5 Must-Haves for a Vulnerability Assessment in 2022

Opportunistic threat actors are well-versed in seeking out and exploiting security vulnerabilities to achieve their goals. Even in this age of high-profile data breaches and hefty compliance fines, businesses struggle to identify all the vulnerabilities in their environment and fix them.
One recent study of cybersecurity incident data found that unpatched vulnerabilities accounted for 82 percent of successful compromises. The need for effective and repeatable vulnerability assessments has never been greater, but confusion about what a good vulnerability assessment entails keeps companies from addressing their weaknesses. This article explains what vulnerability assessments are, describes how they work, and provides five-must haves for effective vulnerability assessments in 2022.
What is a Vulnerability Assessment?
A vulnerability assessment is a structured process that systematically identifies and prioritizes the vulnerabilities existing in an IT environment. The assessment can cover the systems (devices, servers), infrastructure configurations, and applications. It’s important that the assessment process also reports on how to best remediate or otherwise manage the risks of any detected vulnerabilities.
Vulnerability assessments form an important part of a wider vulnerability management approach that aims to cyclically manage vulnerabilities.
The lifecycle of vulnerability management includes:
- Conducting vulnerability assessments to identify vulnerabilities in a system
- Prioritizing which vulnerabilities to deal with first
- Choosing how to deal with vulnerabilities (accept the risk, harden the system, or apply a security patch/update)
- Adding any findings to a single source of truth for effective vulnerability management to ensure the multiple teams involved with the process are on the same page.
How security Vulnerability Assessments work?
You can break down vulnerability assessments into four different types depending on the information system being tested for vulnerabilities. These types include:
- Host assessments that look at system-level vulnerabilities in systems, such as production servers and workstations.
- Network assessments that examine your company’s network infrastructure (including cloud environments) for vulnerabilities that could let threat actors inside.
- Application assessments that look for vulnerabilities in the source code of apps (including any third-party code upon which an app depends).
- Database assessments that specifically inspect database applications and data pipelines for security vulnerabilities.
Vulnerability assessments sometimes get confused with penetration tests or bug bounty, but they are not the same. In a penetration test, an expert ethical hacker tries to get inside your environment and access critical resources, usually by exploiting a vulnerability. Vulnerability assessments attempt to uncover as many weaknesses as possible in a system or environment and provide remediation measures. You can think of a pen test as a deep test, but it doesn’t go as wide as a vulnerability assessment in finding all potentially exploitable weaknesses.
5 must-haves for your vulnerability assessment in 2022
While you could write a book on a vulnerability assessment strategy, the following five must-haves give you a useful foundation upon which you can detect and patch the most threatening weaknesses that malicious actors are likely to exploit.
1. A comprehensive initial assessment
A comprehensive initial assessment sets the groundwork for the entire assessment process. Pivotal at this stage is an asset discovery process that identifies every asset you want to scan.
The initial discovery of assets to scan for vulnerabilities poses a major challenge to effective vulnerability assessments. Many businesses lack sufficient visibility into their hybrid, multi-cloud infrastructure, which may well include cloud systems spun up by development teams without central IT’s knowledge.
Furthermore, modern websites and web apps rely on a complex interplay of in-house and third-party resources. A typical eCommerce website loads resources from payment providers and marketing solutions, each of which could contain vulnerabilities.
You’ve got to get an accurate inventory of web apps, third-party resources, endpoint devices, and other assets in your environment. Ideally, your chosen toolkit will automate this process.
Then, factor in the strategic elements that dictate your company’s risk tolerance level for various assets or classes of assets. Customer-facing applications, such as banking apps, or Internet-facing assets, both should be prioritized for assessment. There may well also be assets that you can forgo assessing for vulnerabilities or at least schedule assessments on a less frequent basis.
2. Support from automated scanners
A vulnerability scan helps you identify security weaknesses in computer systems, networks, and applications, which is why automated vulnerability scanners play a central role in any modern security vulnerability assessment. These tools automatically identify known security weaknesses in code (including libraries, frameworks, apps), ports, and operating systems running on devices.
For certain heavily regulated industries, it’s important not to neglect the importance of compliance scans. Consider how eCommerce companies need to comply with PCI DSS if they collect, store, or process credit and debit card information. These businesses will need a vulnerability scanner that performs compliance checks for vulnerabilities that put them at risk of non-compliance.
Examples of automated scanners include:
- Nessus, which scans for over 59,000 vulnerabilities
- Nmap, a network scanner that identifies hosts, services, operating systems, and open ports on a network and works well as a lightweight vulnerability scanner
- OpenVAS, an open-source code vulnerability scanner
Selecting the right scanners for your business should factor in whether you want open-source or paid tools and the type of assets the solution works on (e.g. can the tool scan your cloud environment for vulnerabilities?)
You’ll possibly need two to three different solutions to cover all kinds of vulnerabilities; a tool that neglects an important area or category of asset then leaves gaps in your assessment. If the tools included in your assessment strategy can’t find a vulnerability, you can be sure actors with malicious goals will find them regardless.
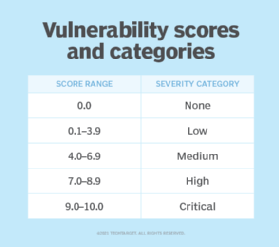
3. A ranking system of security weaknesses
One common problem in vulnerability assessments is that security teams get presented with a list of hundreds or even thousands of vulnerabilities and work through them from there. This can lead to a feeling of being overwhelmed and fatigued from sifting through vulnerabilities without any system that properly defines their importance or severity.
The scanning solutions you select will likely include a severity rating for detected vulnerabilities and help to prioritize them. Usually, the basis for these rankings will be the common vulnerability scoring system (CVSS). However, some additional context in the form of knowledge about the scanned asset, your company’s individual risk appetite, and the overall threat landscape can also inform your ranking system.
For example, vulnerabilities with publicly available exploits should take precedence for remediation because they offer low-hanging fruit to threat actors. Similarly, a DDoS vulnerability or weak content security policies on an eCommerce site might cause a bigger existential threat because if the site is down, there is no revenue.
4. A practical plan for responding to threats
Ultimately, vulnerability assessments tie in with a company’s overarching approach to cyber risk management. Therefore, it’s important to use the clarity and understanding gleaned about weaknesses in your environment and use this to create an actionable threat response plan.
The vulnerabilities enumerated during any automated scans can guide plans in responding to threats that target those vulnerabilities or the systems on which they’re found. Threat response includes both preventative methods (e.g. removing vulnerable third-party web app components) and remediation strategies outlining what to do and who should be involved if prevention fails.
5. A strong vulnerability assessment report
A strong vulnerability assessment report forms the basis from which security teams can efficiently and thoroughly address vulnerabilities, whether through directly patching them, making a configuration change, or otherwise alleviating their threat. Like any other kind of report, it should be clear and concise so that no time is wasted in trying to understand its content and findings.
A good vulnerability assessment report includes information such as an executive summary that presents key findings without overwhelming readers, graphics that enumerate the vulnerabilities, and an overview of the tools and methods used during the assessment. The main body of the report is a results section with a description of each vulnerability, its importance/severity, potential consequences of exploitation, and remediation/mitigation recommendations.
The next step: Protect yourself
You can’t overlook regular vulnerability assessments if you want to protect your company’s sensitive data, apps, and systems from being breached. The next step is to protect your company by incorporating these must-haves into your security vulnerability assessment strategy.
A final reminder is not to neglect the crucial role that third-party vulnerabilities can play in putting websites and applications at risk in today’s complex IT ecosystems. Since enumerating and uncovering these risks can be difficult, turn to dedicated solutions that can map out a digital asset inventory for websites or web apps. Reflectiz can identify all third-party activity and inform website owners about potential compliance issues and vulnerabilities. Learn more.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!