The Complete List of Data Security Standards

Concerned about data security? You’re not alone. With the proliferation of digital technologies, businesses are collecting and processing more data than ever. Data breaches are rising. While 45% of breaches were credited to malicious activities, 22% were due to casual errors. That’s a lot of sensitive information falling into the wrong hands.
But data security isn’t just about protecting sensitive information from hackers. It’s also about staying compliant to protect personal information. If you’re a business owner or decision-maker, you know how complex and constantly evolving regulations can be. That’s where data security standards come in.
Let’s look at data security standards, how they differ from regulations and frameworks, and which data security standards e-commerce and finance businesses should be aware of today. We’ll also provide tips on choosing the relevant standards for your organization and staying compliant.
What are data security standards and regulations?
Data security standards are guidelines, or criteria organizations can follow to protect sensitive and confidential information. These standards can help prevent unauthorized access, use, disclosure, disruption, modification, or destruction of data.
Many different data security standards have been developed by various organizations and agencies, such as the:
- International Organization for Standardization (ISO)
- National Institute of Standards and Technology (NIST)
- Payment Card Industry Data Security Standard (PCI DSS)
In addition to data security standards, there are also various data protection regulations that organizations may need to comply with, depending on their location and industry. These regulations establish legal requirements for handling and protecting personal and sensitive information.
Examples of data protection regulations include the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States.
Data security standards and regulations are particularly important for e-commerce and financial services businesses as they handle sensitive customer information regularly. Failing to comply with these standards and regulations can lead to serious consequences such as fines, legal action, and damage to an organization’s reputation. These businesses need robust data security measures to protect their customers’ information and remain compliant.
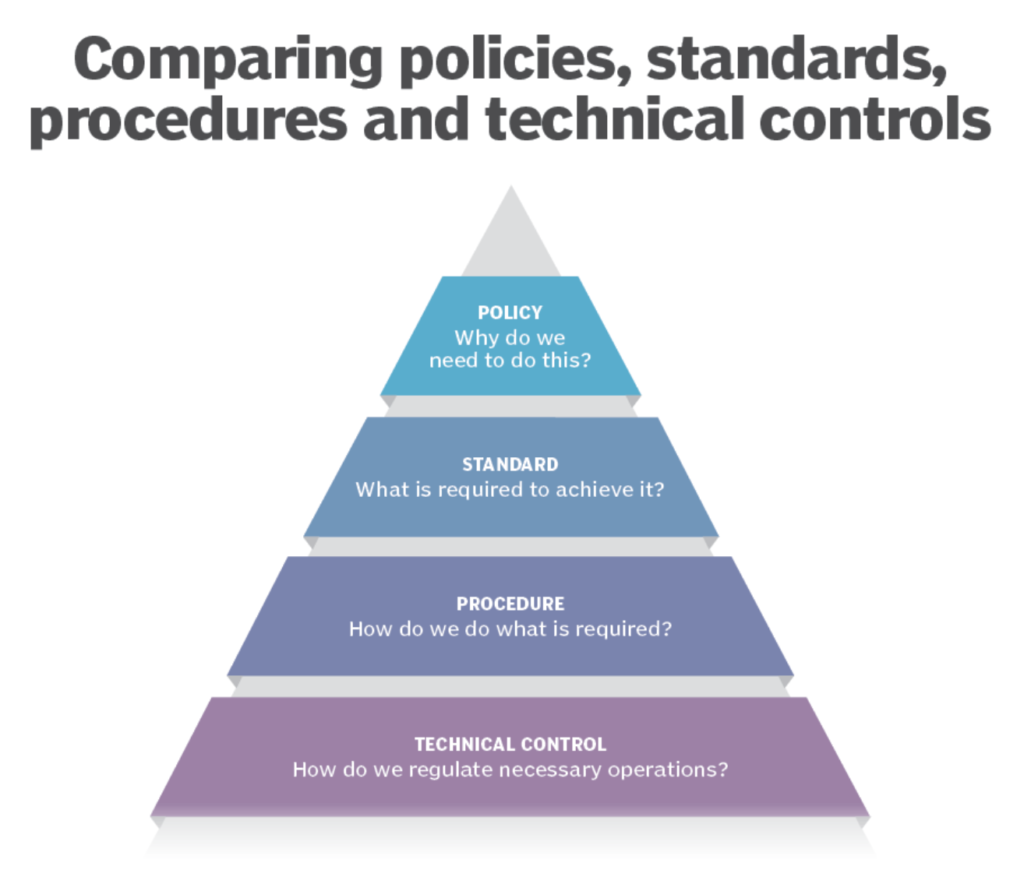
Security standards vs. IT security frameworks
Security standards are a set of criteria organizations can follow to protect sensitive and confidential information. Different standards are developed by various organizations and agencies, such as the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST).
Some of these standards are mandatory, while others are voluntary and recommended as best practices.
IT security frameworks fall under a broader category. These encompass sets of policies, procedures, and guidelines that organizations can use to secure their information systems and protect against cyber threats. They’re usually not required by law and tend to be developed and maintained by organizations or third-party vendors.
The main difference between IT security frameworks and security standards is scope. Security standards can be very specific, focusing on particular aspects of data protection. Security frameworks provide a more holistic approach to information security and consider a wider range of security issues, providing a structure for addressing them.
While different, security standards and IT security frameworks can overlap. For example, an organization might use a specific security standard as a guide for implementing its security framework, or it might use a security standard to ensure its security framework is aligned with industry best practices. The common goal is to help organizations protect their information systems and data from threats and ensure their information’s confidentiality, integrity, and availability.
Why do data security standards matter?
Imagine you’re running an e-commerce business that processes online payments. If you don’t have solid data security measures, your attack surface could be vulnerable, potentially compromising your customers’ payment information. This could lead to financial losses for your business and your customers, not to mention damage to your reputation.
By following data security standards like the Payment Card Industry Data Security Standard (PCI DSS), you can protect your customers’ payment information and make sure you’re handling this data in a secure and compliant way.
How to choose the right data security standards for your organization
Regarding security, the motto “less is more” doesn’t feel appropriate, but navigating all the different standards available can be daunting. To help, we’ve listed a few things to keep in mind when choosing the relevant ones for your business:
- Location and industry: Different countries and regions have different laws and regulations regarding data protection, so it’s important to ensure you’re following the right ones where your business operates. For example, if you’re in the EU, you’ll need to follow the GDPR and industry-specific regulations, such as SOX or GLBA, for financial services.
- Nature of your business: The type of information you need to handle depends on the nature of your business and will require specific protection and controls. If you’re an e-commerce that processes online payments, you’ll need to follow the PCI DSS. And if you handle sensitive healthcare information, you might need to follow the ISO 27799 standard.
- Other factors: The size and complexity of your organization, your budget, resources, and your overall risk profile are also important considerations.
- Beyond your walls: What do your customers expect regarding data protection? Even if not mandated by law, following security standards and frameworks can help your company to establish trust and confidence.
The complete list of data security standards
There are many different data security standards, each designed to address specific risks and protect different types of information. Here’s a list of data security standards to help you navigate through your options:
- ISO 2700 Series: This series of standards cover a wide range of information security topics, including risk management, security controls, and security management systems. Some specific standards within the series include:
- ISO 27018 provides guidelines for the protection of personal data in the cloud.
- ISO 27031 guides on developing and implementing disaster recovery plans for information and communication technology (ICT) systems.
- ISO 27037 provides guidelines for collecting and protecting digital evidence during a cyber incident.
- ISO 27040 provides guidelines for protecting stored data, including data stored in the cloud.
- ISO 27799 provides guidelines for protecting personal health information (PHI).
- NIST SP 1800 Series: The National Institute of Standards and Technology (NIST) is a U.S. government agency that develops standards and guidelines for various industries, including information security. The SP 1800 series covers various aspects of information security, including risk management, incident response, and supply chain security. Some specific standards within the series include:
- NIST SP 800-53, which provides guidelines for the selection and implementation of security controls for federal information systems.
- NIST SP 800-171 provides guidelines for protecting controlled unclassified information (CUI) in non-federal systems and organizations.
- NIST Cybersecurity Framework (CSF) provides a common language and guidelines for managing cybersecurity risks. It is designed to be flexible and adaptable to the needs of different organizations.
- COBIT: The Control Objectives for Information and Related Technology (COBIT) is a framework developed by the Information Systems Audit and Control Association (ISACA) that provides a set of best practices for the governance and management of information and technology (IT). It covers many IT-related topics, including risk management, security, and compliance.
- CIS Controls: The Center for Internet Security (CIS) is a nonprofit organization that develops best practices for securing IT systems and networks. The CIS Controls are 20 cybersecurity best practices designed to be prioritized and implemented based on an organization’s risk profile.
- HITRUST Common Security Framework (CSF): The Health Information Trust Alliance (HITRUST) is a nonprofit organization that develops a set of best practices for protecting sensitive health information. The HITRUST CSF is a framework that provides a set of guidelines and requirements for securing electronically protected health information (ePHI).
- General Data Protection Regulation (GDPR): The GDPR is a data protection law that applies to organizations operating in the European Union (EU) and European Economic Area (EEA). It sets out specific requirements for collecting, using, and protecting personal data and gives individuals the right to control their data.
- COSO: The Committee of Sponsoring Organizations of the Treadway Commission (COSO) is a joint initiative of five private sector organizations. It aims to improve corporate governance and provide guidance on risk management. COSO has developed a framework called the “Internal Control Integrated Framework” that provides a set of principles and guidelines for managing risk and improving internal control in organizations.
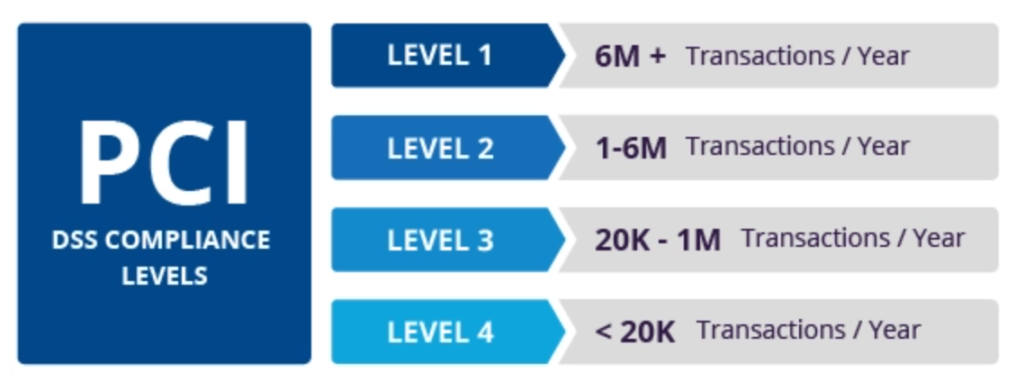
- PCI DSS (Payment Card Industry Data Security Standard): The PCI DSS is a set of security standards that apply to organizations that accept, process, store, or transmit payment card data. It is designed to ensure that sensitive payment card information is handled securely and reduce the risk of data breaches. The PCI DSS is particularly relevant for e-commerce businesses that process online payments.
- The PCI DSS v4 (Payment Card Industry Data Security Standard) is the latest version of the PCI DSS, a set of security standards that apply to organizations that accept, process, store, or transmit payment card data. It is designed to ensure that sensitive payment card information is handled securely and reduce the risk of data breaches. One of the key changes in PCI DSS v4 is an increased emphasis on the need to protect public-facing web applications. Reflectiz supports PCI DSS v4 by using behavioral analysis to identify and mitigate risks on customers’ websites, focusing on protecting against client-side attacks that originate in users’ browsers.
- SOC 1: The SOC 1 standard is designed to help organizations assess the internal controls related to their financial reporting. It covers controls that are relevant to the financial statements of an organization, including controls over financial reporting (ICFR) and controls at a service organization relevant to user entities and their internal control over financial reporting (ICFR).
- SOC 2: The SOC 2 standard is similar to the SOC 1 standard, but it focuses on a business’s non-financial reporting controls related to information security, availability, processing integrity, confidentiality, and privacy. It is typically used by organizations that provide cloud-based or other outsourced services.
- SOC 3: Intended for a general audience and provides a summary of the results of the SOC 2 assessment. It is often used as a way for organizations to demonstrate their commitment to information security and trustworthiness to their customers.
- SOC for Cybersecurity: Introduced in 2020, it is designed to help organizations assess their cybersecurity risk management practices and controls.
- SOC for Supply Chain: Also introduced in 2020, it is designed to help organizations assess the internal controls of their supply chain partners and ensure that they are meeting the necessary controls and requirements.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): SSL and TLS are cryptographic protocols that are used to secure communication over the internet. They are particularly relevant for e-commerce businesses, as they are often used to secure online payment transactions. SSL and TLS work by encrypting the data transmitted between a client and a server, making it difficult for third parties to intercept and read the transmitted data.
- SOX (Sarbanes-Oxley Act): The Sarbanes-Oxley Act (SOX) is a U.S. law enacted in 2002 in response to a series of corporate accounting scandals. It sets out specific requirements for publicly traded companies’ financial reporting and internal controls and requires them to have independent audits of their financial statements. SOX is particularly relevant for financial services companies, as it applies to publicly traded companies, and many financial services companies are publicly traded.
- GLBA (Gramm-Leach-Bliley Act): The Gramm-Leach-Bliley Act (GLBA) is a U.S. law enacted in 1999. It sets out specific requirements for protecting personal financial information held by financial institutions and requires them to disclose their information-sharing practices to their customers. The GLBA is particularly relevant for financial services companies, as it applies to any company that offers financial products or services to consumers.
- The Federal Information Security Management Act (FISMA) is a U.S. law enacted in 2002. It sets out specific requirements for protecting federal government information and systems and requires federal agencies to implement and maintain information security programs. FISMA also requires agencies to report on their information security posture and to certify and accredit their information systems.
FISMA is particularly relevant for financial services companies that do business with the federal government, as it sets out the information security requirements they must meet to conduct business with the government. It is also relevant for financial services companies that handle sensitive government information, as it sets out specific requirements for protecting it.
Don’t let them keep you up at night
Staying compliant with data security standards can be a daunting task. With so many different standards and regulations to consider, and with these standards and regulations constantly evolving, it can be difficult to keep up. That’s where automated solutions like Reflectiz come in.
Reflectiz is a SaaS solution that helps e-commerce and financial services businesses conduct business online while staying compliant with regional and industry regulations and preventing cyber-attacks. It does this by identifying and mitigating customer website risks using behavioral analysis.
By creating an inventory of all digital applications on a website, Reflectiz maps out their impact and identifies any potential compliance issues and vulnerabilities. This allows you and your team to prioritize and remediate issues in real-time, ensuring that your website is secure and compliant. Don’t let data security compliance keep you up at night–Sign up for a free version today.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!