The Essential PCI Compliance Checklist

For a limited time only, get free PCI scan and know how ready you are for the v4 requirements.
“There’s no way I’m buying online. Did you hear about that credit card leak?”
It’s ironic that, at the dawn of Internet shopping nearly two decades ago, people were afraid to do so because they suspected shoddy websites. Now, with major retailers all over the Internet, there is fear of credit card details being stolen – just as a wallet might have been swapped, back in the days of brick-and-mortar shopping.
As statistics show, the number of online transactions has steadily grown (given a further boost thanks to the Covid-19 Pandemic) – as did malicious attacks. This boosted the prevalence of Payment Card Industry (PCI) compliance, created to support, nurture and secure the continued incredible growth of digital transactions. But not nearly enough.
Surprisingly, only about 28% of organizations have achieved full PCI compliance. With hacking and phishing scams getting more and more sophisticated, becoming PCI compliant is crucial not only for the security of customer data but also for the future of your business.
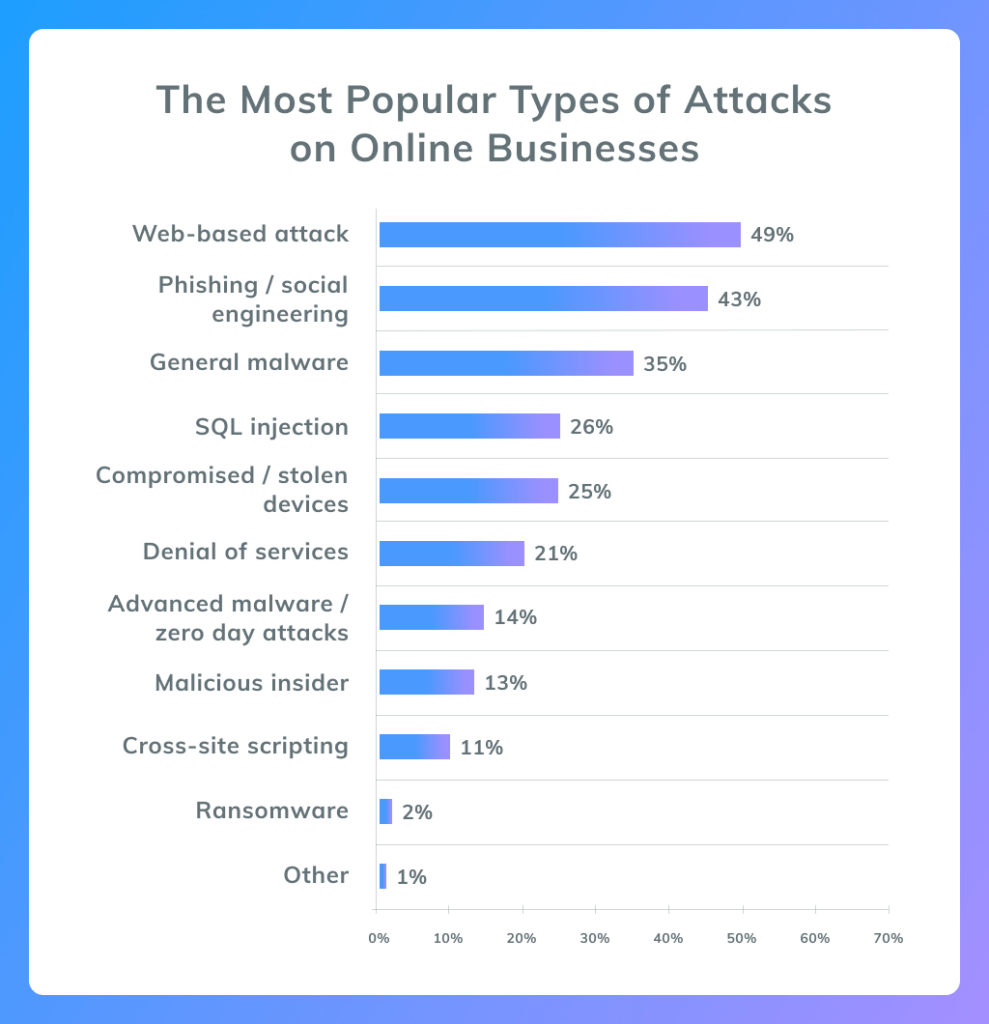
What is PCI Compliance?
PCI Compliance, or, to give it its full name – PCI DSS (Data Security Standard), is the security protocol established with the intention that all companies who process, store, and transmit payment information maintain the highest security measures possible.
PCI compliance standards were set to protect information that online merchants receive and store when they accept online payments. In 2006 the PCI Security Standards Council (PCI SSC) was formed by Visa, American Express, Mastercard, and other international payment services, to drive the adoption of PCI standards. There are dozens of financial institutions and online merchants listed as members, including Amazon, JP Morgan, Wells Fargo, Burger King, Walmart, and more. It provides comprehensive resources and guidelines for organizations and maintains the standards. The PCI SSC has divided the PCI compliance into four levels:
Level 1: Any merchant that processes over 6 million transactions per year
Level 2: Any merchant that processes between 1 million – 6 million transactions per year
Level 3: Any merchant that processes between 20,000 – 1million transactions per year
Level 4: Any merchant that processes up to 20,000 transactions per year per year
To achieve PCI DSS (Data Security Standard) compliance, an online payment or eCommerce retailer must commit to the 12 standardized requirements: You could call this the “PCI compliance checklist.”
The 12 requirements for PCI DSS:
- Install & sustain a firewall to protect cardholder data
- Refrain from using vendor-supplied defaults for passwords and other security specifics
- Protect all stored cardholder data
- Encrypt cardholder data all transmitted on public networks
- Use anti-virus software and keep it updated
- Develop & maintain secure systems and applications
- Restrict access to cardholder data to a need-to-know only basis
- Assign a unique ID to individuals with computer access
- Limit physical access to cardholder data
- Track & monitor all access to network resources and cardholder data
- Frequently test security systems and procedures
- Maintain a documentation policy that addresses information security for all personnel
Adhering to PCI compliance means not only tighter security for your organization as well as cardholder data. It can also lead to more trust from your customers (which in turn can lead to new customers) and build your reputation in the business and payment community, which is a valuable commodity for any organization.
Because PCI compliance is an ongoing process year-round, it can reduce the chances of a security breach or card data theft.
Who should care and why should they care?
The lessons learned are too hard and too costly to ignore. We’ll name a few of them:
- Warner Music Magecart attack, where detailed card information was exposed
- Target – this one is particularly egregious since it had a malware detection tool at its disposal but somehow missed the warnings,
- Roughly 3 million Adobe customers had their credit card details stolen.
The size of your organization doesn’t matter: Businesses using payment processing methods are consistently potential targets, and SMBs can find themselves in the crosshairs as a ‘target practice’ for hackers. And in case you’re wondering – even if your organization uses a third-party payment provider, it does not accept you from PCI compliance.
What being non-PCI-compliant can cost your organization
Let’s look at the cost of being PCI non-compliant: Besides gambling with your customers’ details, not measuring up to PCI compliance standards means that, besides the financial risks you put yourself and your clients at, you’re also subject to possible fines from the PCI Security Standards Council.
Worse, suppose your business suffered a security meltdown (aka ‘breach’) while you weren’t PCI compliant. In that case, your business could be penalized, along with any reimbursements to the clients. In short, you’ll be:
Compromising data of customers, vendors, and financial services; severely damage your reputation and hamper future business ventures; end of business relationships, the rapid decline of shares (if it’s a publicly-traded company), negative PR… and we haven’t even touched yet upon possible lawsuits, insurance claims, financial services fines, and government fines as icing on the cake.
DOWNLOAD THE PCI CHECKLIST HERE
Necessary Steps to Comply with PCI Standards
Remember that cyber security is always a cat-and-mouse game with cybercriminals, so no solution is 100% foolproof. But complying with strict PCI standards does mean that, should the worst befall, if you’d done everything possible on your end, your organization will continue to have the backing of credit card services, banks, or any other financial institutions you partner with.
Speaking of third parties, it is of course important that you know when they receive customer details, and how they secure and use them to help you ensure that your clients’ data hasn’t been stolen or involved in a cyber attack. Keeping an eye beyond your own security perimeters can help you stay a step ahead of groups such as MAGECART, which exploit third-party codes embedded in your website to bypass your security architecture.
That’s why, to tackle this threat and secure your customers through their user journey, we designed a platform to simulate a full user journey, covering all visitors’ actions until the complete checkout phase. This includes an Automated Remote Website Scan and AI-driven analysis to detect anomalies and alert you of suspicious activities.
However, it’s not just about “achieving compliance.” Because that’s like doing the minimum, the real work is to mitigate the risks to your organization, and PCI compliance is your guideline. Some organizations make a mistake because they consider security measures such as PCI compliance as an expense, whereas it should be considered an investment.
There are several steps that your organization must regularly follow to stem the risks of PCI breach:
Risk assessment:
- Reviewing your IT assets and analyzing payment processing procedures
- Identifying existing and potential vulnerabilities from outside
- Searching for unusual activity patterns within the IT department
- You must install software updates ASAP, and antivirus utilities should be constantly updated
Reporting
Compiling and submitting reports to the card payment companies and banks that your organization is affiliated with. This is to make sure that you’re keeping up with the PCI standards. The higher the frequency of reports, the better. These reports should cover just about every policy but the kitchen sink: Firewall, antivirus, information security, system configuration, password policy, physical security, cardholder data policy, etc. When your organization is audited by a PCI Security Standards Council QSA (Quality Security Assessor), to ensure that the business meets the PCI DSS standards, they’ll want to see those. So it’s a good idea to have every conceivable report within reach.
Minimize data access
to authorized personnel only, based on the data relevant to their position. This minimizes the risk of sensitive data leaking through staff without reason to access the information. Multi-Factor Authentication (MFA), strong passwords, and web application firewalls are additional layers, plus frequent security reports.
Separate cardholder data from company data. This allows for tighter security and prevents unnecessary mix-ups of data.
Who oversees PCI compliance?
The person in charge should be a PCI compliance manager. Experienced in data protection & cybersecurity, this person reports to the company’s compliance manager and/or the company’s CISO (Chief Information Security Officer).
So why don’t all companies just become PCI compliant? Take a look at the stats below:
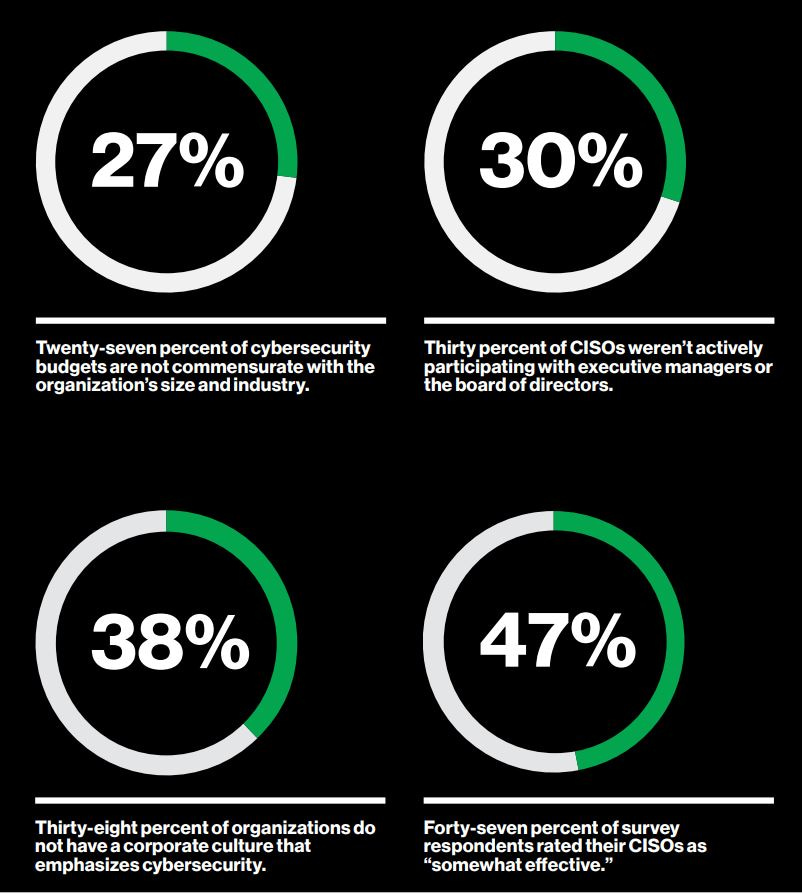
While businesses and organizations are eager and quick to move to the world of digital transactions and contactless payments, cybersecurity is a whole other story.
Recent trends and statistics show that more companies are non-PCI compliant. Why? Most likely, many of them still consider it an expense, not part of a long-term investment.
It’s a “less is more” method: The fewer people with access to sensitive data, the better; the less data you have from your customers, the better (as we all know, companies collecting information end up in hot water, anyway).
Be in contact with your payment processor to sync for any possible changes – better safe than sorry. Most importantly, remember that PCI compliance is never a ‘one-and-done’ thing: It’s a constant operation. That’s why you have a PCI compliance manager; that’s why you assess, make reports, locate ‘blind spots’ before they become serious threats. And most importantly, you’re doing it for your clients and the good name of your business.
DOWNLOAD THE PCI CHECKLIST HERE
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!








