5 Unexpected Ways to Reduce Your Attack Surface

Attack surfaces are where most cyber attacks originate, and that’s simply because they’re the entire area of a system or network that hackers try to exploit to gain unauthorized access. The ever-expanding and dynamic nature of modern attack surfaces make them harder to define and defend: Corporate resources are constantly connecting to new devices.
Access is continuously being provisioned for business partners, employees, and contractors. Businesses are relying more and more on third-party code and apps to get their work done. And everyone’s IT infrastructure is expanding to the cloud. It’s no wonder organizations find it a dizzying task to manage risks from the systems, individuals, and applications connected to their network.
But while attack surface management is not easy, there are many actionable strategies you can use to reduce your attack surface and make it more manageable. This article goes beyond the established wisdom and provides five additional ways to reduce your attack surface that you perhaps haven’t considered before.
The different types of attack surface
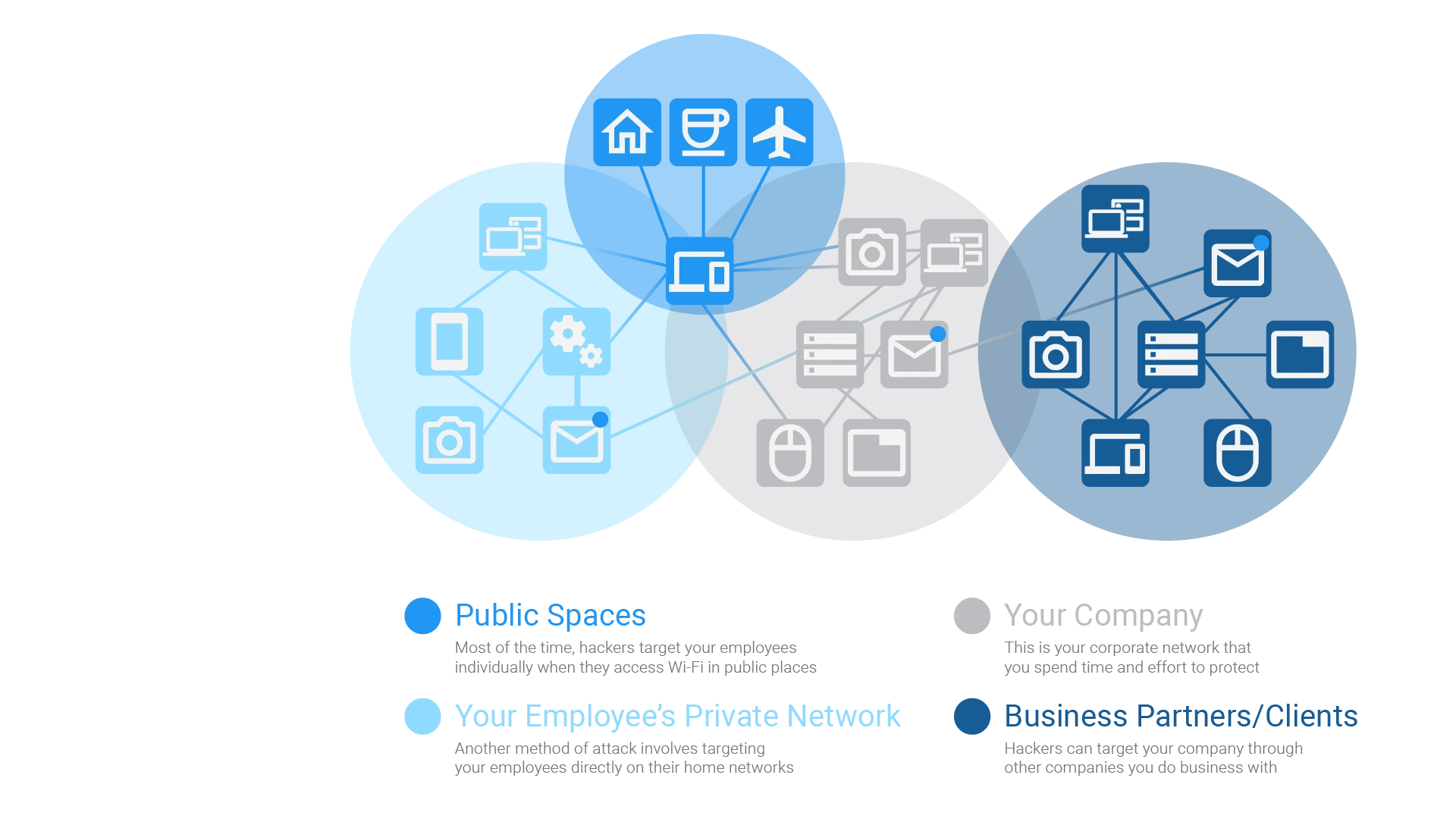
Discussions about the cyber attack surface often focus on its digital elements; the systems, apps, and network infrastructure that comprise an organization’s IT ecosystem. Limiting your focus to securing the digital attack surface is risky, considering there are other types of attack surface you should also be aware of, including:
- The social engineering attack surface—this attack surface is the sum total of people with access to your IT environment (employees, contractors, partners) and their susceptibility to social engineering attacks, such as phishing or tailgating.
- The physical attack surface—this is the total range of endpoint devices connected to your network that malicious actors could access and exploit to gain entry into your IT environment. The physical attack surface includes employee laptops, on-premise workstations, USB ports, printers, IoT devices, servers, and more.
Some sources further add to this nomenclature by defining various other attack surfaces, including IoT and AI attack surfaces. However, these are not established definitions, and both arguably form a part of an organization’s physical and digital attack surfaces.
Attack vectors 101
An attack vector is a path that a malicious actor takes to exploit some kind of weakness or vulnerability in your attack surface. As organizations’ IT ecosystems expand, there are more possible paths for unauthorized access unless the attack surface is appropriately managed and reduced. Some of the main attack vectors used by today’s threat actors include:
- Vulnerable web components—this could mean risky third-party code that powers a certain function on your website, a poorly coded web app, an expired SSL certificate, or a vulnerable open-source library/framework.
- Phishing emails—employees lacking good cybersecurity awareness may get duped by emails that convince them to install a trojan horse or reveal sensitive credentials that let a hacker in.
- Weak or stolen credentials—users could set weak passwords that hackers can easily guess using manual or automated methods, while the dark web is awash with 24 billion stolen credentials that can be reused to hack into networks and apps.
- Malware—malicious code can exploit attack surface weaknesses in several ways, from drive-by downloads at malicious URLs that users click on, to users plugging a USB containing a virus or worm into a network endpoint.
- Misconfiguration exploits—IT users can provision cloud infrastructure with just a few mouse clicks, and it’s becoming increasingly common for threat actors to exploit misconfigurations in this infrastructure. The exploits that prey on misconfigurations include searching for unsecured cloud storage buckets, targeting API vulnerabilities, and more.
Why ‘reducing’ is the word of the day?
There is an increased focus on attack surface reduction in the cybersecurity community because having fewer available paths into your network make it more challenging for malicious actors to achieve their aims. On top of this, attack surface reduction makes it easier to secure your organization by narrowing down security measures to cover fewer entry points.
5 ways to reduce your attack surface that you didn’t consider
Many sources point to similar established methods of attack surface reduction, including improving password hygiene, performing regular vulnerability scans, and adequately protecting code or data backed up to the cloud. Here are five ways to reduce your attack surface that you may not have thought about before.
1. Be pedantic about your inventory
The ability to manage and reduce your attack surface depends largely on the level of visibility you have into the assets, user accounts, and systems that comprise your attack surface. Being pedantic about establishing and maintaining a comprehensive inventory allows you to effectively manage the risks that emerge in a dynamic and expanding IT ecosystem. These risks include out-of-date operating systems, third-party components, and user accounts with no valid owner.
2. Consider that your attack surface includes third parties
An overlooked influence on the risk profile of attack surfaces is an increased reliance by organizations on third-party vendors, suppliers, contractors, and even code. These third-party sources increase supply chain risk, expand the attack surface, and introduce new viable paths for unauthorized users into your IT ecosystem.
Consider how a company website’s pages, domains, and subdomains might all be powered by various third-party technologies owned by different vendors. Security weaknesses in any one of these components could compromise the website’s entire ecosystem and whatever resources are tied into that. By accounting for third-party risks, you can procure solutions that monitor your third-party risks and help prevent attacks like island hopping.
3. Restrict access to devices and data
Sensibly restricting access to devices and data is another important attack surface reduction strategy. Users should only get the minimum access needed to complete their jobs so that a compromised user account doesn’t necessarily mean that the hacker has a viable path to a specifically targeted resource (app, system, data).
Minimizing the number of privileged accounts further reduces the attack surface by limiting the points at which hackers can seize administrative-level control. Lastly, regular audits of user accounts can reveal cases where users have excessive levels of access privileges that you can revoke. Auditing access can even reveal user accounts with no valid owner (orphaned accounts) that could still potentially be compromised.
4. Restrict attacker lateral movement with network segmentation
Network segmentation divides your network into distinct sub-networks or zones that can isolate specific groups of resources and control traffic flows between the various zones. This strategy can immediately impact your efforts to shrink your attack surface by isolating various hardware and software away from the Internet.
Threat actors use multiple scanning tools to detect Internet-accessible resources and probe them for weaknesses and vulnerabilities. Analyzing your attack surface often uncovers Internet-accessible resources that either don’t need to be accessible from the Internet or shouldn’t be.
Another way that network segmentation reduces the attack surface is by restricting lateral movement so that even if a compromise occurs, the attacker can’t find a path to the desired resource because it’s appropriately segmented and inaccessible.
5. Train your employees
Effective employee cybersecurity training should be central to any approach for reducing your attack surface. Consider how even beyond the susceptibility of employees to social engineering, the interaction between people and technology creates many potential weaknesses and vulnerabilities in your attack surface (e.g. misconfigurations, setting weak passwords, plugging random USB drives into endpoints).
Many approaches to cybersecurity training treat the task as a compliance box to tick rather than an endeavor to get users on board in recognizing their own importance to their organization’s security posture. To train people more effectively, it’s worth considering fully managed cyber training platforms that not only limit the IT burden of training people but also focus on more effective and engaging training materials tailored to users’ roles.
Mitigate attack vectors with continuous monitoring and continuous learning
It’s also worth exploring the idea of conducting a dedicated attack surface analysis project. An attack surface analysis maps out all the areas of a system or network you need to monitor and test for security vulnerabilities and weaknesses.
Also, beyond the steps listed in this article, continuously monitoring the full scope of modern digital attack surfaces is imperative to attack surface reduction.
This includes websites, third-party applications, code repositories, domain names, FTP servers, ports, IP addresses, web applications, VPN logins, and more. This entails adopting a more holistic approach to how you monitor for risks so you can mitigate a comprehensive range of attack vectors. Don’t even know where to start from? Learn more about attack surface management and reduction here.
FAQs
What is reducing the attack surface?
Reducing the attack surface refers to the practice of minimizing the points of vulnerability and exposure in a system, network, or application that could be exploited by potential attackers. This involves implementing security measures to limit the avenues through which attackers can gain unauthorized access, thereby enhancing overall cybersecurity.
What is meant by attack surface?
The attack surface is the sum of all possible entry points and vulnerabilities in a system, network, or software application that an attacker can exploit to compromise its security. A larger attack surface provides more opportunities for malicious actors to find and exploit weaknesses. Reducing the attack surface is a fundamental security principle to enhance resilience against cyber threats.
What is attack surface monitoring?
Attack surface monitoring involves actively observing, analyzing, and managing the various elements that contribute to the attack surface of a system. This can include monitoring network traffic, tracking software vulnerabilities, and staying informed about potential threats. The goal is to identify and address changes or vulnerabilities that could be exploited by attackers, thereby maintaining a proactive and adaptive security posture.
What is the modern attack surface?
Third-party applications, especially those externally controlled, are an essential aspect of the modern attack surface. Organizations often use various software and services from external vendors, and vulnerabilities in these applications can be exploited by attackers. This includes not only applications but also APIs that enable communication between different software systems.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!