How to Automate the Software Bill of Materials (SBOM)
![How to Automate the Software Bill of Materials [SBOM]](https://www.reflectiz.com/wp-content/uploads/2022/10/How-to-Automate-the-Software-Bill-of-Materials-SBOM-1024x683.png)
Software Bill of Materials (SBOMs) has always been a simple, powerful, and often overlooked security concept. In the software development landscape, it is common for developers to embed chunks of third-party codebases in their applications. Though this makes for an easy alternative to spending hours writing code from scratch, it poses potential security risks. Therefore, understanding what code you include in your software is critical for a developer, technology, or security officer.
Recent attacks of the SolarWinds and Log4J have emphasized the importance of SBOM as a security best practice by showing that even mighty organizations can easily fall victim to malicious practices. But despite its capability to form a security wall between cyberattacks and organizations, enterprises show reluctance to implement SBOM. This has forced the US Government to release an Executive Order to strengthen cybersecurity and specifically highlight the role SBOMs can play.
Organizations, however, rally with challenges in implementing SBOMs manually. In this article, we define SBOM, discuss its benefits, and shed light on how to automate the creation of SBOMs in three different ways.
What is a Software Bill of Materials (SBOM)?
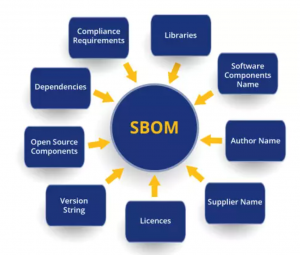
Software Bill of Materials (SBOM) is a comprehensive list of all the components and elements that form a software product. It gives detailed information on the components like dependencies, supply chain relationships, and licenses in proprietary and open source software.
Primarily, SBOMs help you manage risks by enabling complete visibility into the software you are adding to your product.
SBOM is similar to the list of ingredients you see on packaged food–the number of calories it involves, preservatives used, and other things such as salt, sugar, and flavourings. SBOM is derived from the Bill of Materials (BOM) used in the manufacturing industry.
BOM consists of structured information on all manufacturers’ raw materials, components, and parts. This way, you can easily track any faulty component directly to its place of origin and take necessary remediation steps. Similarly, SBOMs identify unique components that contain security flaws and can put your software at risk.
Created to be shared between organizations, SBOMs are written in machine-readable metadata. It contains the below-mentioned aspects:
- Open-source libraries that form application dependencies
- Plugins and add-ons that an application uses
- In-house custom source code prepared by developers
- Component information like versions, licensing status, and patch details
Why is a Software Bill of Materials (SBOM) important?
Lower costs
With SBOMs, you can employ a streamlined workflow by reducing critical time to remediate security threats. The documented software components enable you to proactively verify if the software contains any deficient components. This saves a great deal of the cost of efficient scanning resources and the financial burden resulting from cyberattacks.
Reduce code bloat
When using open-source code blocks, you often end up including different versions of the code with the same functionality. Further, these different versions come with unique defects. SBOMs help you standardize a common set of components to reduce the code bloat significantly.
Optimize productivity
SBOMs help you maximize your team’s productivity by eliminating unplanned and unscheduled work. By enabling you greater visibility into the codebase you’re using, you can better prioritize and quickly deliver code updates. Once you identify the vulnerable components, you can initiate bug fixes without the extra hassle of further investigating the identified components.
Effective monitoring
Your capabilities to monitor components you used in your product for vulnerabilities increases exponentially with SBOMs. With them, your team will have to go through a lengthy and tedious process of evaluating each and every component to check if it contains any security risk. You can further assure your clients of better security.
Easy EOL management
It is possible that you use a third-party code that includes components that reach end-of-life (EOL). Such components lose support from their supplier or vendor. With SBOMs, you can be aware of EOL components and plan for alternate solutions. Although such components may not pose a risk, they could affect performance.
Efficient code review
By giving detailed information regarding every component and subcomponent included in the software, SBOMs simplify vulnerability detection and highlights any security concerns. Further, it helps you understand the time and effort needed to make your codebase bug-free.
Policy compliance
SBOM is, in a way, a compliance checklist on what components to use and what not to use, potential security risks, and other such policies. Therefore, employing SBOM enables compliance with policies.
Why is Automation key?
Formatted to be read by machines, SBOMs comprise an exhaustive list of information, so managing and processing this data manually can be complicated and time-draining. Therefore, automation plays a very critical role in ingesting and creating SBOMs. One major benefit of automating the process is consistency in implementing all the changes as and when they’re released. It also ensures cryptographical signing and verification of components. Furthermore, automation ensures continuous scanning to produce SBOMs, making them a part of the CI/CD pipeline.
Another benefit of automation is that it offers ‘machine-speed,’ saving you time. It allows you to deploy your resources on other crucial tasks instead of manually putting together an SBOM. Also, when detecting vulnerabilities, identifying their location becomes an impractically long process. Automation also helps you to run frequent checks to update newly published vulnerabilities and mitigate them.
Below are the three key methods to automate SBOM creation.
Three ways to automate SBOM creation
1. Use a composition analysis (SCA) tool
You can optimize your resources by using software composition analysis (SCA) tools to automate the process of creating SBOM. SCA is a methodology for analyzing third-party software’s security, license compliance, and code legitimacy. It is an automated process born out of the need to boost productivity without compromising security and code quality.
Ideally, SCA tools investigate software composition, including source code, manifest files, container images, and binary files. The open source components are then listed in SBOM and run against databases to identify vulnerabilities, licenses, and security information.
SCA tools offer speed, reliability, and security by analyzing an overwhelming number of data points and compiling a comprehensive SBOM. With the emergence of cloud-native applications and complex software development methodologies, SCA tools are gaining major prominence.
In this example, we’ll explain how to create SBOM with FOSSA, an open-source dependency management tool ranked as the most significant SCA solution by the Forrester Wave. It helps you protect your software from open source risks such as supply chain threats and license violations.
Generating SBOM with FOSSA can be done in four simple steps:
- You begin by integrating FOSSA with a version control system like GitHub. You can also use its open-source CLI tool and scan your projects. FOSSA automatically scans your projects not just for direct dependencies but also for deep dependencies like licenses.
- Once your projects are scanned and the details retrieved, you need to pick a reporting format from the ‘Reports’ tab.
- After selecting the reporting format, you should pick which components you want to add to the report. You can add direct dependencies, deep dependencies, licensing summaries, and other license information.
- Before generating the SBOM, you can customize the report with your company logo or any other information you want to add.
2. Use an open-source tool
Another way of creating SBOM in an automated mode is through open-source tools. Although they help you generate SBOM at no cost, they usually cover only the basics. Also, they generally produce the report in two standard Data Exchange formats, CycloneDX and SPDX.
To explain how you can take care of your SBOM automation through an open-source tool, we will cite the example of Paketo, a community-driven open-source project.
Paketo supports multiple SBOM formats, including Syft JSON, SPDX JSON, and CycloneDX JSON in addition to Paketo-specific SBOM format. To generate SBOM using Paketo, you will need two tools: Pack CLI and Paketo Buildpacks.
Paketo first creates buildpacks that can be used to build container images. Once these images are built, you can run an inspect command. This will automatically produce a full software bill of materials.
3. Use a plugin within CI/CD pipeline
The third approach is to create and audit SBOMs within your DevOps pipeline. You can do that by using maven plugins at the build stage of the CI/CD workflow. Let’s go through the process briefly using the CycloneDX Maven Plugin.
CycloneDX is OWASP’s lightweight SBOM standard for application security and software composite analysis. It comes with multiple tools for all environments. Its maven plugin generates SBOM featuring all types of dependencies in your projects.
Firstly, you need to configure your pom.xml file, after which running the‘ mvn verify’ command will generate a bom.json file. This is followed by auditing SBOM files. For this, you will have to install the Dependency-Check SCA tool, which is a native Maven plugin. Once you run the SCA tool, you can generate your SBOM file again using the ‘mvn verify’ command.
Staying on top of the hidden dangers of third-party apps
Generating SBOM is a best practice to secure your application from supply chain threats. With the federal government issuing an EO mandating it, SBOM implementation has become a must-have from a good-to-have feature. However, one point that we wanted to highlight in this blog is the automation of SBOM creation as an alternative to generating SBOMs manually, which is a tedious and time-taking process that could potentially lead to errors like missing out on listing a few defective components or EOL information. Chances are that your business relies on external code not protected by your existing security controls. Automation can help by speeding up SBOM creation and ensuring its accuracy.
Explore our free resources on our blog and learning hub to learn how you can detect and mitigate the security and privacy dangers of third-party apps.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!