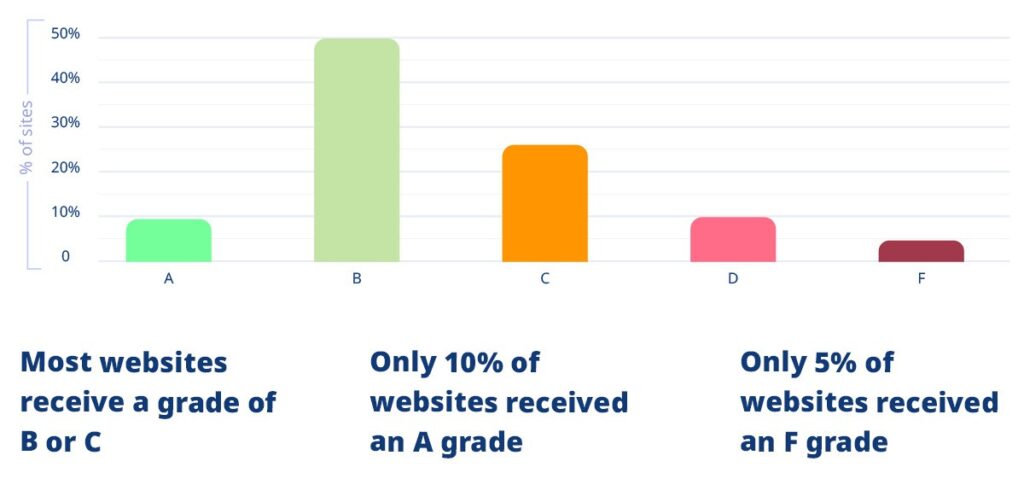
Recent research reveals a stark reality: Only 10% of websites achieve an “A” grade for web security, with the entertainment and retail sectors among the most vulnerable. This is not theoretical. It’s a practical reality with serious consequences, as demonstrated by years of high-profile breaches, such as those on Marks & Spencer and Macy’s.
A Real-World Case Study: Leeds United FC
In February 2025, Leeds United FC’s online store was hit by a Magecart credit-card skimming attack. For six days, a malicious script operated undetected on the checkout page, silently harvesting fan payment details.
The attackers exploited a compromised third-party service, likely a chat widget, analytics tool or advertising module, to inject a JavaScript skimmer directly into the payment page. This stealth was achieved through sophisticated obfuscation; the malicious payload was likely hidden within a seemingly harmless file, disguised through layers of encoding to make it unreadable to security scanners. Because the code executed in the user’s browser, it bypassed traditional defences such as WAFs.
No alerts were triggered by existing tools. The breach came to light only when the UK’s National Cyber Security Centre (NCSC) flagged suspicious outbound traffic during unrelated monitoring.
As Graham Peck, Head of IT and Security at Leeds United, put it:
Why Traditional Security Fails Against Client-Side Attacks
For CISOs: Your perimeter defences are blind to client-side threats. WAFs, network monitoring, and endpoint protection all operate server-side, leaving the browser environment, where modern attacks execute, completely unmonitored.
For Security Managers: Your incident response playbooks likely don’t address client-side compromises. When a Magecart attack hits, you’ll need specialised forensics, browser-based evidence collection, and rapid script containment, capabilities most teams lack.
For IT Directors: Third-party script sprawl is creating ungoverned risk. Your teams approve marketing tools, analytics platforms, and customer service widgets without visibility into their client-side behaviour or supply chain security posture.
A Broader Trend
The Leeds incident is not an anomaly. It’s the latest in a long series of supply chain compromises. British Airways’ 2018 breach, which led to a multi-million-pound ICO fine, and Ticketmaster‘s chatbot compromise highlighted the risk years ago.
In one recent case, a skimmer stayed active for months by disguising exfiltration as legitimate Google Analytics traffic. Cybercriminals now routinely abuse trusted marketing tools like Google Tag Manager, as this activity is often allow-listed and blends in with normal operations.
Moreover, in April 2023, multiple global e-commerce sites fell victim to sophisticated Magecart attacks using fake Shopify and CloudFlare CDN domains. The attackers created counterfeit input fields that captured payment data while legitimate transactions appeared to process normally, a level of sophistication that traditional security tools simply cannot detect.
This isn’t just a technical problem bleeding into the business; it’s often originating there. Further research reveals that 53% of unjustified access to sensitive data is perpetrated by third-party marketing apps, highlighting the need to scrutinise these integrations as closely as any other.
Losses from such attacks are staggering. In 2024, global e-commerce fraud hit $44.3 billion, with e-skimming Magecart-style attacks a significant contributor. Healthcare, finance, education and government organisations all face the same level of risk exposure, as bad actors will exploit any weakness they can find.
Essential Defence Strategies: A Preview
The UK’s National Cyber Security Centre (NCSC) stresses one principle above all: Visibility. Without it, effective defence is impossible. To move from principle to practice, organisations must adopt a multi-layered defence that provides granular control and real-time insight into the behaviour of their websites.
Recommended practices include:
● Dynamic Script Inventory Management
Maintain a real-time catalogue of all third-party scripts, their purpose, permissions, and changes. Leeds United’s breach occurred because they trusted a vendor’s patch confirmation without verification (something they didn’t have the tools to do at the time). PCI DSS v4.0 now mandates comprehensive script inventories with written justifications for all payment page scripts.
● Robust Content Security Policy (CSP)
Strictly whitelist trusted domains and resources to block unauthorised script execution. A properly configured CSP could have prevented the Leeds United attack by blocking malicious scripts regardless of how they were injected into third-party services.
● Sub-resource Integrity (SRI)
Use cryptographic hashes to prevent tampered files from executing. This acts as insurance against compromised CDNs and third-party services. If SRI had been implemented, browsers would have rejected a tampered script immediately.
● Continuous Client-Side Monitoring
Detect suspicious behaviour in real time, such as unauthorised form access or data exfiltration, beyond what server-side tools can see. Modern attacks use sophisticated techniques like encrypted favicon payloads and counterfeit input fields that only behavioural monitoring can catch.
● Specialised Incident Response Plans
Prepare playbooks for isolating compromised scripts, assessing breach scope, and coordinating with regulators and law enforcement. Generic incident response procedures leave teams unprepared for client-side attack scenarios.
Get the complete implementation playbook with step-by-step deployment guides here →
Lessons from Leeds United
Leeds contained the attack within six days, far faster than the industry average of 241 days to identify and contain breaches (according to IBM’s 2025 Cost of a Data Breach Report).
Even so, the fallout exposed systemic weaknesses. Outsourced website management limited the club’s visibility into its own retail platform. Post-incident analysis also revealed the missing security headers and over-permissive third-party access that are common across vulnerable sites. The breach became a catalyst for stronger oversight, tighter controls and ongoing monitoring.
As Graham Peck reflected after implementing an agentless client-side security tool: “The advantage was, it was very low impact. It doesn’t affect the performance of the website at all. It’s non-intrusive…but brings back a lot of information.”
The Path Forward
The case studies of Leeds United, British Airways, and countless others show that even security-minded organisations are vulnerable. The complexity of modern web apps makes client-side compromise inevitable without a new approach.
The answer lies in moving from trust-based vendor relationships to verification-based security models, built on continuous monitoring, granular visibility, and the assumption that breaches will happen.
For CISOs: Your board expects client-side security governance.
For Security Managers: Your team needs specialised playbooks and tools for client-side incidents. Generic response procedures leave you exposed.
For IT Directors: Your business relies on third-party scripts. You need visibility into what they’re actually doing.
The real question for security leaders is simple:
Do you know what code is running on your website right now?
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







