RCE Attacks: Best Practices to Secure Your Web

As a business and website owner, it’s important to understand the potential dangers of RCE (Remote Code Execution) attacks so that you can defend against them or avoid the kind of vulnerabilities that allow them to happen in the first place. In this post, we will look at what an RCE attack is, what it does, and how to avoid becoming a victim.
What is a remote code execution attack?
The term ‘RCE attack’ doesn’t describe one method. Instead, it’s more of an umbrella term for various types of cyber-attacks that lead to the same result: the execution of arbitrary code on a victim’s computer or server. For something to be described as an RCE attack the key ingredient is simply the remote execution of the attacker’s code on someone else’s system.
To achieve this, RCE attackers will begin by looking for vulnerabilities in your defenses, things like buffer overflows, improper input validation, or unpatched software vulnerabilities. They can use a successful RCE attack as a stepping stone to something bigger and more damaging, so once bad actors have exploited one of these entry points to gain a foothold, they may use it to:
- look for further vulnerabilities to exploit.
- cause service disruption.
- launch further attacks.
- move laterally within the system to compromise other resources.
- co-opt your machines to take part in a DDoS attack.
- steal or destroy sensitive data.
- mine cryptocurrencies.
- deploy further malware, including ransomware.
RCE Attacks: Recent examples
The WannaCry ransomware attack made headlines in May 2017 when it crippled the computers of Britain’s National Health Service (NHS), Spain’s telecommunications giant, Telefonica, and Germany’s rail network, Deutsche Bahn. It reduced hundreds of thousands of other computer owners around the world to tears too, by encrypting every file on their infected machines. The attackers demanded bitcoin payments to have them decrypted and those who didn’t pay up lost their systems.
WannaCry exploited an RCE vulnerability to devastating effect. This vulnerability is called MS17-010 and it’s a flaw in the Server Message Block (SMB) protocol (specifically, SMBv1) on Windows operating systems. It used a software exploit called EternalBlue, which was developed by the U.S. National Security Agency (NSA) and later leaked by the Shadow Brokers hacker group. It allows an RCE attacker to send specially crafted packets to a target SMB server, triggering the execution of arbitrary code on the target machine.
The insidious thing about the way it spread was its autonomous nature. Simply being connected to an infected machine was enough to allow the malware to propagate. Once inside a system, it used another tool called DoublePulsar, a backdoor implant to inject and execute the WannaCry ransomware payload on the compromised machines. This RCE attack needlessly affected 230,000 computers in 150 countries: it was entirely avoidable because Microsoft released a patch for the vulnerability in March 2017. The victims were those that didn’t apply it.
The Equifax breach, also from 2017, exposed the financial data of nearly 150 million consumers, and it stemmed from a vulnerability in Apache Struts, an open-source framework for creating web apps.
In February 2016, hackers stole almost $1 billion from the Bangladesh Bank via an RCE attack on the SWIFT banking network.
In May 2024, a severe vulnerability, CVE-2024-37032 (nicknamed ‘Probllama’) was discovered in the popular Ollama AI infrastructure tool (that was patched in version 0.1.34). Ollama simplifies the packaging and deployment of large language models locally on various operating systems. The Probllama flaw took advantage of inadequate input validation, and it could have been exploited by attackers to corrupt arbitrary Ollama system files and eventually launch RCE attacks.
In June 2024 the TellYouThePass ransomware gang targeted a recently patched PHP vulnerability, banking on the idea that not everyone installs security updates straight away. They were reportedly charging victims around $6700 in bitcoin for the decryption key.
In June 2024 the TellYouThePass ransomware gang targeted a recently patched PHP vulnerability, banking on the idea that not everyone installs security updates straight away. They were reportedly charging victims around $6700 in bitcoin for the decryption key.
Anatomy of an RCE attack
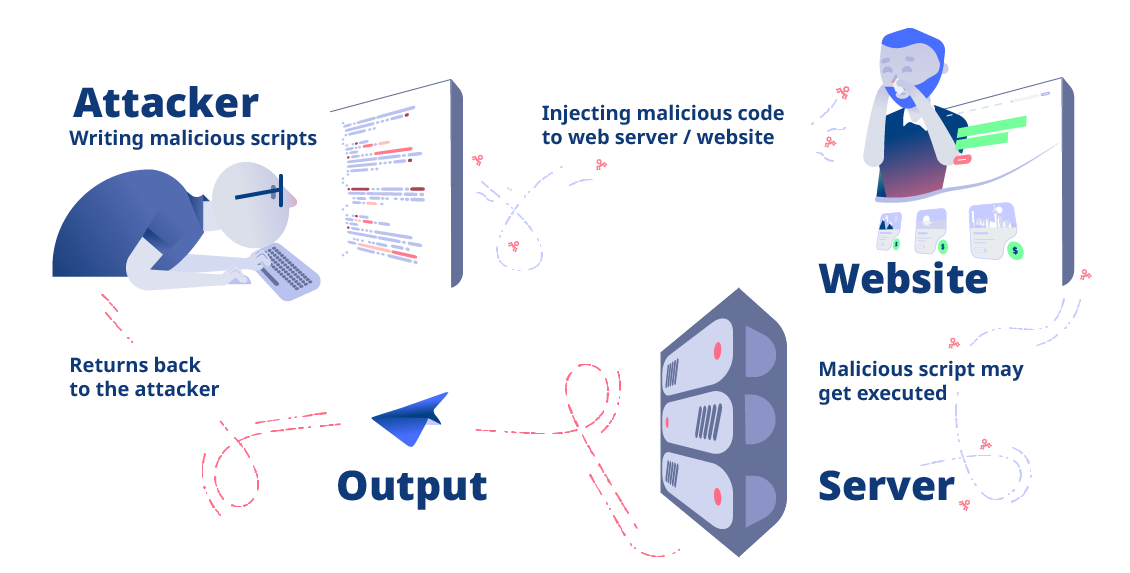
A typical RCE attack can be broken down into several stages. Here’s how a typical RCE attack might unfold:
Reconnaissance
In this initial stage, the attacker gathers information about the target system. This involves:
Identifying the Target: The attacker identifies the target application or service that might be vulnerable. They use techniques such as private research into zero-day vulnerabilities, port scanning, fingerprinting, and enumeration to gather details about the software versions, configurations, and potential vulnerabilities.
Vulnerability Identification
Once the target is identified, the attacker looks for specific vulnerabilities that can be exploited for RCE. Common methods include:
Reviewing Public Vulnerabilities: Checking databases like the National Vulnerability Database (NVD) or CVE (Common Vulnerabilities and Exposures) for known exploits.
Analyzing the Application: Manually or using automated tools to identify weaknesses such as improper input validation, outdated libraries, or misconfigurations.
Crafting the Exploit
After identifying a vulnerability, the attacker crafts an exploit to take advantage of it. This involves:
Creating Malicious Payloads: Developing scripts or payloads that will exploit the identified vulnerability to execute arbitrary code.
Testing the Exploit: Ensuring the exploit works in a controlled environment to avoid detection and increase the chances of success.
Initial Exploitation
The attacker deploys the crafted exploit to the target system. They may use various avenues:
Web Applications: Sending malicious HTTP requests, uploading files, or injecting code through form inputs.
Network Services: Exploiting vulnerabilities in network-facing services or protocols.
Email or Phishing: Trick users into executing malicious attachments or links.
Executing the Payload
Once the exploit is deployed, the payload is executed on the target system. This typically involves:
Gaining Access: The payload runs with the privileges of the exploited service or user, which gets the attacker in.
Establishing Persistence: They are free to create backdoors or other mechanisms that will allow them in again even if the initial vulnerability is patched or the system is rebooted.
Post-Exploitation
Now the attacker performs actions to achieve their objectives. These actions may include:
Privilege Escalation: Attempting to increase their privileges to gain more control over the system.
Data Exfiltration: Stealing sensitive data such as credentials, personal information, or intellectual property.
Deploying Malware: Installing additional malicious software such as ransomware, keyloggers, or bots for future attacks.
Lateral Movement: Moving to other systems within the network to expand control and access more resources.
Covering Tracks
To avoid detection and maintain access, the attacker may:
Log Manipulation: Deleting or altering logs to remove traces of their presence.
Disabling Security Tools: Attempting to disable antivirus, intrusion detection systems (IDS), or other security measures.
Using Tunnels and Proxies: Employing techniques to obfuscate their traffic and make it harder to trace back to them.
Example Scenario
Reconnaissance: The attacker scans a target web server and identifies that it’s running an outdated version of a web application framework.
Vulnerability Identification: The attacker finds a known RCE vulnerability in that version of the framework.
Crafting the Exploit: The attacker creates a payload that exploits the vulnerability to execute a reverse shell (a shell being a program that exposes an operating system’s services to a human user or other programs).
Initial Exploitation: They send a specially crafted HTTP request to the web server.
Executing the Payload: The web server executes the reverse shell which connects back to the attacker’s machine and gives them remote access.
Post-Exploitation: The attacker escalates privileges, exfiltrates sensitive data, and installs a backdoor for future access.
Covering Tracks: The attacker deletes server logs and installs a rootkit to hide their presence.
Here are several common vulnerabilities that can lead to remote code execution (RCE) in web applications:
Deserialization Vulnerabilities
Description: Deserialization vulnerabilities occur when untrusted data is used to populate an object, which can then be manipulated to execute arbitrary code.
Example: If a web application deserializes user input without proper validation or controls, an attacker can craft malicious serialized data to manipulate the deserialization process and execute arbitrary code on the server.
Command Injection
Description: Command injection occurs when user-controllable input is passed to a system command interpreter (e.g., shell commands) without proper sanitization, allowing the attacker to inject and execute arbitrary commands.
Example: A web application that allows users to ping an IP address might use a command like `ping <user_input>`. If the input is not properly sanitized, an attacker could input `127.0.0.1; rm -rf /` to execute a destructive command on the server.
File Upload Vulnerabilities
Description: These occur when an application allows users to upload files without proper validation and controls, leading to the execution of malicious files on the server.
Example: An attacker could upload a PHP file disguised as an image. If the server processes this file and allows its execution, the attacker could run arbitrary PHP code on the server. We encountered just such an exploit involving JavaScript hidden inside a compromised image on a website comments page. You can read our case study on it here.
SQL Injection (with RCE Potential)
Description: This occurs when an application doesn’t handle user input in SQL queries properly, so attackers can manipulate the queries and in some cases execute arbitrary code through database functions.
Example: An attacker could exploit a vulnerable SQL query to execute stored procedures or functions that allow code execution, such as `xp_cmdshell` in Microsoft SQL Server, to run system commands.
Server-Side Template Injection
Description: This happens when user input is embedded in templates without proper sanitization, so attackers can inject and execute code within the template engine.
Example: If a web application uses a templating engine like Twig or Jinja2 and improperly handles user input, an attacker could inject malicious template code that gets executed on the server.
Insecure Deserialization
Description: This occurs when applications deserialize data from untrusted sources without proper validation, leading to code execution.
Example: An attacker could send a crafted serialized object to the application that executes arbitrary code due to the lack of validation once it’s been deserialized.
Remote File Inclusion (RFI)
Description: Remote File Inclusion vulnerabilities occur when an application includes files based on user input without proper validation, allowing attackers to include remote malicious files.
Example: If a PHP application includes a file based on a URL provided by a user, an attacker could specify a URL to a malicious script, leading to its execution on the server.
XML External Entity (XXE) Injection
Description: This happens when XML input containing references to external entities is processed by a weakly configured XML parser, potentially leading to file retrieval, server-side request forgery (SSRF), or code execution.
Example: An attacker could provide an XML payload that references an external entity, causing the server to fetch and parse a malicious DTD, leading to arbitrary code execution.
Buffer Overflow
Description: Buffer overflow vulnerabilities occur when an application writes more data to a buffer than it can hold, potentially overwriting adjacent memory and leading to arbitrary code execution.
Example: If a web application written in a language like C or C++ improperly handles user input in a way that causes a buffer overflow, an attacker could exploit this to execute arbitrary code.

Detection and prevention tactics
Preventing remote code execution (RCE) vulnerabilities requires a combination of secure coding practices, regular updates, and robust security measures. Here are some best practices for developers to help prevent RCE vulnerabilities in their applications:
Input Validation and Sanitization
Validate Input: Always validate input from all sources (e.g., user inputs, APIs, files) to ensure it conforms to expected formats and types.
Sanitize Input: Remove potentially harmful characters, meaning anything that can be read as code from inputs. For example, use libraries to sanitize SQL inputs, HTML, and other content.
Use Safe APIs
Parameterize Queries: When interacting with databases, use parameterized queries or prepared statements to prevent SQL injection.
Avoid Unsafe Functions: Avoid using functions that execute external code or commands unless necessary. For example, prefer higher-level language constructs over `eval` or `exec`.
Keep Software Updated
This is an obvious point to make, but it bears repeating. You should regularly update your development frameworks, libraries, and tools to the latest versions to protect against known vulnerabilities. You should also have a patch management process in place so that security patches are applied promptly.
Implement the Least Privilege Principle
Minimal Permissions: Run applications and services with the least privileges necessary. Avoid using root or administrator credentials unless required.
Separate Roles: Use role-based access control (RBAC) to limit access to critical functions and data.
Secure Coding Practices
Code Reviews: Conduct regular code reviews and security audits to identify potential vulnerabilities.
Static Analysis Tools: Use static code analysis tools to automatically detect security issues.
Security Training: Educate developers on secure coding practices and common vulnerabilities (e.g., OWASP Top Ten).
Use Security Libraries and Frameworks
Hardened Libraries: Use well-maintained and security-focused libraries and frameworks that offer built-in protection against common vulnerabilities.
Security Features: Take advantage of security features provided by the frameworks, such as output encoding, CSRF protection, and secure session management.
Network Security
Firewalls and WAFs: Use them to filter and monitor incoming traffic.
Secure Communication: Use HTTPS and secure protocols to protect data in transit.
Logging and Monitoring
Detailed Logging: Implement detailed logging of application activities, especially those related to user input and critical operations.
Anomaly Detection: Use monitoring tools to detect and alert you about unusual activities that could indicate an attempted RCE attack.
Use Containerization and Sandboxing
Isolation: Run applications in containers or sandboxes to isolate them from the host system and other applications.
Limit Exposure: Limit the exposure of application components and services to reduce the attack surface.
Regular Security Testing
Penetration Testing: Conduct regular penetration testing to identify and remediate security weaknesses.
Dynamic Analysis: Use dynamic application security testing (DAST) tools to find vulnerabilities in running applications.
How Reflectiz can help
For ultimate peace of mind use Reflectiz to monitor all your websites from one dashboard. Its easy filter and navigation options give you complete oversight of the processes running within your website environments, including all internal and external application scripts and open-source tools. With its always-vigilant active scanning, you can detect and block malicious traffic, stop malicious scripts and significantly cut the risk of an RCE attack compromising your system. Sign up today!
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







