What is CTEM? A Complete Overview

The term Continuous Threat Exposure Management (CTEM) was coined by Gartner. In its July 2022 report about implementing this approach it stated that “By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach,” implying that those that don’t will be at considerably greater risk.
But what is it exactly? The first thing to say is that it isn’t a new tool or a new technology. It’s more of a fully joined-up thinking approach to managing cybersecurity in an age when our threat surfaces are growing broader by the day. CTEM is a cybersecurity strategy that involves constantly exposing an organization’s networks, systems, and assets to simulated attacks to identify vulnerabilities and weaknesses. The goal of CTEM is to improve the organization’s overall security posture by identifying and addressing these areas of concern before they can be exploited by real attackers.
CTEM is often implemented through a combination of automated tools and manual testing and may include activities such as penetration testing, vulnerability scanning, and red teaming. By regularly exposing the organization’s assets to simulated attacks, CTEM helps them identify and fix vulnerabilities before they can be exploited by malicious actors.
This is becoming increasingly relevant because of how much more connected organizations are today. Just one example is the rise in remote working. While it’s been a mini-revolution it’s also opened up organizations to new avenues of attack, as remote employees need to be able to safely connect to a company’s critical assets via their own devices.
While enterprises will no doubt have security systems in place, Gartner’s report notes that they, “…fail at reducing their exposure to threats through self-assessment of risks because of unrealistic, siloed and tool-centric approaches. Security and risk management leaders must initiate and mature a continuous threat exposure management program to stay ahead of threats.”
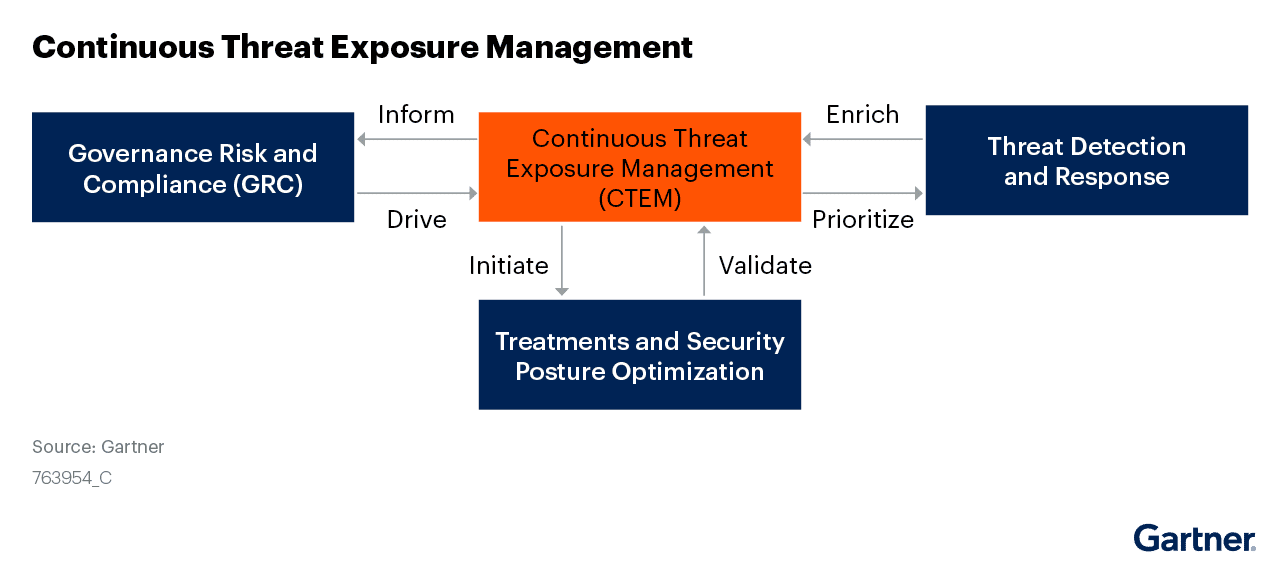
Reflectiz offers a Continuous Web Threat Management solution that represents a significant contribution to the CTEM approach with its specific focus on protecting organizations from the potential vulnerabilities that may arise from using third-party apps on their websites.
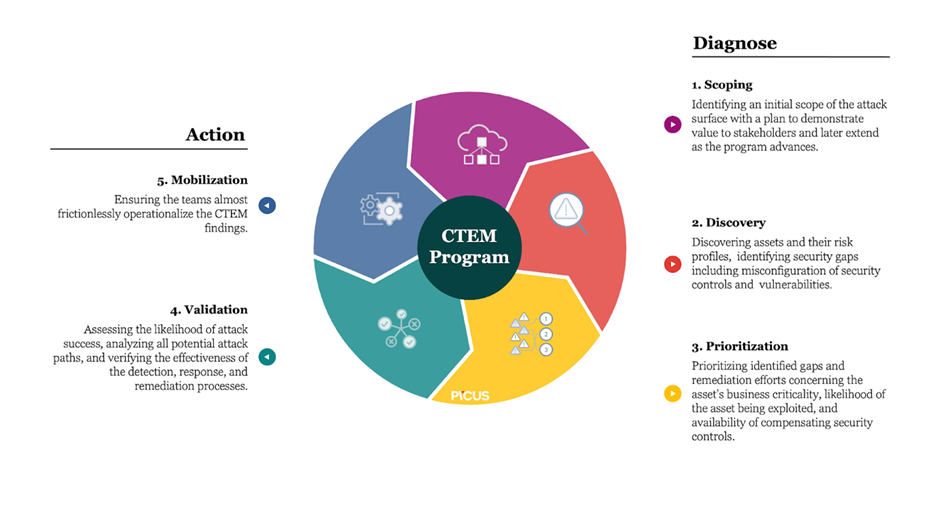
The Five Stages of CTEM
CTEM has five stages, and they look like this:
1. The Scoping Stage
The scoping stage involves defining the scope of the CTEM program, determining which systems and assets will be included, and identifying the stakeholders who will be involved.
During this stage, it is important to conduct a thorough risk assessment to determine which assets are most critical to the organization and therefore require the most urgent attention. This may include physical assets such as buildings and equipment, as well as digital assets such as databases and networks.
Once the assets have been identified, it is then necessary to determine which stakeholders will be involved in the CTEM program. This may include management, IT personnel, security personnel, and other employees who may be affected by potential threats.
Once the scope and stakeholders have been defined, the next step is to develop a plan for managing and mitigating potential threats. This may include implementing security controls such as firewalls, intrusion detection systems, and access controls, as well as setting up processes for identifying and responding to potential threats.
Overall, the scoping stage of CTEM is intended to ensure that the organization has a comprehensive and effective plan in place to find and respond to potential threats. By defining the scope, identifying key assets and stakeholders, and developing a plan for managing and removing threats, organizations can lay the groundwork for effectively protecting themselves against security risks affecting their assets and systems.
2. The Discovery Stage
The discovery stage of CTEM involves actively seeking out and identifying potential vulnerabilities within the organization’s systems and assets.
During this stage, various tools and techniques may be used to scan the organization’s systems and networks to identify possible points of weakness. These may include automated scanners, manual testing, and penetration testing.
It is important to involve a diverse team of experts in the discovery stage, including IT personnel, security personnel, and other employees who may have a unique perspective on potential vulnerabilities. This ensures that all potential threats are identified and evaluated.
When potential vulnerabilities have been located, they are prioritized based on the likelihood of exploitation and the potential damage this could inflict on the organization, so the most important points of weakness can be addressed first.
The discovery stage of CTEM ensures that the organization has a comprehensive and up-to-date understanding of where it is potentially most vulnerable. By actively seeking out and identifying these avenues of attack, organizations can effectively protect themselves against possible threats.
3. The Prioritization Stage
The prioritization stage of CTEM involves evaluating the potential vulnerabilities identified in the discovery stage and addressing them in order of priority, based on how likely they are to be exploited and the potential impact this would have on the organization.
During this stage, it is important to consider a variety of factors when determining the importance of each vulnerability. These may include the potential for damage to the organization’s assets or reputation, the likelihood of successful exploitation, and how difficult it would be to deal with the vulnerability.
After the vulnerabilities have been prioritized, the organization can develop a plan for addressing them. This may include setting up security controls or processes to remove them, conducting regular testing to ensure that the controls are effective, and providing training to employees so that they can better identify and respond to potential threats.
This stage ensures that the organization can address its most critical vulnerabilities first.
4. The Validation Stage
During the validation stage of CTEM, it will be established whether the controls and processes deployed to patch vulnerabilities are achieving the level of protection that they are supposed to. Various tools and techniques may be used to test the effectiveness of the controls and processes, including automated scanners, manual testing, and penetration testing.
As with the discovery stage, it is also important during this stage to include a wide range of experts in the process, such as IT personnel, security personnel, and other employees who may have their own distinct perspectives on potential vulnerabilities.
Once the controls and processes have been successfully validated, the organization can then make any necessary adjustments to ensure that they are effective in protecting against potential threats. This might include updating security controls, setting up new processes, or offering extra training to bring employees up to speed.
The validation stage is important because by regularly testing and confirming that controls and processes are effective, organizations can be sure that their systems are as safe as they can be from possible threats.
5. The Mobilization Stage
The mobilization stage of CTEM involves applying the controls and processes developed during the prioritization and validation stages and using them to effectively manage and defend against possible threats.
During this stage, it is important to ensure that the means are in place to set up and maintain this approach, which may include IT personnel, security personnel, and anyone else involved in the CTEM program.
As well as mobilizing personnel and resources, it is also important to make sure that all stakeholders are aware of the CTEM program and their role in it. Employees may need training on the program, management may need to be made aware of how important it is, and relevant policies and procedures may need to be updated.
The mobilization stage of CTEM ensures that the organization protects itself against potential threats. By mobilizing all necessary personnel and resources and ensuring that all stakeholders are aware of their role in the program, organizations can keep their systems and assets safe from threat actors.
Reflectiz and CTEM
With the help of Reflectiz, you can easily shift your organization into a CTEM program and completely secure your online products from sophisticated cybersecurity attacks. Reflectiz enables complete visibility over your extended threat surface and seamlessly detects potential risks and vulnerabilities in your 1st, 3rd and 4th party components. Book a demo with Reflectiz today and see for yourself how we can make your organization more secure.
CTEM for web
“By 2026, organizations prioritizing their security investments, based on a continuous threat exposure management program, will realize a two-third reduction in breaches” – Gartner
A proactive-approach web solution like Reflectiz offers crucial defense and preemptive measures against evolving web threats. It allows organizations to strengthen their digital environments in a way that goes beyond the capabilities of traditional detection methods, which may face challenges monitoring certain third-party web components like tracking pixels.
In the face of numerous threats and potential financial and reputational risks, it’s crucial to stay alert and take proactive measures to effectively address and mitigate them.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!