PCI DSS Best Practices To Easily Meet The New Requirements In 2023

With the increasing number of data breaches and cyber attacks in recent years, organizations are under more pressure than ever to ensure the security of their customers’ sensitive information. To this end, the Payment Card Industry Data Security Standard (PCI DSS) has been put in place to provide a framework for businesses that handle cardholder information. However, the requirements for compliance can be complex and time-consuming, particularly with the updated regulations coming into effect in 2023. In this article, we will discuss PCI DSS best practices that organizations can adopt to easily meet the new PCI DSS requirements and enhance their overall data security posture.
What is PCI DSS?
Whether your business is a small e-commerce shop or a huge multinational, if it processes, stores, or transmits cardholder data, then it will be subject to the Payment Card Industry Data Security Standards (PCI DSS). This is the set of security standards that were created by major credit card companies, including Visa, MasterCard, and American Express, to ensure that organizations handle cardholders’ data safely. These PCI DSS best practices may not be laws but breaking the PCI Data Security Council’s rules can be just as damaging for your business.
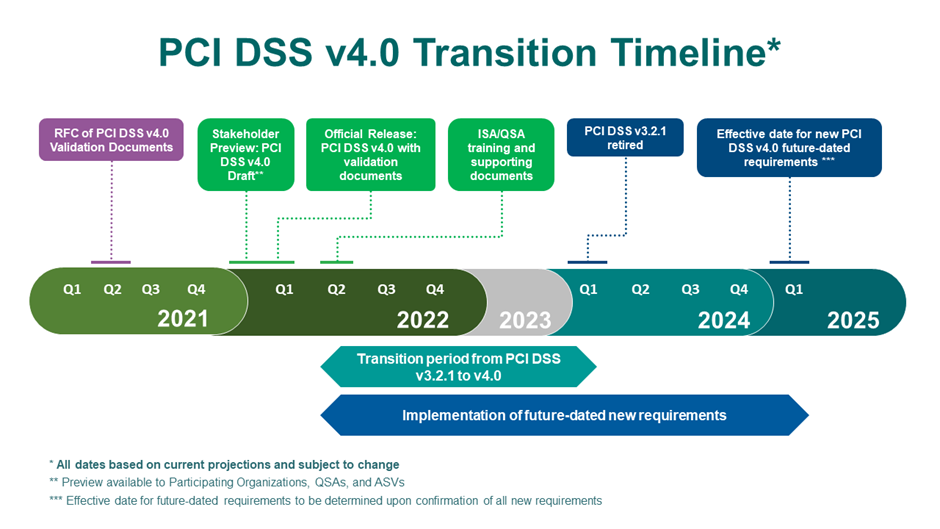
PCI DSS version 1.0 came out in December 2004. Since then, it’s gone through several updates and the next big change is coming with version 4.0. This revised version introduces some new requirements that are currently being promoted as best practices, but on March 31, 2025, they will become mandatory. In Q1 2024 v3.2.1 will retire.
This will be problematic for any company that isn’t prepared. The PCI Compliance Guide says that any organization that is found to be in breach of PCI DSS requirements could be fined between $5,000 and $100,000 per month by payment providers until they achieve compliance.
Fines for non-compliance can also lead to bad publicity which can negatively affect your business, as well as impact the relationship with your bank. It may impose its own penalties for non-compliance with payment processing regulations, and it could also increase transaction fees or even end the relationship entirely.
Faced with these concerns, many organizations are opting for monitoring products that take care of these compliance hurdles. The Reflectiz solution is one of these products, and it now features a new PCI dashboard that puts important information about your security posture right at your fingertips.
Although March 2025 may seem like it’s a long way off, it isn’t. That’s why we recommend you start implementing the new PCI DSS best practices now. That way, if you encounter any problems, you’ll have time to put them right. Here’s how the transition timeline looks right now:
Is every organization treated the same?
Although every organization that processes customer financial data must adhere to PCI DSS best practices, the exact requirements vary according to the size of the business:
- Level 1 – More than six million transactions a year
- Level 2 – One to six million transactions a year
- Level 3 – 20k to 1 million transactions a year
- Level 4 – Up to 20k transactions a year
Level 1 organizations need to get an annual report done by a qualified security assessor (QSA). Businesses that suffer a data breach must also undergo an external audit, as well as quarterly scans of their network and an annual penetration test. PCI Level 2 and 3 merchants are required to complete a Self-Assessment Questionnaire (SAQ), do a quarterly network scan, and submit an Attestation of Compliance (AOC). Level 4 merchants are only required to complete an SAQ, do quarterly vulnerability scans, and submit an AOC.
What are the new PCI DSS best practices?
Before we list them, here are a couple of other things that have also changed recently.
Customized Approach/Defined Approach
Version 4.0 introduces something called the customized approach, which gives organizations more flexibility to, “…use innovative technologies to achieve security objectives. These new technologies often do not fit within the traditional method for implementing and validating PCI DSS.” So, this change acknowledges that more organizations are turning to solutions like the Reflectiz platform. It’s still possible to satisfy security objectives using older methods though, and these approaches fall under what’s now known as the defined approach.
Risk Assessments
One of the biggest changes with the latest PCI DSS best practices is the use of a very structured and formalized risk assessment process. The expectation now is that any changes to a system (such as adding a firewall for instance), should be formally risk assessed.
Updated PCI DSS best practices for v4.0
Section 3
3.2.1
Organizations will now be required to encrypt or protect sensitive authentication data before it’s authorized.
3.3.3
When issuers store sensitive authentication data they will now need to make sure it is encrypted. Some legacy systems may be problematic if encryption software isn’t available for them, so it would be best to start exploring solutions sooner rather than later.
3.4.2
If you access the cardholder data environment (CDE) via remote access technology, you must prevent PAN data from being copied and relocated.
You will now need to enforce this with a technological solution. Your remote access software may have settings that can block the relevant actions. Your current processes and resources may affect how easily you can implement this requirement.
3.5.1.2
You should no longer use disk-level or partition-level encryption to make PAN unreadable.
3.5.5.1
Organizations will now need to use keyed cryptographic hashing, which is different from the most common hash algorithms in use currently. You may be able to use, HMAC, CMAC, or GMAC instead, with a minimum of 128-bit cryptographic strength.
Section 4
4.2.1
Organizations will now need to demonstrate that they are documenting, tracking, and inventorying SSL and TLS certificates used for transmitting sensitive data over public networks.
Section 5
5.3.3
Organizations will need to scan removable media that are used in the common data environment.
5.4.1
Automatic email phishing protection is now required.
Section 6
6.4.2
It is now a best practice to use a web application firewall to protect any web apps exposed to the Internet.
6.4.3
You need to monitor and manage all payment page scripts that are loaded and executed in the consumer’s browser. The Reflectiz platform accomplishes this without adding any scripts of its own to websites. The solution is entirely remote, but it gives you broad oversight of all such scripts and apps across the whole website, not just payment pages.
Section 7
7.2.4, 7.2.5, 7.2.5.1
This is about role-based access control and the changes call for tighter controls around account reviews and improved processes for reviewing systems, users, and applications.
Section 8
8.3.6
Minimum password lengths are increasing from seven to 12 alpha and numeric characters. This might be easily fixed with some apps but others may call for code changes.
8.3.10.1
If you aren’t using multifactor authentication (i.e. you are using passwords alone) you will now need to change your passwords every 90 days.
8.4.2
All access to the CDE now requires multifactor authentication, rather than just access from external locations, so this covers internal admin access to things like firewalls and servers.
8.5.1
Right now, most systems ask for a username and password and only move on to the next stage if they are input correctly. Going forward, all stages of the authentication process need to be completed for it to succeed, and the process should not reveal which stage caused a failure.
8.6.2
All application and system passwords that could be used for interactive login should have additional approval and tracking controls related to how they are used and they can no longer be placed in a script or a file.
Section 10
10.4.1.1
Logs can no longer be reviewed manually.
10.7.2
The requirement to protect critical security control systems, generate alerts if they fail, and respond promptly has now been extended to all organizations. So, if your firewall or IDS system goes down, you need a way to detect the problem, flag it, and respond to it without delay.
Section 11
11.3.1.2
Authentication is now mandatory for internal vulnerability scanning. Simply scanning ports and services is no longer sufficient. If a vulnerable service requires credentials for access, such as a web application, it must be used to access the port or service for evaluation purposes. A crucial aspect of this updated standard is that the credentials employed by the vulnerability assessment (VA) scanner must be inputted into the system and securely saved. This functionality must be included in the VA scanning solution.
11.5.1.1
Systems need to detect and alert for any covert communication channels (such as DNS tunneling) that are being used for malware purposes. You may need to change your current IDS/IPS system to meet this requirement.
11.6.1
This section concerns change and tamper detection mechanisms for payment pages. It comes in response to the rise in web skimming attacks on e-commerce providers in the last few years, but the Reflectiz platform takes care of this already.
Section 12
12.5.2 (Immediately effective for 4.0 assessments)
In earlier versions of PCI DSS, it was stated in the initial discussion section that an annual assessment of your card data environment should be carried out. However, in version 4.0, the Council has incorporated this requirement into the section 12 requirements matrix and made it mandatory for merchants to perform a documented scoping exercise each year, as well as after any significant changes to the in-scope environment (such as changes to people, systems, and processes). This requirement is now trackable and effective immediately.
12.5.2.1
Service providers will need to perform this scoping exercise at least every six months and also after any changes to the way the company is organized.
12.6.2
Organizations should ensure that staff receive formal security awareness training. They will need to document and update it at least once a year, as well as when new threats and vulnerabilities that may affect their CDE security arise. Staff need to understand the part they play in protecting cardholder data.
12.6.3.1
Your security training program needs to address the threats and vulnerabilities, including open source vulnerabilities, that affect your environment in particular, as well as the acceptable use of end-user technologies. For example, if you experience a lot of magecart attacks, then your training needs to address this, and it should be reviewed and updated annually
12.10.7
Incident response procedures will need to be put in motion if a stored Payment Account Number (PAN) is detected somewhere unexpected. This means you will always need to be watching out for processes that store PANs outside expected boundaries. You should periodically review processes that deal with card data and use a good data discovery tool.
How Reflectiz can help you stay compliant with PCI-DSS
With these PCI DSS best practices set to become requirements within a matter of months, now is the time to make sure that your organization is fully compliant with them, and the easiest way to do that is to use Reflectiz. The all-in-one platform alerts you to client-side risks such as JavaScript tampering, web skimming attacks, keylogging, or malicious code injection. It maintains a comprehensive list of all third- and fourth-party scripts with descriptions of why they are necessary and assures the integrity of all scripts and apps working in the background on your website.
Reflectiz makes compliance with the new regulations effortless by utilizing authentication scanning to detect internal vulnerabilities. The outcomes are ranked clearly, arranged from low risk to critical to help you prioritize your responses. Any unauthorized changes, including those from trusted domains or applications, are immediately flagged, and your security teams are notified. Additionally, a defensive baseline can be established to define what constitutes “unusual” based on your specific business context.
While PCI DSS may only focus on payment pages, we provide comprehensive coverage for your entire website, including login pages and post-authentication scans. And Reflectiz is completely unobtrusive, demonstrating value in just hours, and without the need to install a single line of code.
As well as helping you to make the listed changes to PCI DSS best practices, Reflectiz can also generate compliance reports for audits by the PCI’s Quality Security Assessor (QSA), which you may recall applies to Level 1 organizations. You can explore the compliance checklist on the Reflectiz website here and also learn more about the changes coming with PCI DSS v4.0 here.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!