What really happens when your accessibility extension is threatening your site?

What really happens when your accessibility extension becomes an immediate suspect that is threatening your site?
In early April a group of cyber researchers issued a security warning regarding a third-party accessibility supplement called “Negishim”. The warning was referring to a series of suspicious actions allegedly made by “Negishim” and to the vague identity of the vendor that offered the supplement. The message between the lines was clear: terror organizations might be using this third-party accessibility extension as a spying tool.
The “Negishim” Red flag
Besides functioning as an accessibility component, “Negishim” was also monitoring users’ digital fingerprints. This action and the fact that the identity of the “Negishim” operators remained unknown, were indeed alarming. A red flag was raised. Since many Israeli sites have already implemented “Negishim”, the recommendation was simple: “Remove!”
Is it a legitimate data collection and who’s behind it?
“Negishim” had a dual problem. First, there was an entity that provided the accessibility tools: it wasn’t an identified entity and it did not provide contact information. The second problem was the data collection. It did seem a bit alarming that an unknown Israeli entity allows any site to use a third-party code that grants permission to do everything on the site. Thanks to our cooperation with the National CERT, we managed to clear the Negishim from suspicion and make sure its operators are legitimate. However, we still wanted to check if information was taken, and if so – what data was taken.
How it works?
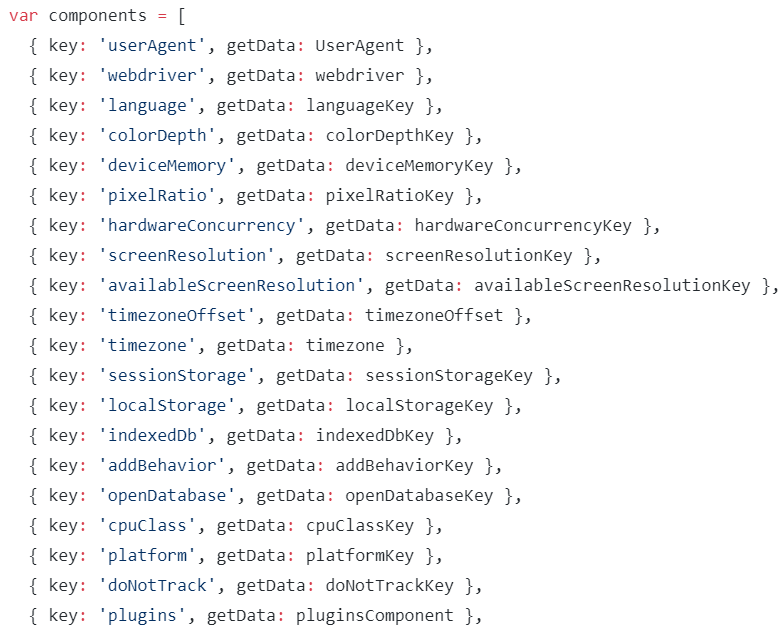
“Negishim” is an accessibility tool. Its modus operandi is generated to make it possible to adapt the site to accessibility laws. However, behind the scenes this tool uses a library named fingerprint2. For those of you who are interested, this is an open-source library located on GitHub under the following address: https://github.com/Valve/fingerprintjs2. It is important to note here that this is not a malicious source, but a perfectly valid library. One that runs multiple tests on users’ browsers simply to identify them.
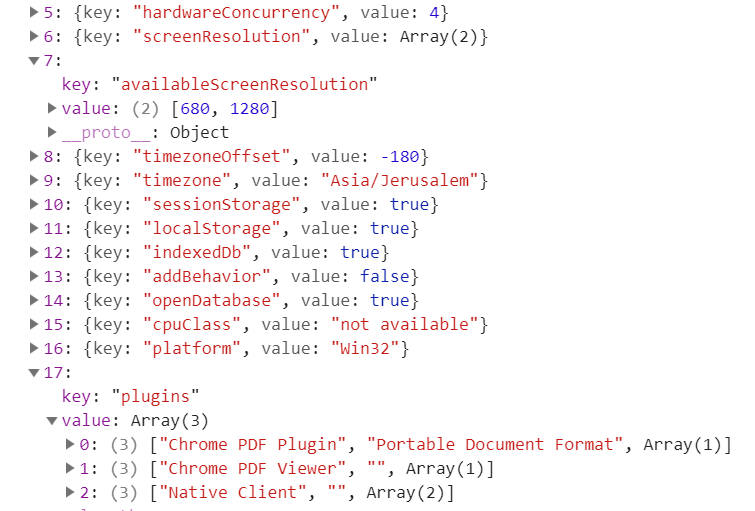
Indeed, this tool was able to gather large chunks of information about the end-user’s computer and browser. This action is generated in accordance to the available options provided in the browser. The purpose of it, among other things, is to assist widely used accessibility components to do a better job.
Technology through the looking glass
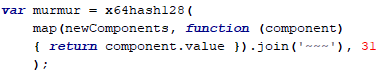
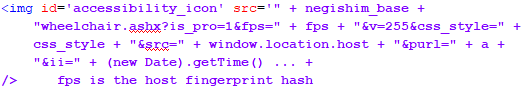
On a deeper overview, it seems that although large amounts of data were collected, the only piece of information that has been delivered back to “Negishim” was a general signature (HASH) of all collected components. This procedure was performed by the following function:
In other words, the actual information was not delivered to an external party. The only component that was essentially sent, was only a “general signature”. One that we believe is designed to identify the user’s computer in a defined way. Please note that this signature will actually change even as a result of any minor change that occurs on the end user’s computer. Moreover, assuming that there is an offensive intention, it will not be possible to identify the user’s computer details through its signature since this is only a general identifier.
Side notes
The “Negishim” warning demonstrates how vulnerable these components might be. Like any third-party, in this case “Negishim” gained permissions to perform manipulations on the site. Third-party code, by definition, is completely controlled by an external vendor or entity. It can undergo changes and modifications, while site administrators, or security personal will know nothing about it. A third-party script can do anything, including fingerprinting, keylogging and data theft. Once it’s there and without proper control, site owners are helpless and exposed.
In our view, no significant user information leaks occurred. Neither did any data that affects user privacy was leaked. In this case, the entity behind the extension was defined as legitimate. Accordingly, and in our professional judgment, the accessibility tool itself is also legitimate. However, it would be totally acceptable if sites choose to prefer not send this information.
We should also note that the fact that the “Negishim” supplement operators chose to send only the HASH and not all the details, was theirs. In the exact same way, that choice could have been altered by their own discretion. Such instance could have easily been done with no supervision or knowledge of the site that Negishim was installed in.
We would like to thank the information security researchers, who examined the case and put the issue on the agenda for further inspection and deeper control.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!