The Cybersecurity Effects of Fourth-Parties on Websites

Fourth party apps on websites are commonly referred to as “the vendor’s vendor code”. Fourth-party apps may offer additional benefits, but at the same time they also carry a set of threats while running on your websites. For your users, they are all, first-parties.
In this article, we will refer to the threats that fourth-parties present to websites, from a cyber-security and privacy perspective.
Article update, August 2020; originally published on July 2019
Fourth-parties on Websites: a simple but risky supply-chain
Most code today is no longer developed from scratch. It is based on open-source, “shelf” products and vendors who offer solutions that can integrate with other platforms. That makes everything faster and cost-effective. This is what created web third-parties and therefore can be found almost anywhere third-parties are used.
Let’s look at your website as an example and see what happens there and what also happens at your vendors, who also have third-parties of their own. Every move or modification on your vendors’ vendors, can affect your site.
But tracking these modifications is rarely possible and the obvious problem in this case is lack of control and hence mitigating risks.
To begin with, let’s understand that in the user’s browser, a script – is a script. The meaning of it is that each running script can do almost anything to a webpage, including loading additional scripts, the Fourth-party scripts.
Even if you installed a third-party app from your most trusted partner, this script can do whatever it wants on the given page. As an example, we’ll use the most popular tag manager in the world, Google Tag Manager or GTM.
Behind the scenes, a tag manager is a smart third-party script with “credentials” to load additional scripts to a page or the website. In fact, we can now understand that a tag manager, this case GTM, is a loader of fourth-parties in an organized way. But this is just one example. In the real world every third-party can just load any fourth-party it wants to your website. Do we want GTM to load fourth-parties scripts? Well, yes. But what about the dozens of other tools that you had, did you also allow them?
Fourth-parties by Numbers
To get a more accurate view, let’s look at the numbers first. On average, e-commerce websites, financial and online services websites today use approximately 30 to 80 third-party vendors in total. According to our data, based on thousands of financial and e-services site analysis, the average ratio is 30% of fourth party apps. When we examine ecommerce sites or news sites, the ratio in many cases becomes higher and so are the definite numbers.
To learn more about the third-party statistics, including data referring to content and news websites, visit our latest post:
The Figures of Third-Party Application Security on Websites.
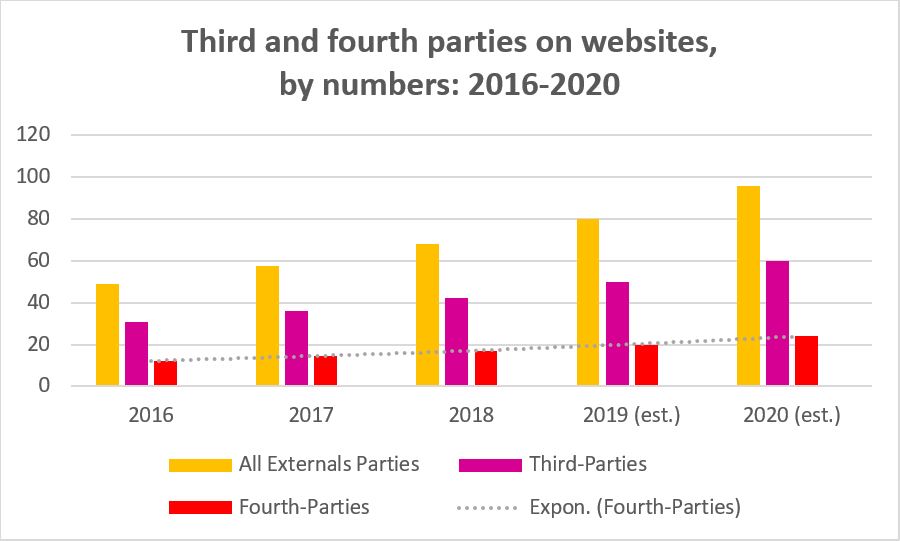
Third and fourth-parties expansion on commercial websites 2016-2020 (prediction)
Meet Your New Friends: few examples of fourth parties.
Are you familiar with them?
ComScore – To show how fourth-parties are used and to demonstrate the risks they present, we’ll refer to how several advertising giants are using ComScore’s media measurement and analytics tools. ComScore is an authority and ad products are almost bound to use it. For these advertising products ComScore is a third-party, an analytics tool for them. For your website, ComScore is a fourth-party. Most likely you’ll be unaware that it even exists.
DoubleClick – Here’s another example. As part of your marketing efforts, you use an embedded YouTube clip to present your product on your website. But did you know that Google installs Double-Click pixels on your website?YouTube belongs to Google, and Google uses its advertising platform, Double-Click, to monitor who is watching your YouTube video. So now you have a Double Click pixel on your website.
Fourth-party apps detected on a typical scanned news website.
Source: Reflectiz scan results.
Video Players – Almost any website today uses a video player. To enable internet video player functionalities, these tools are using a wide variety of technologies, in many cases open-source., Once you use a video player solution on your website, the provider installs a fourth-party which is the player itself. This happens with no prior approval or control from the security team’s end.
Anti-Bots – Anti-Bot tools are commonly used on websites for security reasons and to make sure no one is “spamming” components like video or watch count, and the data gathering in the process. But to function properly, Anti-Bots needs to do key-logging on your users’ actions.
The bottom line is simple. From almost any third-party component you use, you suddenly got yourself several unattended “friends”, fourth-parties, that are now running on your site. Well, this may be legitimate, but are you willing to let external components decide what will run on your website?.
Fourth-parties on websites from cyber-security perspective
If we go back to where we just started, all these “friends”are running on the user’s browser. Therefore, they are identical to the user, with no way to distinguish between them, i.e., client-side code. In practice a third-party vendor can load other’s vendor scripts to a page, without your users even noticing it. From a cyber-security point of view that is a severe risk.
Fourth parties risks
Almost by default fourth-parties introduce an uncareful supply-chain process presenting both privacy and security risks. And that can be a problem, especially if you consider its GDPR / CCPA implications, or possible supply-chain attacks. From an end-user point of view, the fourth and third parties are both data processors. Both have the same authorization level and ability to provide the same privacy rights stated by the regulation. You, as the website security owner, need to validate it.
Those are relatively simple cases, but according to what we see in our day-to-day analysis, most cases are more complex and involve a structured process of commercial data sharing. Like other supply chain processes, without proper monitoring tools, this instance would be almost impossible to track. The privacy and security consequences are clear cut. Be aware!
Supply-chain Attacks
If you consider supply chain attacks, the role of fourth-parties becomes clearer and so does the need to address it as an evolving risk factor – especially for the web ecosystem.
Hacking fourth-party vendor scripts on YOUR website almost equals hacking your website. The biggest challenges for security teams in this case are visibility. Unfortunately, in most cases there’s no way for security teams to monitor these new “friends” that just settled on your website, likely without your permission.
Fourth-parties are hard to discover. From an attacker point-of-view, it’s a strategy sometimes a goldmine. Similar to third-parties, an attacker can hack more websites through a single hub, but the same attacker can also hide the trails more effectively and avoid tracking.
How to handle your web fourth-parties and control them?
Everyone today focuses on privacy regulations, security and privacy professionals deal with the uncompromising requirement to identify data processors. In this case, fourth-parties become a severe and immediate risk.
Demands from financial institutions
According to EBA published in 2019 every major financial institution in the European Union should reveal its critical fourth-party vendors. For the first time, banks are demanded to do due diligence and monitor their fourth parties. However, do they have the ability to detect them? How can financial institutions actually monitor them?
Are the security perimeters you currently use enough?
The common third-party security practice involves due-diligence processes, questioners, seasonal vendor surveys, penetration-testing and even intelligence tools. But when it comes to fourth-parties on websites, this is hardly the case. Are these your vendors? Can you trust them? Here’s the problem with fourth-parties: these are not your vendors, these are your vendors’ vendors!
Within the regular cyber-security course, these are hard to track. Fortunately, when we refer to websites there are few great tools (and Reflectiz is one of them) that allow security teams identify the presence of fourth-parties and, what’s beyond them.
Once discovered, an effective cyber-security process needs to be carried out in order to avoid unnecessary fourth-parties privacy and security risks. This should include adding fourth-parties to the relevant third-party due-diligence process, fourth-party tracking, technology funnel identification, and a notification mechanism that alerts of any related abnormality according to its severity. But the most important missions you need to start with are to first discover your fourth-parties. and second- create a baseline and detect any modification.
Learn more about fourth-party risks on your website
Contact us OR Book a Meeting with our experts
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!