7 Ways to Ensure Supply Chain Security

Not to sound dreadful, but can we all agree that the modern software supply chain is riddled with threats? From cyber and data privacy breaches to the risk of critical IT systems failing and vulnerabilities in third-party technologies, it seems new threats are mushrooming everywhere. It’s no wonder 82% of CIOs believe their software supply chains are vulnerable.
They are most likely right to be worried. Organizations must prioritize supply chain security as a breach in the system can potentially derail their entire operations flow. The same goes for vulnerabilities which lead to unnecessary costs and delayed delivery schedules.
The good news? While threats can’t be eliminated entirely, there are ways of protecting your business from supply chain security risks.
Digital Supply Chain Security?
The software supply chain forms the backbone of modern software development lifecycles. It automates applications and software updates’ building, testing, and deployment. But while this automated process has become a critical business enabler for many (who use it to build and deploy their applications faster), they also tend to run using a large variety of tools and services. You see where we’re going with this? Integrated through automated actions, these external processes and tools can widen the attack surface for software companies and are considered by some to be their highest security risk.
Beyond the development stage, security and risk management teams must partner with other departments to prioritize and manage their supply chain risks. This includes pressuring vendors and suppliers to provide evidence of their standards and best-practice internal security controls (particularly if you share data, infrastructure, or services with them).
Evidence of secure design and engineering practices should also be taken into account, alongside a Bill of Materials (BOMs) for products, services, and components, which includes all logic-bearing hardware, firmware, and software. Finally, it is good practice to look for evidence of their vulnerability disclosures and management programs and ensure that they establish anti-tamper controls and provenance efforts, such as only buying from original equipment manufacturers (OEMs) or licensed resellers.
Adherence to these best practices is becoming increasingly mandatory. But although it is desirable to ascertain a partner’s susceptibility to attacks, current approaches are only partially successful in identifying and remediating digital supply chain attacks.
The good news is that there are actions you can take towards that goal. They include: creating partnerships with your key IT, procurement, supply chain, operations, system owners, and product development stakeholders – and perhaps developing a joint governance model.
Additionally, aim to create an inventory of major ICT supply chain partners to classify them as high/medium/low risk based on business or mission criticality. For those rated high risk, security and risk management leaders should make it a requirement to provide evidence of security best practices.
Lastly, aim to establish detection and resilience capabilities for any mission-critical supply chain partners. This should include a cyber incidence response plan, downtime procedures, and a continuity of operations plan so that critical functions and operations can continue if the systems of a critical digital supplier are disrupted.
Further, we recommend using an automated tool to help you adopt a proactive and preventative approach to vulnerability scanning and quickly identify risk areas, particularly in eCommerce platforms, web applications, and third-party software.
So, let’s get to business: how do you start protecting your company from software supply chain risks? Here are four suggestions to get you started:
1. Start with secure software Development
Computer security author Robert C. Seacord illustrates an interesting problem in which most businesses find themselves. There’s no need to develop proprietary software for your entire software stack when building software from commercial and open-source components can dramatically reduce the cost and time needed to develop your own. This being said, software developers are left wanting to secure their supply chains but don’t know how. Software consumers want to understand and limit their exposure to supply chain attacks but have no practical way of doing so. Seacord rightly explains that the key to solving this problem is understanding what software you are using and what its quality attributes are.
Equally important is understanding that the quality and security of your application and software releases depend on a broad approach to code security. This can include Static Application Security Test, Dynamic Application Scanning Tools, secret scanning, Infrastructure as Code security, container security, and software composition analysis. Running this full set of scans as part of your software supply chain process can help you improve your code and application quality throughout development.
2. Create a vulnerability management program for dependencies
Like the above, you can protect your code and dependencies by establishing an internal quality and security management program. This can help tackle some of the most common (and most feared) risks in working with the code you write coupled with the code you depend on: from using dependencies with security vulnerabilities that attackers can exploit (or introducing vulnerabilities to your own code) to leaking authentication credentials or a token that attackers could use to access your resources. Not only are these risks threatening your resources and projects, but they are also passed on to anyone using a package you create.
When considering a vulnerability management program for dependencies to tackle those risks, a good starting point is the following best practices for securing code in your supply chain:
- Establish processes to ensure that you create an inventory of your dependencies. (Hint: Use automated solutions for this)
- Continuously monitor dependencies for security vulnerabilities.
- Assess the impact of that vulnerability on your code
- Based on this information, design protocols that can help you decide what action to take when vulnerabilities are detected.
An application dependency tree illustrated by Julien Danjou, who says: “Dependencies are a nightmare for many people. (…) but something you cannot, in practice, get rid of – unless you’re incredibly rich and talented and can live without the code of others.” Source: julien.danjou.info
3. Choose open-source code and development repositories wisely
You’ve probably heard of GitHub or BitBucket, but do you know how a code repository is defined and how to choose the right one for your organization? A source-code repository is an archive containing the code and its hosting facility where you can have your project’s technical documentation, web pages, snippets, patches, and more – and all this can be accessible publicly (open-source) or privately.
A source code repository has multiple functionalities; it can keep your code safe and offer version control options to ensure changes to your code are tracked (and you know who did something to your code). It can also simplify the process of unifying changes made by multiple developers working collaboratively on the same projects, modules, and code lines, promoting teamwork and helping prepare code for release in production.
So when looking for a code repository, start by establishing your goals. What do you want to accomplish with it? Your priority may be version control for your project to help fix coding mistakes. Or you may be looking to improve a sense of community within your developers. Even if there are tricks you may not want to share, committing to a joint project such as submitting a bug fix to your favorite framework is in everyone’s interest.
Finally, you may want to select a code repository to function as a digital portfolio. This may be particularly appealing to developers who’ve leveraged a GitHub repository to spice up their CV – for many, providing a link to your code repo is worth more than talking about your excellent academic background.
Once you’ve established your goals, keep the following questions in mind to select a code repository that will work harder for you:
- What version control systems are supported? If the repository hosting service isn’t compatible with the version control system used in your projects, you may have difficulty using it.
- What’s your team size? Having multiple developers involved in a project means you’ll need to consider the level of permissions you can assign each of them. If you’re a solo developer, this is not a relevant consideration, meaning you have a more comprehensive selection of options.
- What does your release schedule look like? Depending on how often you plan to release updates to the code, you may want to choose a repository management system with CI/CD (particularly if you plan to release small things regularly). The aim is to simplify your daily routine.
- What kinds of files are you working with? Some software solutions are designed to simplify the working process supporting large files such as 3D graphics and audio files. If you work with large file types, this is worth considering.
- How can you keep your options open? You’ll need to integrate your source code repository with other third-party solutions and automation tools to help streamline your processes. Selecting repositories that are easy to integrate with these features can open up new avenues for your development experience moving forward.
4. Beware of dependency confusion attacks
Most software today is assembled from multiple open-source packages and components instead of written from scratch. While the advantages of relying on the work of thousands of developers are also clear, we should never forget that dependencies themselves have dependencies, and the chain of trust stretches backward into infinity – this leads to a tangled web of dependencies that quickly becomes very difficult to follow.
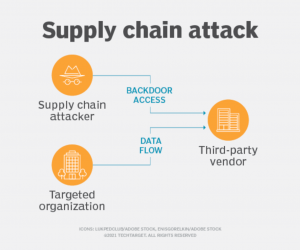
The result, in cybersecurity terms, is a threat category referred to as a dependency chain–of-trust abuse or dependency confusion attack. To perform such an attack, the malicious actor spots internal-looking dependencies in a repository’s Software Bill of Materials, then creates a malicious package by the same name to be pushed and reside on a default public registry. Finally, the attacker leverages a fail-open behavior management system: looking for the identified dependencies in case it is missing from the environment in which the code is trying to execute. Results in failure on the first-order registry will typically query the next-order registry, which usually defaults to a public one – this “confusion” in the process (hence the name!) is all the attacker needs. When those mishaps happen, the malicious code is silently planted.
To prevent this from happening to you, educate your developers on this risk. Since this occurs silently and voluntarily (by default on a dependency lookup), many might be unaware. Secondly, designate specific registry source and scope in the Bill of Materials and scan for dependency name leakages. You may want to use an open-source toolkit, such as a dependency combobulator.
5. Provide end-to-end security and privacy protection of customer data through Identity and Access Management (IAM)
One way to apply a zero-trust approach to your organization’s supply chain is by providing end-to-end security and privacy protection of customer data and other digital ecosystem resources. This can be done in parallel with creating a cohesive strategy for all external users (including consumers, business customers, and partners) by aligning IAM priorities with both business and IT priorities–key to delivering an omnichannel experience and unifying customer profile data.
With businesses relying increasingly on digital interactions with their customers to keep their operations running, the bar continues to rise on what a great total user experience means. Gartner estimates that by 2024, organizations that aim higher in this regard will outperform competitors by 25% in satisfaction metrics for both customer and employee experience. Meanwhile, improving user experience for all users through IAM practices will be essential for digital businesses to thrive securely.
6. Implement an effective supply chain monitoring process aimed at protecting your broader ecosystem–not just your environment
As supply chains become increasingly global and fragmented, supply chain management becomes increasingly complex. The traditional supply chain takes a linear and reactive approach to manage risks, whereby the functioning of the chain depends on specific predefined workflows. Historically, transactions from legacy systems governed how the chain functioned rather than real-time conditions–and visibility within a traditional supply chain was limited by the lack of integration between the different systems that made up the chain.
On the other hand, the digital supply chain uses a network approach: it applies digital technologies throughout for a more integrated, dynamic, and predictive supply chain that can spot problems earlier and proactively respond to disruptions based on real-time conditions. In this sense, connectivity is critical for visibility across the supply chain. But of course, this optimization made possible by an ecosystem of modern technologies also increases the threat surface for cyber attacks. This is why supply chain planning must include security as a critical consideration, including the following best practices to help better manage your supply chain cybersecurity risks:
- Include security requirements in supply chain contracts and documents.
- Enforce basic security standards throughout, from changing default passwords for devices to limiting user access and encrypting communication.
- Establish strong due diligence requirements to benchmark against when researching vendors to ensure they can adequately meet your cybersecurity requirements. This includes asking vendors about their physical security measures, access controls, malware prevention and detection measures, and secure coding practices.
- Consider adopting an automated vendor risk management solution that continually monitors the risk exposure from different vendors in the software supply chain.
- Aim to strengthen your security education, training, and awareness programs to improve human awareness of cyber risks throughout your supply chain–not just within your business.
7. Don’t trust; verify by testing your applications for vulnerabilities
Digitization initiatives, the need to work from home, and requirements for specific software by different departments and business units have all contributed to the growth in commercial software usage by businesses worldwide. Meanwhile, IT departments feel growing pressure to handle their risk exposure. That’s because vulnerabilities in commercial software have become more common with the increased use of open-source components as their building blocks.
Hackers have recognized that they can exploit vulnerabilities in embedded open-source software components to compromise widely used applications. The most secure way to control the security of software used by employees is to test them to assess whether they contain any vulnerabilities in their code and determine how much risk you’re willing to accept for each application you deploy.
Keep in mind that since application providers typically do not share their source code, the only effective way to verify their security is via manual penetration testing, which has its limitations. For starters, manually testing hundreds of applications used across the business is time-consuming, expensive, and labor-intensive. During this time, productivity may decrease, and employee frustration may go up as business units risk being stuck waiting for applications to pass the test and/or for a new and better application to be introduced.
Additionally, the effectiveness of manual pen-testing techniques can be questionable because while it may detect some vulnerabilities, it can also miss some. To avoid these pitfalls, consider automating this process with binary software composition analysis tools to create a software bill of materials (SBOM). Remember to look for tools that do not require access to source code, can guarantee high precision and recall (which will reduce false positives), and perform analysis for open-source and third-party software.
Keep calm and carry on with ongoing website dependency scanning
The rapidly-growing dependency on external code and third-party services begs whether these software supply chain risk measures are enough. Today, websites load numerous third-party resources, such as requests to various payment providers and marketing tracking solutions, on any given webpage.
Even if any one of the third-party providers is vulnerable, it leaves an open window to an attack. And for that reason, today, businesses need to keep a keen eye on their digital inventories, including all their domains and subdomains connected to their ecosystem.
That’s why Reflectiz developed a SaaS solution that uses behavioral analysis to mitigate client-side attacks — especially the ones originating in the users’ browsers – by monitoring all network activities (requests a browser makes to upload a website). This should be part of your third-party risk management strategy to pinpoint all third-party activity on your website and draw a list of all vulnerabilities and potential compliance and regulatory issues you might be facing.
Our fully automated platform can scan your entire website in minutes to help you reliably mitigate risks and monitor different digital services, all without intrusive implementation processes. This way, with continuous monitoring, you can detect changes as they occur with a 360° view of 3rd and 4th-party applications that may be putting your website at risk. To learn more, why not try it for yourself?
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!