How To Build A Successful Continuous Threat Exposure Management Program

Cybersecurity threats continue to increase in complexity and frequency, making it more important than ever to have a solid defense strategy in place. A continuous threat exposure management (CTEM) program is an essential component of any cybersecurity strategy, as it provides ongoing monitoring and response to potential threats.
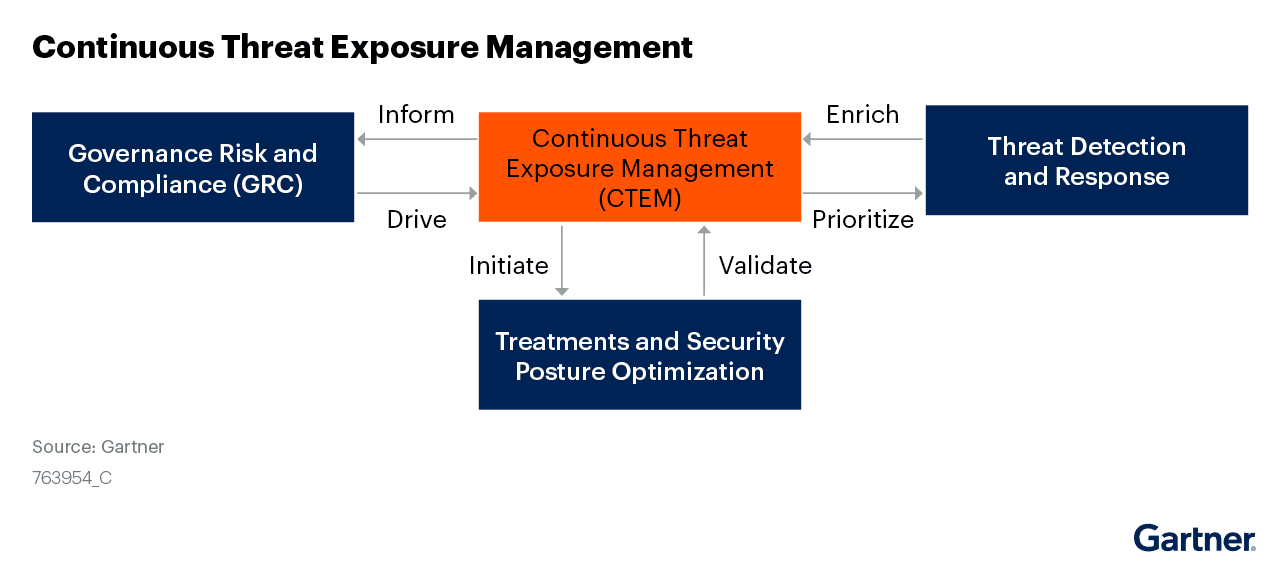
What is Continuous Threat Exposure Management?
Continuous threat exposure management is a process of continuously identifying, analyzing, and mitigating security risks to protect critical assets from cyber-attacks and data breaches. It involves ongoing monitoring and assessment of threats, vulnerabilities, and risks to ensure that businesses can proactively respond to security incidents. By implementing a continuous threat exposure management program, businesses can reduce the likelihood of successful cyber-attacks and data breaches, comply with industry regulations, improve incident response, and maintain business continuity. It is a critical component of any organization’s overall security strategy and is essential in today’s rapidly evolving threat landscape.
The importance of building a successful continuous threat exposure management program
A successful continuous threat exposure management program is crucial for businesses that want to safeguard their critical assets, prevent cyber-attacks and data breaches, and maintain their brand reputation. Here are some of the key reasons why building a successful program is important:
Proactive Risk Mitigation
A successful program enables businesses to proactively identify and mitigate security risks, reducing the likelihood of successful cyber-attacks and data breaches. This can help to prevent significant financial losses, reputational damage, and legal liabilities.
Enhanced Compliance
A continuous threat exposure program can help businesses comply with industry-specific regulations and data privacy laws. Regular threat exposure assessments can help identify areas where improvements are needed to meet regulatory requirements, ensuring that businesses remain in compliance with relevant standards.
Improved Incident Response
A well-designed program can improve a business’s ability to respond to security incidents. By continually monitoring and assessing threats, businesses can quickly identify and respond to incidents, minimizing the damage caused by a cyber-attack or data breach.
Improved Business Continuity
A successful program can help businesses maintain their operations during a security incident. By identifying and mitigating threats proactively, businesses can reduce the impact of an incident, ensuring that operations can continue with minimal disruption.
Overall, a successful program is essential for businesses that want to maintain the security and integrity of their critical assets, comply with regulations, and protect their brand reputation. By investing in a robust program, businesses can minimize the risk of cyber-attacks and data breaches, and ensure that they are well-prepared to respond to security incidents when they occur.
A Step by Step Guide
Step 1: Identify Your Assets
The first step in building a continuous threat exposure management program is to identify your assets. This includes not only your physical devices but also your data, applications, and networks. Once you have identified all of your assets, you can start to prioritize them based on their importance and the level of risk they present.

Step 2: Conduct a Risk Assessment
The next step is to conduct a risk assessment. This will help you to identify potential vulnerabilities and threats to your assets. It’s important to conduct a thorough risk assessment, including both internal and external threats. Once you have identified the risks, you can start to prioritize them based on their potential impact and likelihood.
Step 3: Establish a Monitoring Strategy
The next step is to establish a monitoring strategy. This should include continuous monitoring of all of your assets, including your networks, applications, and data. You should also have a plan in place for monitoring external threats, such as malware and phishing attacks.
Step 4: Implement Security Controls
Once you have identified your assets, conducted a risk assessment, and established a monitoring strategy, it’s time to implement security controls. This may include firewalls, intrusion detection systems, and access controls. It’s important to ensure that your security controls are regularly updated and tested to ensure that they are effective.
Step 5: Establish Incident Response Procedures
In the event of a security breach, it’s important to have established incident response procedures in place. This should include a clear plan for detecting, responding to, and containing any security incidents. It’s also important to have a communication plan in place to keep all stakeholders informed.
Step 6: Conduct Regular Audits
Regular audits are an essential component of any continuous threat exposure management program. This includes both internal and external audits. Regular audits can help to identify potential vulnerabilities and ensure that your security controls are effective.
Step 7: Train Your Employees
Finally, it’s important to train your employees on cybersecurity best practices. This should include training on how to identify potential threats, how to respond to security incidents, and how to use your security controls effectively. Regular training can help to ensure that your employees are aware of potential threats and are able to take appropriate action.
Building a successful continuous threat exposure management program with Reflectiz
Now that we have discussed the key steps of a successful continuous threat exposure management program, let’s dive into how Reflectiz can help you achieve it.
About Reflectiz
Reflectiz is a cutting-edge web security platform that provides complete visibility and control over third-party components, including iFrames, on your website. The Reflectiz platform enables continuous monitoring and analysis of all third-party scripts and resources used on your website to ensure that they are secure and compliant with your organization’s security policies.
Continuous Web Threat Management
With Reflectiz, you can detect and mitigate any security risks and compliance issues posed by third-party components, including tracking pixels, web-skimming attacks, open source vulnerabilities, and more. Our platform leverages advanced AI and machine learning algorithms to automatically detect and categorize all third-party components, analyze their behavior, and provide actionable insights and recommendations for remediation.
Reflectiz provides a user-friendly dashboard that allows you to monitor all your web assets in one place, giving you complete visibility into your web environment. You can easily track your website’s risk exposure, identify potential vulnerabilities, and take action to mitigate them.
Moreover, Reflectiz supports integration with leading ticketing systems such as Jira and Splunk, enabling you to seamlessly manage and prioritize security incidents and vulnerabilities.
Reflectiz offers flexible deployment options to meet your organization’s unique needs. You can choose to deploy Reflectiz on-premises or in the cloud, depending on your organization’s infrastructure and security policies.
Conclusion
In conclusion, building a successful continuous threat exposure management program is critical to protecting your organization’s web assets from security risks and ensuring compliance with industry regulations. With Reflectiz, you can achieve continuous visibility and control over all third-party components on your website, identify potential security risks, and take immediate action to mitigate them. Book a demo today to learn more about how Reflectiz can help you build a successful continuous threat exposure management program.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







