Step by Step Guide to Preventing Island Hopping Attacks

Island hopping attacks are a vector for cybercriminals and hackers to target large businesses with sophisticated defense mechanisms. This type of attack, malicious actors no longer need to target their intended victim – they study its supply chain instead, and infiltrate the less secure links they can find within it. Their key tactic is to move laterally within businesses to reach its final target from within their circle of trusted relationships.
This works well because the target business may not see the attack coming, since it didn’t originate at the usual red flags: untrusted entities, an unauthorized device, unexpected geo-location, to name a few. Cybersecurity teams overlooking less suspicious attack vectors, such as long-term business partners, risk falling prey to these types of attacks.
What is Island Hopping?
The term derives from the United State’s plan during World War II to infiltrate Japan by hopping the nation’s islands to get to Japan’s mainland. In cybersecurity terms, this strategy is apt to infiltrating many third-party entities that make up modern supply chains until attackers reach their intended target.
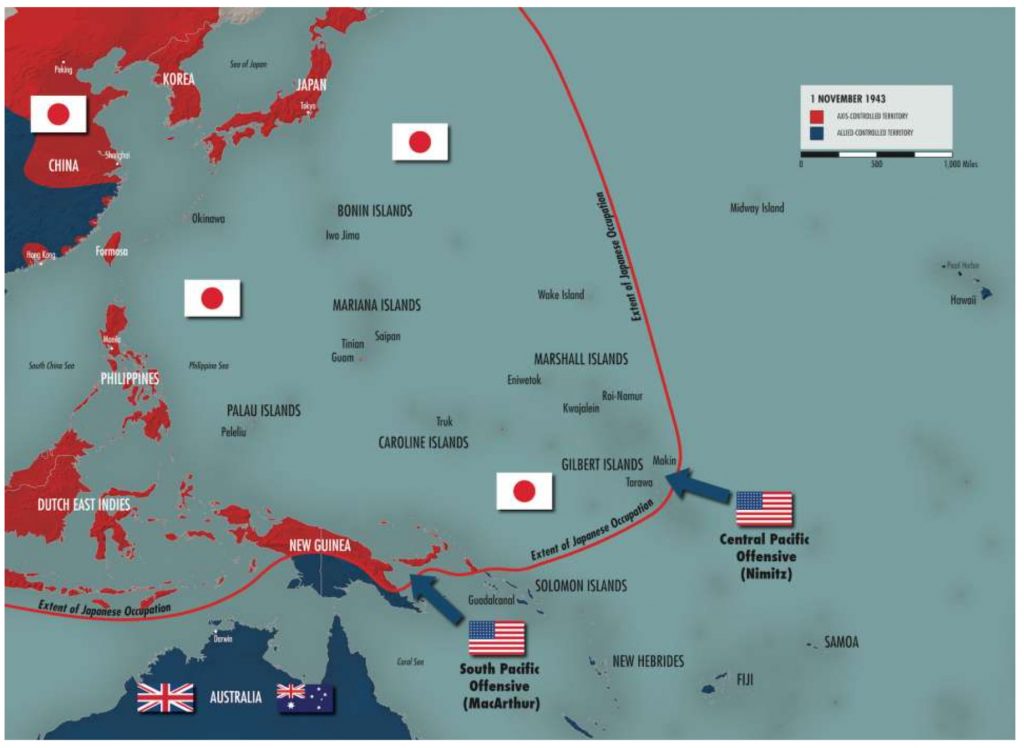
An island hopping attack requires considerable effort and expertise to execute successfully due to the amount of reconnaissance needed to gain the necessary knowledge to launch it. Attackers first identify the target business’s direct suppliers or third-party entities. Once identified, the attackers proceed to run reconnaissance on those entities and move down the supply chain until they find an entity with weak cyber security controls to infiltrate.
Once attackers infiltrate the first entity in the chain of islands, they will proceed to the next target using access gained during the initial attack; thus infiltrating entities one by one using the trusted connections between them.
Attackers target businesses for many reasons, including financial gain, obtaining sensitive information such as credit card or customer details, or attempting to damage a company’s reputation. But of course, most attackers have different motives and this is by no means an exhaustive list. Your business may be targeted, but that doesn’t mean it is the final target. Similarly, if one of your vendors was attacked, you should be on guard – this means that you might be next! One thing is for sure: following cyber security best practices can help you to identify and prevent an island hopping attack.
How to prevent Island Hopping attacks?
Preventing a cyber attack from an external entity seems straightforward enough, since cyber security teams expect them to come from sources such as third-party applications installed on their website. Preventing and combating cyber attacks that originate from your trusted entities is another matter altogether.
Basic and outdated cyber security strategies that trust external suppliers will leave a business vulnerable to island hopping attacks since these trusted entities may not receive the same level of scrutiny from their cyber security teams. A security overhaul is needed to cater to the ever-changing threat landscape of the modern business. These best practices can help:
Monitor your third-party applications on an ongoing basis
Did you know that more than 60 third-party components or applications are running at any given time in a modern-day web application? Not every security team is aware of them all. This means that traditional security and risk assessment tools do not cover the entire spectrum of risks third-party components bring into your website. Most traditional security assessment tools do not have the capability to identify vulnerabilities within these third-party libraries and components, leaving an unprotected path for attackers.
Targeted risk assessments are an excellent method of identifying third-party components’ risks in an application and business. But businesses usually only perform these risk assessments at the start of the deployment or periodically, since these risk assessments require time and specialized skills.
Modern businesses need instead to continuously monitor the third-party libraries and components running within their applications to ensure they are not exposing security risks and blindspots that put application security at risk or breach regulatory compliances.
Many applications use third-party or open-source libraries, frameworks, and components to render development more efficient. But using these third-party or open-source components magnifies the risk of accidentally introducing a vulnerability into the application. Beyond that, the use of 4th and Nth parties makes controlling risks even harder.
For example, you probably remember the log4j turmoil of 2021? All the applications using the library encountered a zero-day vulnerability that rendered their servers and applications susceptible to remote code execution by attackers. Because log4j is used as a logging tool for many different digital services, it was difficult for security professionals to quickly identify the applications affected. Many software use open-source code, but this one is particular in that it is maintained by several individuals who have little incentive to keep it at its best shape. So when there’s a chance your systems include at least one component that relies on log4j for logging, this is what’s at stake:
Identifying and remediating these weak spots takes a long time due to the many dependencies involved. What’s more: it’s not enough that you are up-to-date if all your vendors aren’t doing the same! So the only effective mechanism to detect these types of risks is to continuously scan and monitor all third-party components, libraries, frameworks, and digital vendors used by your website or online service. After all, as log4j shows, even the smallest misstep by your vendor’s vendor can expose your organization to severe attacks. By mapping out your website’s digital components into an assets inventory and constantly keeping them in check, you can detect vulnerabilities in real-time to remediate vulnerabilities before any damage is done.
PS: If the log4j topic still haunts you, you may be interested in a free scan to find log4j vulnerabilities in your website.
Understand what data is being used by your third parties
Some third-party components require data to be transferred from the application to their platforms in order to provide comprehensive solutions to a business. This information varies widely depending on the nature of the business, and can include anything from user behavior data to sensitive customer payment information. Regardless, identifying the transfer of data to these third parties is crucial to assess the risk they bring in.
But understanding the data flow is not enough to evaluate risks – knowing what type of data these third parties use and transfer for processing or storage is also essential. If you know these two components, you can visualize what kinds of risks you’re facing and prioritize, prevent, and create protocols for managing them in case of emergency. For example, the risk of a third party may be directly correlated to the nature of the information it is handling, since the more sensitive the information, the more significant the damage if it gets into the wrong hands.
To reduce risks, businesses must restrict their flow of information by only sharing the essential and nothing more. It is also critical to look into the retention policies of this information – third parties should only store it for a specific period and must securely destroy the data once the relevant processing or task is complete. Ensuring that this is happening is one vital component in preventing island hopping attacks since fewer data exposed via third parties means less gateways for attackers to find their way into your systems.
Put weaknesses and risks in the spotlight
Using third-party components within web applications has its benefits, but it also comes with many security risks that can open applications to island hopping attacks. These attacks are difficult to detect and prevent without proper security controls. With websites today making dozens or network requests to third-party providers on each webpage, it is safe to say that traditional security tools have become incapable of handling the situation. Knowing the operational status of third-parties and performing the occasional risk assessment is no longer enough to eliminate the security blind spots they create.
Here’s the way forward: Continuously monitor third parties, detect gaps between your application security processes and the security risks created by third parties running on your website, and understand what data is being used by your third parties as well as their actions to discover previously unknown fourth-party dependencies. Reflectiz can help with all of these. Book a demo to learn how.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!