The Holiday Security Code Freeze Paradox
Learn how hackers exploit the holiday code freeze to launch perfect “placeholder-to-payload” attacks, and discover proven freeze-ready security strategies.
Download the full holiday season security playbook here.
It’s a common misconception that a code freeze means a website becomes static, as third-party scripts continue changing dynamically and can be altered at any time. While holiday freezes ensure uptime during peak transaction periods, they severely limit defenders’ response capabilities. This paradox results in:
- Maximum damage potential: Attackers target high-volume shopping days.
- Minimum response capability: Organizations operate with skeleton crews and slowed patch decisions.
The data underscores the risks:
- 11,000 e-commerce sites fell victim to e-skimming software in 2024, a threefold increase from the previous year.
- Fraud spikes by more than 20% on Black Friday and Cyber Monday.
- Global e-commerce fraud losses reached $48 billion in 2023.
The Placeholder-to-Payload Attack Pattern
This attack pattern is increasingly popular:
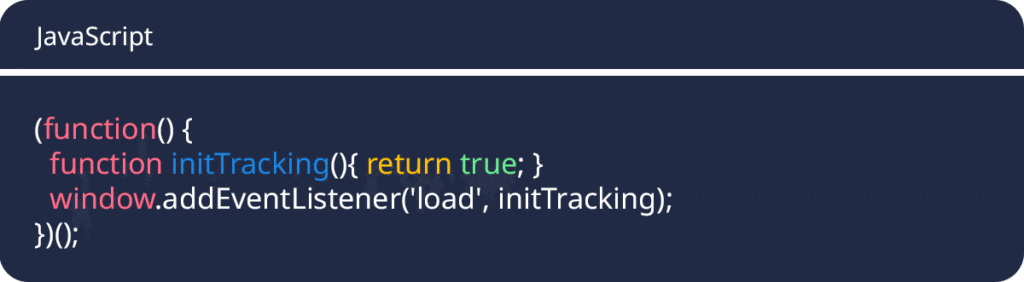
Phase 1: Harmless Placeholder
Attackers introduce a harmless-looking script that behaves like abandoned dev code. It sits inactive for months, raising no alarms.
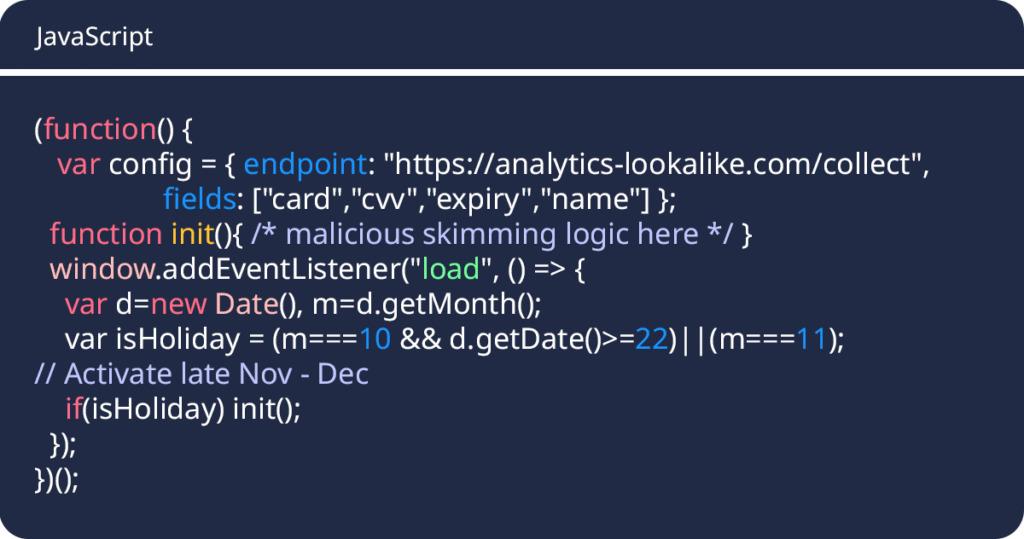
Phase 2: Timed Activation
Come late November, the dormant code activates as a payment skimmer during peak shopping days, when patching is riskiest.
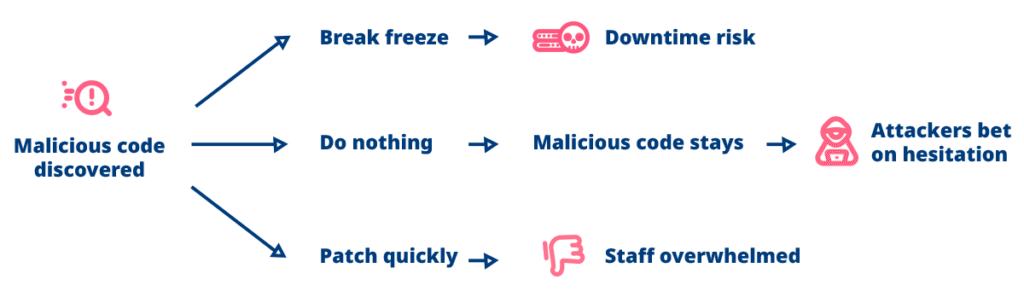
Phase 3: Response Paralysis
When they discover the malware, defenders face impossible options: break the freeze and risk reducing uptime, leave malicious code active, or attempt quick patches with under-resourced staff. Attackers bet correctly that many organizations will hesitate.
For more, Download the full holiday season security playbook here.
The Supply Chain Lesson: Polyfill.[io]
Compromised code doesn’t require hackers; it could be human error or a misconfiguration giving legitimate third parties excessive data access. Example: A misconfigured TikTok pixel collecting sensitive user data without consent violates GDPR. No malicious intent, same outcome: unauthorized data exposure.
Polyfill.[io] exemplifies this risk. When attackers bought the abandoned but widely trusted JavaScript library, they weaponized a tool used across millions of sites:
● Acquired a legitimate, widely used library with malicious intent.
● Kept operations normal for months to avoid detection.
● Injected malicious logic targeting specific users during peak hours.
This patience mirrors the placeholder-to-payload model: maintain cover, then strike when defenders are least ready.
When “Helpful” Updates Break Everything: Handlebars.js
Even without malicious intent, external services can disrupt code freezes. During Black Friday weekend, a website using content delivery network (CDN)-hosted Handlebars.js could face disaster when the provider auto-updates to a version with breaking template syntax changes.
The “security improvement” is legitimate, but existing templates break instantly. Product descriptions render as escaped strings, checkout forms lose formatting, and conversions plummet during increased traffic days. The CDN’s helpful update creates exactly the stability crisis that code freezes prevent.
This exposes a critical blind spot: Code freezes protect against your changes, but third-party services evolve independently. A single dependency update cascades into sitewide failures, regardless of internal deployment restrictions.
Defense Strategies That Still Work During Code Freezes
Even when you can’t deploy new code, you can still add these smart protections:
1. Content Security Policy (CSP)
Restrict what scripts can run and where they can connect.
HTTP
Content-Security-Policy:
default-src ‘self’;
script-src ‘self’ https://trusted-cdn.com;
connect-src ‘self’ https://api.yoursite.com;
frame-src ‘none’; object-src ‘none’;
base-uri ‘self’; form-action ‘self’;
report-uri /csp-violations;
Dropping “unsafe-inline” and log violations blocks many injection vectors.
Downsides: CSP implementation is complex, requires deep resource knowledge, and can break essential features. Whitelisted domains offer no protection when compromised: CSP can’t detect when trusted sources turn malicious.
2. Subresource Integrity (SRI)
Ensure third-party scripts haven’t been altered at their source.
HTML
<script src=”https://cdn.example.com/lib.js”
integrity=”sha384-<HASH>” crossorigin=”anonymous”></script>
Downsides: SRI breaks functionality when resources update since hash changes block loading, requiring constant maintenance to keep hashes synchronized with external scripts.
3. Continuous Script Monitoring
Watch payment flows for unexpected script loads, new outbound requests during checkout, and Document Object Model (DOM) manipulations of sensitive fields.
Downsides: Alert fatigue causes real threats to be missed. High false positive rates flag legitimate behavior as malicious. It requires resources and maintenance.
4. Payment Frame Isolation
Remove checkout pages from attacker reach via sandboxed iframes.
HTML
<iframe src=”https://secure-payments.yoursite.com/checkout”
sandbox=”allow-forms allow-scripts”
allow=”payment”></iframe>
Dropping “allow-same-origin” cuts malicious access back to the parent page.
Downsides: Payment frame isolation adds checkout complexity, limits customization, and creates implementation challenges for parent-frame communication.
5. Change Detection: Deep Behavioral Analysis
Deploy agentless defenses that identify risks such as formjacking attacks on checkout pages, tracking pixels transmitting data to foreign servers, or suspicious script behaviors.
Alerts about script changes during code freezes could add additional security.
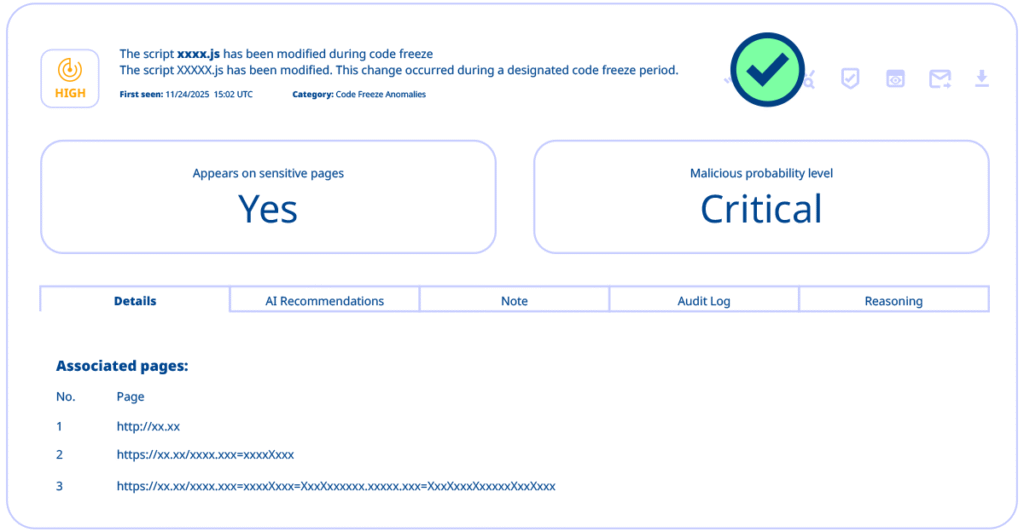
The team gains visibility into every script change during a code freeze and decides the most efficient reaction.
Downside: Behavioral detection can produce false positives since defining “normal” behavior as baseline can be challenging and requires some ongoing tuning.
From Code Freeze to Proactive Resilience
Relying solely on code-level defenses creates predictable vulnerabilities. Dev freezes ensure stability but create blind spots that sophisticated attackers exploit. Attackers are patient; they wait for maximum opportunity and minimum response capability.
Security during critical periods can’t mean halting defenses; it requires shifting from code-based remediation to ongoing, real-time monitoring and active threat management. The challenge isn’t preventing malicious deployment; it’s detecting and neutralizing dormant threats already lurking in your environment.
Defense Beats Reaction
Every minute preparing now saves hours of crisis management during peak revenue. The question isn’t whether third-party risks will surface; it’s whether you’ll be ready without breaking everything else.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







