C2 Server: The Brain of Client-Side Attacks Exposed

The term “C2 server,” short for “command and control,” may not be widely recognized, but it’s the central command post for cyberattacks. Like a shadowy general, malicious actors utilize C2 servers to direct compromised devices, ranging from individual computers to entire networks, in carrying out their digital assaults. In the past, malevolent agents operated physical C2 servers, but today, they’ve embraced the cloud, covertly utilizing cloud providers.
This article explores the world of C2 servers, their functions, cybercriminal tactics, and the pressing need for robust cybersecurity defenses.
What is a C2 Server?
C2 is short for command and control, a term that has military roots. A C2 server is one that a malicious actor uses like a general on the battlefield to command and control other machines–often whole networks of them–to carry out cyberattacks on their chosen targets. In the past, bad actors frequently ran their own physical C2 servers, but nowadays they are more likely to use cloud-based machines.
Functions of a C2 Server
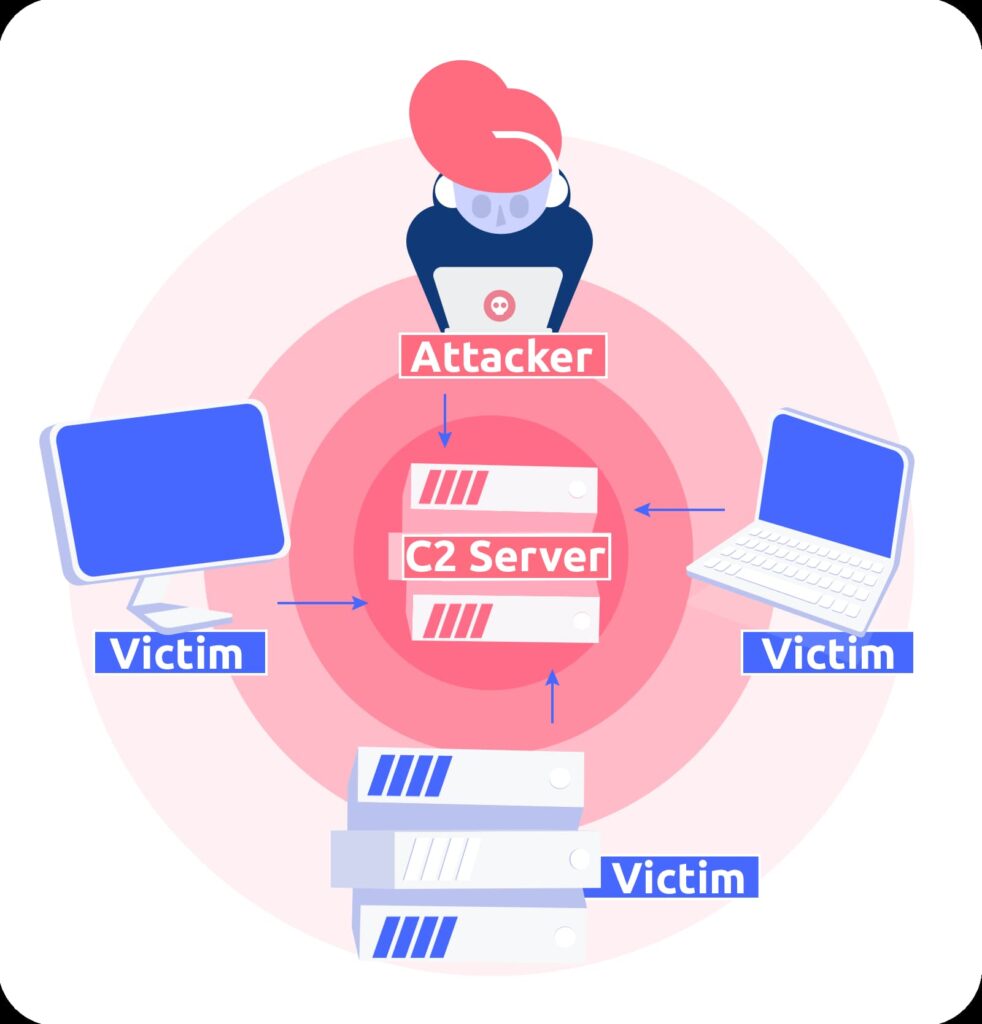
The C2 server’s job is to allow attackers to communicate with compromised devices such as desktop computers, IoT devices, tablets, phones, etc. Compromised means that they have already been infected by the attacker’s malware, which may be introduced when an employee opens a phishing email, for example.
Since C2 servers are provided as a service by legitimate companies, you may be wondering how attackers get to access them. Does AWS offer a Bad Guy tier now? No, attackers rent servers from legitimate cloud providers without them knowing it. The cloud providers do their best to stop them, using dedicated cybersecurity teams to monitor for this kind of abuse, but it’s difficult to stay on top of. They will take down C2 infrastructure as and when they find it, but cybercriminals obfuscate their activities to evade detection, and they will shift their operations frequently to avoid disruption, so defenders face a never-ending cat-and-mouse game.
Cloud Infrastructure: A Cybercriminal’s Advantage
Malware groups will often use cryptocurrencies and disposable accounts which makes it hard to trace them. They are highly motivated to succeed because when they do manage to rent servers from major providers it lends their activities an appearance of respectability that makes them look benign to security tools, and if they can piggyback on the infrastructure of services like Azure, AWS, and DigitalOcean, they get to leverage a robust, reliable, and responsive server infrastructure where it’s easy to spin resources up and down as needed, and with access to a global network, they can also deploy C2 servers that are physically closer to their infected targets for better performance.
One of the cloud’s major selling points is scalability, and cybercriminals will use it to support massive botnets. It’s also true that renting infrastructure is cheaper than buying and maintaining dedicated hardware, so tapping into the cloud not only gives them access to incredible resources, it also means they can launch their attacks more cost-effectively.
What is a C2 Attack?
A C2 server attack usually follows this kind of progression:
Malware infection – The attack starts by infecting the victim’s computers and devices with malware such as trojans or backdoors to establish a foothold.
Command infrastructure – The infected machines then connect back to the C2 server to receive instructions and updates for carrying out malicious activities.
Remote control – The C2 server allows the attackers to remotely control the infected machines on the victim’s network.
Lateral movement – The initially infected points provide access for the attackers to move laterally and compromise additional systems.
Data exfiltration – Sensitive data like credentials, emails, documents, etc., is extracted and transferred back to the C2 server. This traffic is usually encrypted to avoid detection.
Obfuscation – C2 communications are encrypted and disguised as normal traffic and rhe C2 servers are shifted frequently to avoid detection.
Botnet coordination – For large attacks, the C2 server enables an attacker to control and direct a botnet that can include thousands of infected devices.
Persistent access – Even if malware is detected and removed, the C2 foothold allows reinfection to maintain network access.
Manipulate IT – The C2 channel allows attackers to manipulate or disable security tools, destroy backups, or corrupt data.
When connected to a C2 server, attackers can remotely access an infected machine, move laterally through a network, and steal data. Since they’re not keen on advertising their presence, C2 communications are routed through intermediate servers to hide the true source of the attack and are often masked using common protocols. They can be disguised to imitate trusted or unmonitored traffic and blend in with normal web, DNS, or other traffic to avoid detection for as long as possible.
Disrupting connections to C2 servers can disable malware campaigns, but attackers are constantly evolving their tactics and infrastructure to avoid detection.
C2 server infrastructure explained
As we’ve seen, at a high level, C2 servers act as the central nervous system that gives attackers remote control over infected machines. They provide an attacker with real-time command capabilities to orchestrate various malicious activities through the compromised hosts.
As mentioned already, C2 servers facilitate the two-way communication channel between the attackers and infected machines. Compromised systems phone home to the C2 server to send stolen data, receive new instructions, download additional payloads, and update malware configurations. To avoid detection, these C2 communications are encrypted and often masked to blend in with normal web traffic. The servers themselves are typically based on rented infrastructure from legitimate hosting providers and disguised behind a proxy.
For large campaigns, botnet herder servers manage segments of the botnet population while distributed C2 nodes provide redundancy. This infrastructure can scale to support thousands of infected machines.
The location of C2 servers also often shifts between domains and IP addresses to avoid disruption if one gets taken down. This redundant, decentralized, and cloud-based infrastructure is robust and resilient.
Disconnecting compromised hosts from the C2 servers that are controlling them is key to stopping an active attack campaign, but the sophisticated infrastructure makes this an ongoing challenge as attackers continually adapt their techniques.
Examples of C2 servers
Here are some examples of known C2 servers that have been used to coordinate major malware and cyberattack campaigns:
Emotet C2 – Controlling server for the Emotet banking trojan and botnet, used for spreading malware and stealing financial data.
TrickBot C2 – Associated with the TrickBot malware which often serves as an initial vector for large-scale ransomware attacks.
Dridex C2 – Long-running crimeware operation focused on stealing banking credentials and facilitating financial fraud.
VPNFilter C2 – Control server for the VPNFilter malware used to infect home and small business routers for espionage and sabotage.
REvil C2 – Ransomware operation known for extorting large sums from major corporations via ransomware and data theft.
DarkHydrus C2 – Iranian APT group leveraging C2 for targeted phishing, credential theft, and data exfiltration from government and education sectors.
ShadowPad C2 – Backdoor associated with Chinese threat actor groups used to stealthily control compromised Windows systems.
Hafnium C2 – China-linked group that exploited Exchange Server vulnerabilities in cyber espionage operations.
Zeus P2P C2 – Early use of peer-to-peer C2 channels to avoid centralized server takedowns for this banking trojan.
BlackEnergy C2 – Distributed denial-of-service attacks on the Ukrainian electrical grid were launched from this infrastructure.
As you can see, C2 servers provide critical command infrastructure for all types of major cybersecurity threats, from targeted malware to massive criminal botnets.
C2 Server – most common threats
Here are some of the most common threats posed by attackers leveraging C2 servers to direct malware infections:
Data exfiltration – One of the primary goals is to extract sensitive data like credentials, emails, customer records, trade secrets, etc., and transfer it back to the C2 server for the purposes of theft, fraud, or espionage.
Ransomware deployment – C2 channels allow rapid deployment of ransomware across an organization’s network by delivering the encryptor payload to compromised machines.
Financial theft – Banking trojans and other malware under C2 control can manipulate transactions, inject fraudulent ones, and steal funds.
Botnet DDoS – Large distributed denial-of-service attacks can be coordinated by directing all infected machines to simultaneously flood a target, crippling it.
System manipulation – Disabling security tools, destroying backups, and interfering with system logs via C2 allows attackers to cover their tracks.
Lateral movement – C2-controlled malware allows attackers to pivot through the network, expanding their foothold to compromise additional systems.
Remote access – Attacker-controlled remote access to systems makes it easy to manipulate configurations and steal data over long periods.
Malware delivery – Infected hosts under C2 control can be used as launch points to spread malware further via phishing emails, etc.
Reconnaissance – C2 servers collate network maps, system information, credentials, and other intel gathered by malware to facilitate attacks.
Disrupting the C2 infrastructure is key to stopping the expansion and impact of malware infections. But attackers are constantly adapting C2 tactics and security teams often find themselves playing catch up.
How to manage threats from C2 servers
Here are some tips for security teams to counter the C2 threat:
- Real-time monitoring – Use endpoint detection tools and network monitoring to identify traffic patterns to known C2 domains or botnet infrastructure. Many C2 connections hide in SSL traffic.
- Block C2 infrastructure – Block IPs, domains, and URLs that are associated with identified C2 servers. Continuously update blocking as infrastructure shifts.
- Analyze payloads – Inspect network payloads for signatures of known C2 modules and malware families to detect bot infections.
- Restrict lateral movement – Segment networks, limit admin privileges, and implement access controls to constrain the ability of malware to spread between systems.
- Take down servers – Work with hosting providers to suspend identified C2 server infrastructure when possible. Report criminal abuse.
- Remove infections – Isolate and re-image infected systems to eliminate botnet footholds. Revoke compromised credentials.
- Employee training – Educate staff on phishing and malware risks to limit the initial footholds attackers use to establish C2.
- Patch vulnerabilities – Prioritize patching of exploited software vulnerabilities that allow attackers to gain a C2 foothold.
- Review permissions – Audit unnecessary application and network permissions that could enable lateral movement between compromised systems.
Implement additional network security controls –
· Use firewalls and intrusion detection/prevention systems to monitor and block potential C2 communication.
· Monitor network traffic to identify any potential C2 communication or other malicious activity.
· Implement endpoint protection solutions that can detect and block potentially unwanted programs (PUPs) and other types of malware.
· Regularly update antivirus software and other security controls to ensure that they are able to detect and prevent new and emerging threats.
With vigilance and a defense-in-depth approach, organizations can mitigate the havoc attackers attempt to wreak from C2 servers on compromised networks.
How Reflectiz can help to expose C2 servers communicating with your web environment components
Reflectiz creates an automated inventory that maps the behaviors of all the digital assets in your supply chain. As well as notifying you of when new scripts, tags, or apps are added to your website, it can also let you know when they perform suspicious or unauthorized changes, and when they attempt to communicate with suspicious domains.
Once your unique defensive baseline has been established, the platform alerts you to any changes or suspicious activity. It means that you can respond promptly to any attempts to control the devices in your network or send data to unauthorized locations. Reflectiz gives you the insights to stop C2 servers from hijacking your infrastructure. Find out more about how Reflectiz can help keep your business safe from C2 server and other web-based attacks. Sign up for the free version and test drive our tools today.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







