Third-Party Impacts on Financial Websites: Insights and Data
Reflectiz has been active for the last couple of years in the landscape of cyber-security and, particularly web third-party components risk mitigation. Our solution uses machine-learning platform, based on a propriety browser with dedicated profiling and unique analysis methodology. These capabilities allow us to scan the entire third-party inventories for any given website and analyze the data within.
This article was published for the forthcoming Vendor & Third-Party Risk Europe conference, taking place in June 18-19, London, UK. Reflectiz will be co-sponsoring the event. For more details: www.cefpro.com/vendor-risk
The Financial Website Risk Survey
For the upcoming 4th Annual Vendor & Third-Party Risk Europe conference, Reflectiz has been scanning more than 1,500 websites, including the top financial websites worldwide, particularly banks and credit card companies. The data collection was aimed to discover abnormalities and suspicious actions that affect the supply chain process and eventually generate privacy and security risks.
Third-Party Risks Findings
The actual data will remain confidential, but the findings themselves reveal an interesting overview regarding the amount of vulnerabilities and the risks third, fourth and even fifth parties present.
Our research team was focused on several potential instances. These include key-logging, device activation, the presence of unfamiliar external parties and the extensive use of open source code by internal development teams.
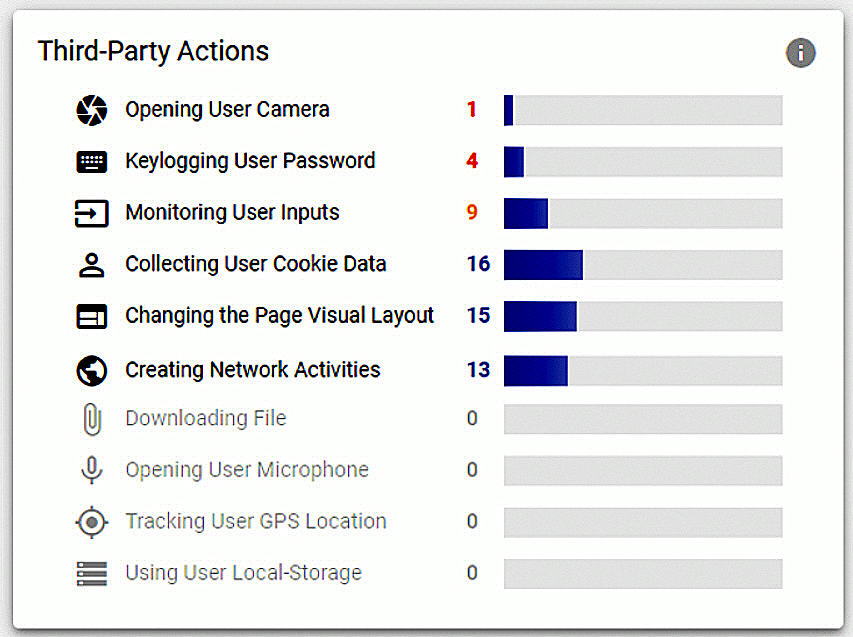
Third-party actions board sample, taken from one of the surveyed websites.
Source: Reflectiz third-party risk scan results, April 2019
What we have discovered so far?
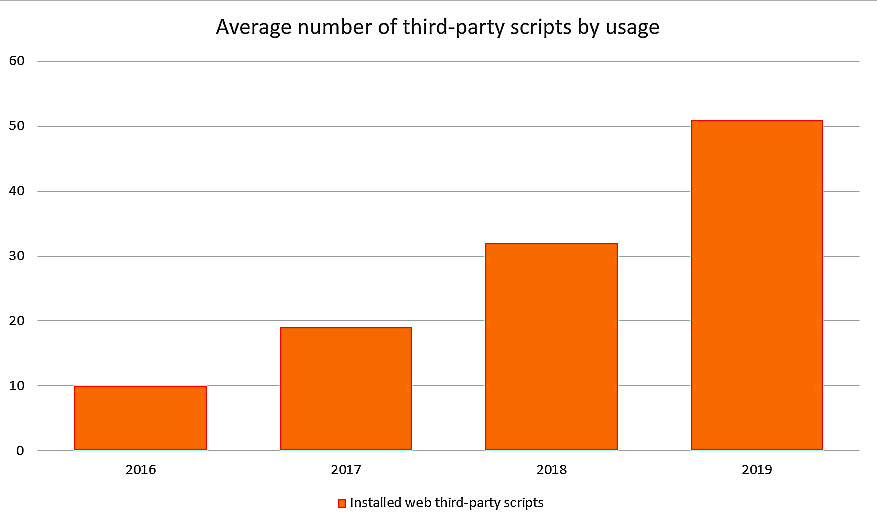
To start with, the average amount of external parties was higher than predicted. Especially fourth-parties and beyond. Our findings indicate that an average website installs above 50 different third-party vendor components. Overall, the most interesting data shows an increasing amount of permissions granted to external components.
Source: Reflectiz 2016-2019
Abnormalities and semi-malicious activities
These types of actions include any suspicious behavior a third-party generates. In some cases, this involves an innocent occurrence, but as we all know the risk is always out there.
Keylogging user input fields
Keylogging – More than 80% of sites surveyed present at least 1 keylogging event. 30% of sites have more than 3 keylogging instances on a permanent basis.
The highest number of keylogging events spotted was 6 in a single site. Keylogging is used on websites to monitor visitors’ behavior, but at the same time it provides third-party vendors access to end-user sensitive data. This instance usually occurs with no monitoring ability or awareness of the website itself.
Third-party device activation
The most popular device activities are GPS, microphone and camera.
According to our estimations, at least 30% of device activities are not mentioned specifically in the terms of service and site’s privacy policy.
GPS activation was found on 18% of sites. This action constantly grows, as the demand for location services is rising, but it has to be dealt carefully.
Microphones are used widely for voice search, voice recognition and enhanced user experience. Typically, those actions are triggered by the end-users, not by external parties. Our findings indicate that 8% websites use this capability. Our research team predicts that the growing demand for voice recognition tools will increase the use of third-party microphone components. Due to the nature of voice recognition, financial websites should take more security precautions to protect themselves and avoid malicious behavior.
Cameras are rarely activated by external parties. According to our findings, this instance occurred only in 5% of sites. By default, website scripts, and third-parties within, cannot activate the device camera without active approval from the user. A third-party will ask a user permit first and will activate the camera only upon approval.
So far, we have presented only a small fraction of data insights collected by our scan platform. We look forward to meet you and share more insights during the 4th Annual Vendor & Third-Party Risk Europe conference.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!