The Essential SDLC Security Checklist

Cybersecurity threats are evolving faster than technologies and software development processes, and with each new application a user installs on a device, the attack surface grows. A 2022 report from mobile security vendor Zimperium found that a global average of 23% of mobile devices contained malicious applications in 2021. Although one might think that organizations will have the upper hand with rapid technological advancement, unfortunately, this isn’t always the case.
There are many ways hackers can compromise devices for reconnaissance or to gain full access to the corporate network resources as if they were authorized users. Ransomware and malware are well-known examples, but flawed code and leaky apps can also set the stage for a breach and further damage. Poor programming practices and flawed code can enable the public, including attackers, to see application data such as corporate information and passwords.
That lesson was clear in 2021 when Slack identified a bug in its Android app that logged cleartext user credentials on devices. The company warned users to change their passwords and purge the application data logs, but the doors were by then wide open to attackers seeking corporate information. More recently, the Beijing 2022 Olympics app, which was compulsory for all attendees, was found to have flaws that could make it easy for hackers to steal sensitive personal information, cybersecurity researchers in Canada warned. To protect against flawed code and leaky apps, organizations must foster secure coding practices and incentivize developers to implement security as an essential part of the SDLC.
In this blog, we look at what SDLC Security entails before discussing in detail the checklist to ensure a Secure SDLC.
What is SDLC Security?
SDLC, or Software Development Life Cycle, is a systematic process of building software by defining a set of rules from start to end continuously. There have been multiple SDLC models, including the most recent and effective DevOps.
SDLC Security is a framework for building a secure application by making security a core development requirement right from the app’s inception.
Why do we need SDLC Security?
In simplest terms, SDLC security is important to make your application bulletproof (or as close to it as possible). Traditionally, businesses used to release applications, wait till they identify a bug or security challenge, and then address the issue. This led to disastrous results for businesses (reputation loss, financial burden through fines, and risk of a permanent shutdown) and their customers (identity theft, monetary loss, and privacy intrusions).
Against this backdrop, the benefits of a secure SDLC include:
- Security as a continuous process and not a one-time checkpoint
- Effective collaboration between all stakeholders
- Vulnerability detection or logic flaws early in the development process
- Reduces business risks and other damages
- Early detection improves efficiency and software development velocity
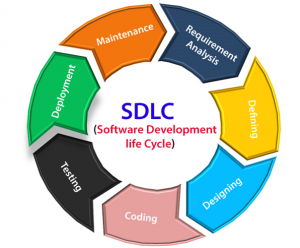
7 Phases of SDLC
SDLC is a process where you outline each stage and the tasks within that stage. This approach increases process efficiency and resource productivity. The different phases of SDLC are:
1. Planning
Project stakeholders define cost, timelines, targets, team building, and leadership structure. Planning also involves gathering feedback, recommendations, and suggestions from leaders, customers, experts, and other invested parties.
2. Requirements
Teams are assigned to individual parts of the project, and requirements are defined in terms of what the application is expected to do, its features, and it’s functionalities.
3. Design
The design of the software is essentially modeling how the software will work. Its elements include architecture, user interface, platforms, programming, and security practices.
4. Development
Developers write the code of your application. Although different teams work on individual parts of the project, they use source code management tools to keep track of code changes and collaborate.
5. Testing
After the source code is prepared, it is run through a series of tests to identify any flaws, security threats, and bugs. Eliminating glitches and other issues will increase user satisfaction.
6. Deployment
Make your application available to users through a downloadable application or website link.
7. Maintenance
Although the development cycle practically ends with deployment, bugs could have passed through the cracks during testing. Maintenance helps to ensure interruption-free service to your customers.
SDLC Security in eCommerce & Finance
In both eCommerce and financial services, time-to-market is a make-or-break factor. For this reason, almost every player in these industries has adopted DevOps practices to accelerate product and feature releases significantly.
However, faster product releases pose a significant challenge for security teams. eCommerce businesses and financial institutes are prime targets for cyber attackers due to the direct monetary transactions they manage. To avoid serious damage, enterprises must implement security as a foundational element for their SDLC.
Below are four essential best practices:
- Establish security requirements for your applications
- Identify potential gaps and risks
- Align development and security teams
- Perform a comprehensive security analysis to identify risk-prone areas
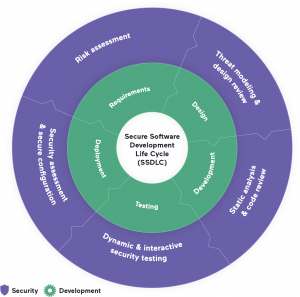
Checklist to Create Secure Software Development Lifecycle (SSDLC)
Build security into each step of the cycle
Rather than being seen as a roadblock in SLDC, security should be baked into each step of the development process in order to accelerate it. Keeping security in mind at every stage of the development process includes:
- Assessing risks during the requirements listing stage
- Reviewing design
- Analyzing the architecture for potential risk during the design phase
- Performing both static analysis and dynamic analysis
- Interactive application security testing during the development and testing stages
Your development team must be aware of the secure coding practices and security frameworks. This ensures consistency and helps you define a uniform security policy at an enterprise level.
Include security requirements in the planning phase
Along with business, performance, and functional requirements, your development team must also gather security requisites from all the stakeholders before the development process begins.
With respect to security, you will decide on technologies and languages to use along with best practices to detect and manage vulnerabilities and other hostile code.
This stage also includes ascertaining if the frameworks are secure with the application environment and checking for compatibility of technologies and languages. All the prerequisites must be properly addressed since running into these issues later could lead to development complications and possibly expose your software to security attacks.
Oftentimes, security requirements are tied up with functional specifications. For example, if the functionality needs a user to enter their password before accessing their account, a security consideration can be that the letters they input become encrypted.
Prevent downstream security issues with secure design
Software designing is a phase where you document how your software product and its features should be built to align with the technical and business requirements. Developers will use this document to write the source code.
In terms of security, this forms a critical stage. You must review the code and the design properly to mitigate software defects leading to security risks. If left unresolved, these issues don’t appear in the testing phase since they don’t qualify as bugs.
Security review methodologies like architecture risk analysis (ARA) and threat modeling help you identify flaws in your design. While ARA ensures that your design meets the security principles, threat modeling detects any loopholes in the design that hostile agents can leverage to harm your system.
Follow secure coding guidelines and perform code quality reviews
Conducting an efficient security review of source code is important to weed out any vulnerabilities. The code quality review primarily checks logic errors, specification flaws, and style guides, among other defects. It is done through an automated tool, which scans your source code based on predefined rules, and inspects for insecure code.
Secure coding guidelines are technology-agnostic security rules that must be included in the software development process. It is crucial to implement secure coding practices to avoid cyberattacks. Some of these guidelines are validating inputs from untrusted sources, designing and implementing security policies, following multiple defense strategies, executing the least privilege approach, and adhering to quality assurance techniques.
Test, test, test
Although you have run multiple security checks at different stages of the process, code testing happens once the code is completed. Once the modules are sent for testing, they are subjected to multiple test paradigms, including security testing, to detect and highlight vulnerabilities. You can employ scanning tools for a variety of tests, such as:
Static analysis: SAST ( Status Analysis Security Testing) tests your source code before it is compiled. It detects vulnerabilities and security risks that could open up your application to potential attacks.
Dynamic analysis: DAST (Dynamic Analysis Security Testing), involves vulnerability investigation while the application is in production, usually testing HTML and HTTP interfaces.
Interactive application testing: Unlike SAST and DAST, this is a functional test that interacts with your application via an automated bot, human tester, or any other type of simulated interaction.
Penetration testing: In this test, you evaluate the security of your application by stimulating an attack using tools, techniques, and processes that real-life cyber attackers use.
Keep up with the latest threats
With evolving technology, cyberattack practices also evolve. Therefore it is critical to keep yourself up to date with security issues. Although there are no fixed guidelines on how to do that, you can follow simple practices to ensure that you are always in the know-how of the latest threats on the scene:
- Follow security experts as they usually spend the majority of their efforts on researching cybersecurity issues. Subscribing to their blogs, newsletters, podcasts, and other updates they release is a good idea.
- Do your own research into the cyberattacks ecosystem. Although it might not be possible for you to dedicate as much time to this as experts, you can read through every reported attack, such as the Log4j vulnerability, and pore into the details.
- Attending cybersecurity events is also a great way to learn new trends. Engaging in such events will also help you build a network of security professionals who can collaborate and share knowledge on software security.
Better software security without the additional overhead
Current market demand for improved security has pushed SDLC security to the forefront. Security and reliability are two of the most important factors for delivering a successful application.
However, building a secure application demands a security-driven approach to software development, and including security best practices as an inherent part of the process can be fairly straightforward.
We’re helping businesses just like yours ensure the security of their web applications with our cybersecurity platform. It eliminates the hassle of managing multiple tools. Our management dashboard allows one-window deep visibility into all your digital assets, components, and supply chain. If you’re interested in better adherence to your SDLC security, Reflectiz can be a great support.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!