A Complete Review of the OWASP Top Ten for 2022

You’ve probably heard of the OWASP Top Ten – a document first released in 2003 to promote awareness about prominent cybersecurity risks in web applications. In today’s software-led world, technology decision-makers need a solid understanding of these risks and associated vulnerabilities to help make decisions about security practices, tools, and processes to mitigate risks to their companies’ web apps.
The actual OWASP Top Ten document is primarily written for developers, which means it can get heavy on technical details and muddy the waters for strategic decision-making. This blog aims to review the OWASP Top 10 focusing on what each one means in practical terms, the potential business consequences, and actionable mitigation tips.
OWASP Top Ten: What is it all about?
The Open Web Application Security Project (OWASP) is a nonprofit foundation that aims to improve software security by publishing industry standards, articles, tools, and documents. An example of the kind of tools it provides is the OWASP Risk Assessment Framework, which combines static application security testing and risk assessment tools.
Every three to four years, OWASP updates its list of top ten application security risks in light of prevailing application security dynamics and the overall threat landscape. The top ten are ranked in order of risk level.
The methodology uses a combination of data-driven analysis and industry surveys to establish a list of the ten most significant application security vulnerabilities:
- The data side of things gathers information from over 200,000 organizations about web application vulnerabilities found in various processes and uses this information to identify eight of the top ten critical security risks.
- The remaining two risks are gleaned from surveying industry professionals and asking them to rank the most important web app security risks.
The most recent OWASP Top 10 update from 2021 carries over to 2022. The 2021 update adds three new categories of risk to the previous update in 2017, along with some consolidation and re-naming.
Top 10 Vulnerabilities for 2022
Let’s now look at the current OWASP Top Ten through the lens of helping to inform your strategic security and technology decisions.
1. Broken Access Control
Access controls are critical for securing applications against unauthorized access to data and resources. Broken access controls can lead to data compromise, obtaining permissions beyond what’s intended for standard users, or account takeover attacks where outsiders hijack user accounts and initiate fraudulent transactions.
This vulnerability jumped from 5th position in 2017 to 1st in 2021, reflecting that it was found in 94% of tested applications. Common vulnerabilities in this risk category include application logic faults that bypass access control checks by allowing users to change parameter values or force browse to certain URLs.
From a decision-making perspective, it’s critical to emphasize the importance of shifting security left in the development cycle. Access controls are harder to implement later, so communicate the importance of implementing proper access controls, such as denying requests by default and rate limiting APIs early on in web app development.
2. Cryptographic Failures
Cryptographic failures refer to either a bad implementation of encryption or a complete lack of encryption. The major consequence of a cryptographic failure is that you can potentially expose sensitive data. The exposure of sensitive data can pose compliance, reputational, or competitive business risks depending on what information is not adequately protected by encryption.
With the average data breach cost at an all-time high of $4.35 million in 2022, businesses can’t afford to slip up with cryptography.
Critical to preventing cryptographic failures is first classifying the data that any web app processes, stores, or transmits. Then, you can identify the sensitive data assets and ensure they’re encrypted both at rest and in transit. A modern encryption solution that uses up-to-date and strong standard algorithms centralizes encryption and encryption key configuration, and manages the encryption key lifecycle is a prudent investment.
3. Injection
Injection is a risk category that refers to the ability of threat actors to provide malicious input to web applications that result in the app executing unexpected and unwanted commands. Injection occurs when the app can’t distinguish malicious input from its code. Common injection attacks include SQL injections that insert malicious SQL queries into input fields or JavaScript injections that load malicious code into the client-side of the web app.
Injection attacks can lead to various negative outcomes, including denial of service, privilege elevation, and data breaches. An important strategic element of mitigation is encouraging the use of tools that help to detect injection vulnerabilities in code. Since there are several different injection attacks, you may need more than one tool for thorough testing.
4. Insecure Design
This is an entirely new category for the OWASP Top Ten, focusing broadly on application design and architectural flaws that lead to increased security risks. When an application is inherently designed in an insecure way, even a perfect implementation of security controls and risks can’t compensate for those design weaknesses. Sophisticated threat actors will eventually find and exploit design flaws.
At a high level, one of the most important mitigation tips is to mandate the use of threat modeling for software development teams. Threat modeling should use the structure and data flow inherent to a specific web app to trace out the key technical threats that could exploit the system.
To trace out the threats, try to answer the question, “what can go wrong here?” The STRIDE model is a good place to brainstorm because it focuses on important types of application security threats and controls for preventing them.
5. Security Misconfiguration
This category of risks relates to the security components in an application being incorrectly configured. Misconfigurations are increasingly common due to the cloud being used as a development environment and web apps being built with container images. The infrastructural complexity adds more points at which security misconfigurations can occur.
In the data gathered by OWASP current the Top Ten, there were over 200,000 detected instances of security misconfigurations in web apps. The challenge with mitigating security misconfiguration risks from a strategic standpoint is that they cover the whole application stack and the app’s infrastructure. Individual errors are often at play here, such as opening unnecessary ports, not changing default passwords, or leaving cloud storage buckets open.
A pivotal strategic change is to ensure you have a repeatable process for hardening configurations and a tool or process that automatically audits and verifies those configurations across on-premise and cloud environments.
6. Vulnerable and Outdated Components
Web apps comprise many components or building blocks from external sources (libraries, frameworks, etc.). These components handle both back-end and front-end functionality. When threat actors try to compromise an application, they look at its component parts and attempt to exploit any vulnerabilities. Often, these vulnerabilities come from using out-of-date frameworks or libraries that are easy to exploit.
The overall strategic mitigation here is to ensure an effective patch management strategy is in place. Part of that strategy entails maintaining an inventory of all the components in your apps and the respective versions of those components the app is running. Ideally, you’ll be able to automate the inventory step with a digital inventory solution.
7. Identification and Authentication Failures
Failures in authentication and identity management make applications vulnerable to threat actors masquerading as legitimate users. Some examples of vulnerabilities include not setting validity periods for session IDs, permitting weak passwords that are easy to guess, and not rate limiting login attempts against automated attacks.
The solutions include implementing multi-factor authentication in apps and communicating the importance of complying with recommended password length, complexity, and rotation policies to developers.
8. Software and Data Integrity Failures
This is another new risk category in the OWASP Top Ten, and it’s all about making faulty default assumptions within development pipelines about the integrity of software or data. Since web apps regularly rely on plugins and libraries from external sources, a lack of verification of the integrity of these sources introduces the risk of malicious code, unauthorized access, and compromise.
The main mitigation strategy is ensuring external code or data hasn’t been tampered with by requiring digital signatures.
9. Security Logging and Monitoring Failures
Logging and monitoring help to provide security accountability, visibility into events, incident alerting, and forensics. When there are failures in these capabilities, your company’s ability to detect and respond to application breaches becomes severely compromised. To mitigate, use open source or proprietary tools to correlate logs, implement monitoring and alerting, and create an incident recovery and response strategy using established guidelines, such as NIST 800-61r2.
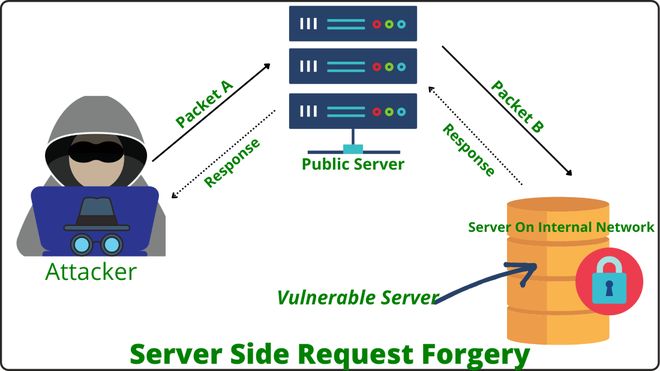
10. Server-Side Request Forgery (SSRF)
SSRF is one of the two OWASP Top Ten risks added based on the community survey rather than data from web apps. Most web apps today require external resources for their functionality, which are usually accessed at URLs. SSRF occurs when hackers can get servers to make requests that they control. The typical vulnerability is that the web application doesn’t validate the user-supplied URL, potentially allowing access to internal services or resources by bypassing access controls.
The strategic concept of defense in depth is important here; multiple controls at the application and network layers can help to prevent SSRF. Client-supplied input data should be validated and sanitized, while network segmentation can also help.
Keep calm but remember to look in all directions
While the OWASP Top Ten is a useful document for improving web application security, it is not the be-all and end-all. There is a strong focus on securing the server-side, but many of today’s attacks focus on the client-side. In other words, it’s important to look in all directions.
A specific blind spot is the third-party scripts often running on websites and web apps. These potentially compromised scripts bypass security tools. The complex modern digital ecosystem requires you to manage a growing inventory of third-party apps and scripts.
Reflectiz provides a complete list of all third- and fourth-party applications running on your website, including their scripts, geolocations, and relationships. The platform also gives you data about potential compliance issues and vulnerabilities that you can remediate before it’s too late. Join Reflectiz FREE version today.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!