Magecart Hacking Groups: No Longer Just an eCommerce Threat

Original article was posted on September 15, 2019, the article was edited on May 9, 2023.
Magecart is essentially a subset of Web Skimming that injects malware into payment pages of online businesses to steal credit card information and personal data. This notorious hacking consortium already has a long list of eCommerce exploits to its name, but has now started targeting other online services and businesses in 2021. How is all this related to third party risk management and ongoing monitoring? Let’s dive into it.
Magecart has already become a feared name in the cybersecurity community, CISOs, CIOs, web security professionals, and security analysts are all combating this third party risk on an ongoing basis. Magecart’s main methodology is to steal sensitive information from customers that use eCommerce and other eService platforms by exploiting vulnerable third parties on these websites.
Magecart has been active since 2015 and has attacked tens of thousands of eCommerce and B2C websites since then. The most common target has been Magento, an open-source eCommerce platform written in PHP. As we’ll learn from this article, third party risk management (TPRM) and continuous monitoring becomes extremely crucial when it comes to securing these websites.
Who’s Behind Magecart?
Magecart figured amongst the ‘Most Dangerous People on the Internet in 2018’ listed out by WIRED. They have grown even more during the COVID-19 pandemic. The Magecart threat, as a whole, has become more common in many aspects. The attacking groups behind it (more on them later), present more sophisticated hacking techniques that target and exploit vulnerable third parties.
As a result, websites are more exposed. Magecart attacks are on the rise, not just in terms of severity, but also their frequency. The fact that these eSkimming (digital skimming) attacks are escalating dramatically is also related to the increasing popularity amongst hackers. This is largely due to the growing use of third parties on modern websites and the security risks created by third party relationships.
Magecart refers to the form of supply-chain attacks in which hackers infiltrate eCommerce and other eService websites by exploiting third party relationships and dependencies. These applications can be locally or remotely stored. When no third party risk management program (TPRM) is in place, they steal sensitive information from unsuspecting users at the transactions and checkouts stages.
These groups are known to have attacked tens of thousands of eCommerce websites to date. Some of the most famous examples are Ticketmaster, British Airways, and Newegg, but they are not alone. All these organizations have one thing in common, and that is they were all hit by Magecart. These attacks create financial losses, reputational damage and legal and regulatory issues.
The latest $230 million fine which was issued to British Airways by the UK privacy watchdog, the Information Commissioner’s Office (ICO), shows that Magecart breaches are under the direct accountability of the breached organization. The same can be said for Ticketmaster UK, which had to cough up £ 1.25 million for the infamous 2018 breach. This is before we even touch the brand damage aspect.
Related: Ticketmaster UK: A Lesson to be Learned
How the Typical Magecart Attack Works
There are two stages which are most evident in Magecart hacking attack sequence:
Infiltration of your website – Generally, using two methods to place the malicious code on your website. One is to forcibly break into your website and place the code on your server. But the more common way is to target your third party vendors who don’t manage risk well. Even doing your due diligence and good vendor risk management is not enough to stop Magecart hackers from hitting the jackpot as they are not covering post production changes.
By infecting a third party tag, the Magecart group makes a malicious script run on your website when it is called on the user’s browser. Additional information about third party risks on websites can be found on one of our August 2019 blog posts. The most worrying part is that even after your website has been infected, it often takes traditional application security tools a lot of time to detect the breach.
Did You Know?
As per a recent IBM report, the average life cycle of a data breach in 2020 was about 280 days. It takes an average of 220 days to identify a breach and another 72 days to contain such a breach.
Skim vital information from a form – There are many ways to capture data, but eSkimming is the most prevalent method. The skimming code is a JavaScript (JS) code that searches for and collects personal information, commonly known as hooking or keylogging. One way is to monitor all keyboard presses on a sensitive page. The other way to do it is to pick up information from specific parts of a form such as credit card number and CVV number fields, also known as formjacking.
Usually, the cybercriminals conceal their malicious code behind other innocuous-looking codes (digital signatures) to avoid identification. This is how they escape undetected despite regular static code testing. Once obtaining the requisite information, it is not hard to relay it to their server. The attackers can then send the data wherever they want, without any real detection tools in their way.
Formjacking is one of the most common techniques used by online skimming groups such as Magecart.
Who Does Magecart Target?
For the Magecart attacking groups, eCommerce websites are the most convenient targets, mainly because of their poor third-party risk management and lackluster risk assessment. But if you think that these groups only target “regular” eCommerce retailers, you are sadly mistaken. Magecart attackers now target all sorts of service providers wherewith people use credit cards for making payments and transactions.
The French advertising network – Adverline case, demonstrates how Magecart “crossed the line” of traditional eCommerce websites. It’s not just an example, but also a frightening reminder of how creative these skimming groups can be. This worrying trend has only intensified with the accelerated digitalization (more vendor risk) across all sectors following the COVID-19 pandemic outbreak in early 2020.
Here are just a few examples of recent Magecart incidents and exploits. Keep in mind that this is just the tip of the iceberg. Let’s take a closer look:
eCommerce Platforms
Almost every online business today is based on popular platforms like Woocommerce, Zencart, and Shopify. Dutch security researchers found a glaring Magecart vulnerability in these world-famous platforms that are powering thousands of eCommerce and eService websites today. The malware mimicked a fake payment page that tricked customers into exposing their payment information.
Social media buttons were also found to have become an attack vector. Malicious skimming code was injected via these seemingly unharmful buttons that we all like.
National Baseball Hall of Fame
Magecart attackers also used a fake Google Analytics script to hack into the website of the National Baseball Hall of Fame, something that went undetected for months!
The attackers included a malicious Magecart script to steal credit card information from people who purchased items on the site. This script affected the website between November 15, 2018, and May 14, 2019. The breach was detected on June 18, 2019, but the damage had already been done. The breach affected only those customers who purchased merchandise from the website.
Poker Tracker
Gambling websites are also prime targets due to the number of deposits and withdrawals that are performed on them. One such hack involved the compromising of the Poker Tracker website to steal payment information from customers. Poker Tracker is software that helps gamblers to improve their chances of winning by analyzing statistics based on the opponent’s moves.
On August 8, 2019, Anti-malware blocked Poker Tracker from connecting to domains renowned for hosting credit card skimmers. Investigations revealed a Magecart type attack targeting the outdated Drupal platform. This marked a shift from the common Magecart strategy that mainly targeted Magento vulnerabilities. This means that vendor risk and third party risks are not the only challenges today.
Magecart Groups: A Dangerous Consortium
With more companies adopting the online route, there is intense competition among cyber-criminals like Magecart. According to ZDNet, There have been instances of one Magecart group attacking and sabotaging the efforts of a rival Magecart gang. Hacking groups and entities have always been competitive and the Magecart space is no different. They are all fighting to hack third party vendors and escalate fast.
In one example, Group 9, a relatively recent entrant to the Magecart gang attacked another Magecart group, Group 3, primarily active in South America.
Group 9 added a unique code to their card skimmer that sought information from domains associated with Group 3’s operations. On identifying these domains, it came to be known that Group 9 was not only stealing data from Group 3, but also altering the data collected by Group 3, thereby rendering them useless. Therefore, the buyers of such spurious credit cards will find that the card does not work.
Consequently, it affects the seller’s credibility. This is one of the best examples of a thief stealing information from the other crook. There are many sharks in the pond.
Related: The Cybersecurity Effects of Fourth-Parties on Websites
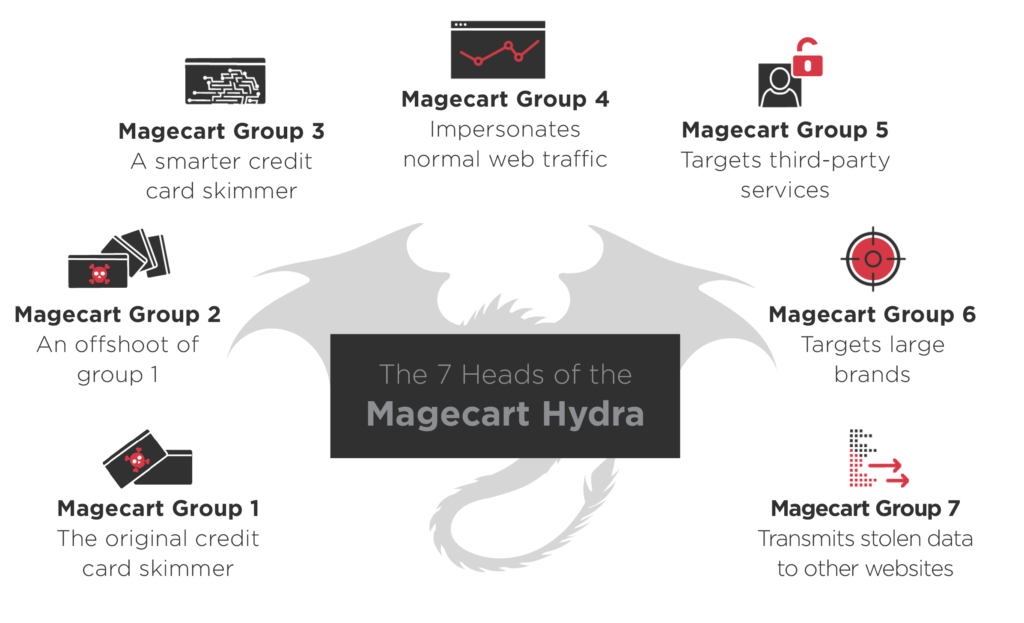
There are over 12 active Magecart groups (as we know of so far) today. Top ones include:
- Magecart Group 1 – The original eCommerce website JavaScript eSkimmer
- Magecart Group 2 – Specializes in using stolen cards for overseas purchases
- Magecart Group 3 – Founded in 2016. Active mostly in South America
- Magecart Group 4 – Has deep connections with organized crime syndicates
- Magecart Group 5 – Specializes in exploiting third party vendors
- Magecart Group 6 – Focuses on high-profile targets (British Airways, Newegg)
- Magecart Group 7 – Is good at transmitting stolen data to remote servers
Third Party Risk Management: A Must Have Today
Firstly, you need to adopt a layered approach when it comes to securing your website/s from Magecart attacks. Here are just a few layers,
- Content Security Policy (CSP) – This useful cybersecurity standard helps CISOs and security professionals to whitelist the domains that are considered to be trusted (and valid) sources of data/information. Only JavaScript code received from these trusted domains is executed. But as explained earlier, CSPs won’t help you if the trusted domain has been breached.
Related: CSP: Not Exactly a Magecart Vaccine
- Sub-Resource Integrity (SRI) – This security technique basically involves adding a cryptographic hash to the JavaScript, something that allows browsers to verify that all received files have not been manipulated. The problem, or challenge, with SRI is that it’s hard to configure for dynamic JS code. Third party vendors are constantly changing their code.
- Third Party Risk Management Program – A TPRM program essentially helps organizations rate third party vendors based on the security risk they bring into the ecosystem, something that allows them to take their risk assessments to the next level. Unfortunately, due diligence is also not sufficient in fighting Magecart today, nor are third party SLAs with third party vendors.
While it’s good to have the aforementioned measures in your AppSec toolkit, there is no real substitute for ongoing and continuous monitoring in third parties.
Third party risk can only be eliminated by understanding the security blind spots that are being created by newly formed dependencies and vulnerabilities by third parties you are using. There is also the issue of fourth parties that often flies “below the radar”. This visibility and transparency should ideally be complimented by the ability to set up customizable alerts for quick detection and remediation.
What Does the Future Hold for Magecart?
With people preferring online payments more to cash, Magecart attacks will keep on increasing as vendor risk rises. They already hide their malicious codes behind innocuous-looking codes to escape detection. We have seen how dangerous Magecart can get. Therefore, it is no surprise Magecart ranks amongst the eight ‘Most Dangerous People’ on the Internet today.
From a more technical perspective, we see a growing number of security experts and researchers that point out how difficult it is to stop Magecart threats. A recent Security Boulevard blog post demonstrates it, naming Magecart as one of the most sophisticated cyber-attacks that are growing in 2019 and are difficult to stop. Third party risk management is no longer an option for online businesses.
The bottom line is clear and simple: Magecart threats are escalating. They are also becoming more sophisticated and challenging for CISOs and security teams. These risks are hard to detect as they are indirect, yet baked into your software supply-chain. As someone rightly said “There are two types of companies, those that have been hacked, and those who don’t know they have been hacked.”
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!








