New Case Study: Leeds United Hidden Cyber Attack and Recovery

Learn how malicious code infiltrated Leeds United football club’s online store through trusted third-party services, highlighting the universal threat of Magecart and supply chain risk in the modern web ecosystem. Learn more about this incident in our upcoming live webinar with IT and Security Manager, Graham Peck.
The Attack
At 10 AM on February 24th, two local cybercrime police officers arrived at Elland Road, home of the English Premier League football team, Leeds United. They were there to inform IT and Security Manager, Graham Peck, that the UK’s National Cyber Security Centre (NCSC) had noticed something odd. While monitoring communications between a malicious server and another business six days prior, they had observed that server receiving traffic from the Leeds United online shop.
The NCSC tried to determine what kind of data was being transmitted, but it was encrypted and therefore unreadable. However, they located the script on Leeds United’s website responsible for sending it. To understand its function, they deployed an unencrypted test packet, which revealed the script was scraping credit card data – a clear sign of a data breach.
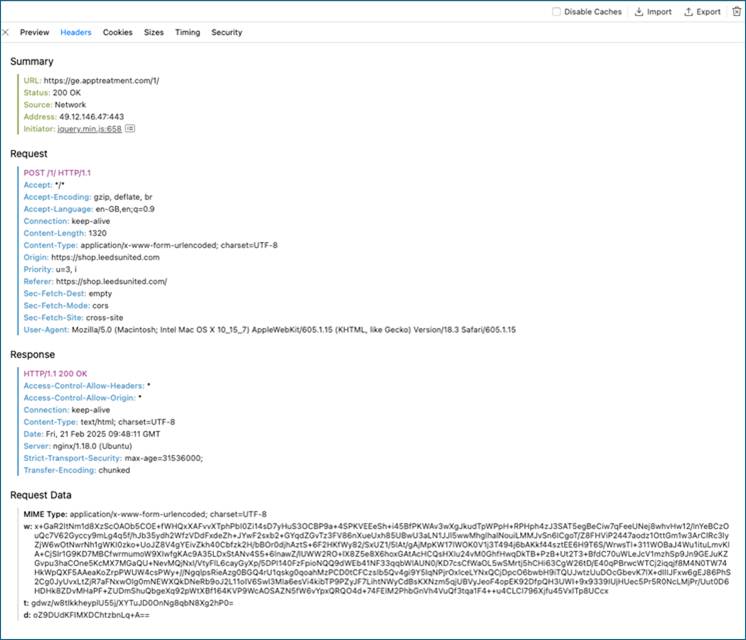
The mystery attackers had deployed a malicious JavaScript skimmer embedded in the checkout page of the club’s webstore. Key technical elements of the attack included:
- Third-party script exploitation: They compromised a third-party service component (possibly a chat widget, analytics tool, or advertising module) loaded on the website, which gave them access to the checkout functionality.
- Client-side execution: The malicious code ran in users’ browsers, effectively circumventing traditional server-side security measures that were powerless to identify the breach.
- Immediate data theft: Customer payment details were transmitted in real-time via hidden channels to servers controlled by the attackers.
The Response
The initial response was swift, as Graham explained. “We took the website down so that we could investigate and locate the code responsible. As soon as we found it, we removed it. Also, the external threat actors had left behind their IP addresses, so we were also able to put blockers in on Cloudflare and several other platforms to stop access from a specific server that was currently linked to the website.”
The Investigation
After finding problematic code on the website, Graham employed a security company to conduct a digital forensic analysis, combing through record logs to understand precisely what had happened. They established that the breach began at 8 PM on February 18th and concluded by 11 AM on February 24th. A small number of transactions had been completed on the website during this period, raising questions about how many had been compromised.
Additionally, Graham recognized the need for a proactive solution to monitor third-party components more effectively. Reflectiz, a specialized web exposure management solution, was already on the horizon as a potential tool to help Leeds United prevent such attacks in the future. While the team worked to contain the breach, the tool would soon reveal deeper security flaws.
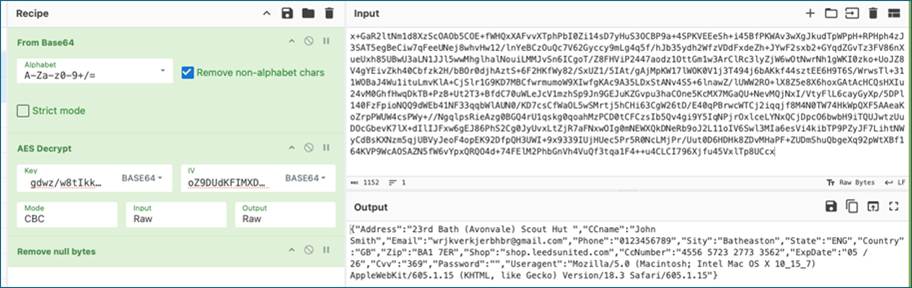
At this point, it’s worth appreciating the sheer amount of good luck that went Leeds’ way during this incident:
- They were lucky that the NCSC spotted the exfiltrated data transmission from its web store in the first place.
- They were lucky that the malicious script was only designed to target credit card details, so any customers using Apple Pay and PayPal weren’t affected.
- Then there’s the six-day window between the breach happening and the business being able to shut it down. Most businesses aren’t so lucky. According to IBM’s 2024 Cost of a Data Breach Report, the mean time it takes to identify a data breach across all industries is 194 days, with containment taking an additional 64 days, a 258-day lifecycle in which attackers are free to inflict all sorts of damage.
A Universal Threat Across Industries
While this particular attack targeted a Premier League football club’s e-commerce platform, the technique used – injecting malicious code through third-party services – is a threat to organizations in every country and across all sectors. Whether they’re in retail, healthcare, finance, education, or government:
- E-skimming can compromise any web application that processes sensitive customer data or payment information.
- Supply chain vulnerabilities, including third-party dependencies, create critical security gaps in web ecosystems.
Graham Peck, Leeds United’s Head of IT explains: “The national crime agency told us there’s a concerted push by threat actors into the entertainment industries. Hostile states are doing everything they can to create discord and disrupt the businesses of their enemies, particularly companies with a large commercial value and extended supply chain, like Marks & Spencer. We heard about one attack recently where a ransomware gang was spying on a victim’s internal communications. A staffer innocently mentioned they had £5 million worth of cyber insurance cover, so that’s what the gang demanded.”
The Resolution
Even though the breach was quickly isolated and affected customers informed, it was far from the end of Leeds United’s security journey; it was just the beginning. The web skimming attack exposed a massive blind spot that needed urgent attention. This led the club to immediately implement Reflectiz across its entire web infrastructure.
In the aftermath, Reflectiz revealed serious shortcomings in the retail website’s prior security. Graham explained that Leeds United had outsourced its retail website management, a common practice that only works with a truly trustworthy and professional third party – which wasn’t their experience. The previous company was responsible for all security mechanisms but provided no visibility or control, leaving Graham effectively “flying blind” with a public-facing, multi-million-pound asset.
Post-Reflectiz Benefits
Immediate Visibility and Evidence
After deploying Reflectiz, Graham gained deeper insight into the security gaps within Leeds United’s website. This allowed him to present clear evidence to stakeholders. “There were a lot of third parties that had too much information, and there were no security headers. All the basic things that you would have expected to be in place as part of a retail website weren’t there. With this tool, I was able to show them. I could send them proof that I didn’t have before, even though I’m not a developer. I don’t have to jump between programs. I can just export information about what I’m seeing and tell them what to fix so that my risk level reduces.”
Streamlined Operations and Smart Alerting
Reflectiz helped streamline the security monitoring process, reducing manual tasks while providing timely and actionable alerts. “In a typical penetration test, you would have to spend time doing things like creating customer accounts, but this was a lot easier. It was up and running very quickly and monitoring continuously,” Graham explained. Unlike some security tools that flood teams with false positives, this solution allowed Leeds United to focus on significant threats. “A lot of systems out there say they’re really good security products. But in most cases, what they do is they create so much noise from alerts that you end up running the risk of not being able to see when you do have an issue, or as we put it, ‘You can’t see the woods for the trees’. With this tool, we can spot problems quickly and act on them, reducing a lot of the time and effort spent on false alarms.”
An Always-On Security Analyst
The tool provided ongoing, automated monitoring, which was particularly valuable for Leeds United’s small security team. “It’s almost like having an additional security analyst on site. I now have peace of mind that there is a system constantly watching for anything abnormal on the third-party website. This solution plugged into my existing security setup with ease and was ready to go. It also revealed hidden supply chain risks that I didn’t know were there.”
Key Takeaways
- Third-party services and supply chain vulnerabilities are a major cybersecurity risk in today’s digital ecosystem.
- E-skimming attacks (like Magecart) can compromise sensitive customer information if third-party components are exploited.
- Early detection and quick action can significantly reduce the scope and damage of a data breach.
- Implementing web exposure management tools can provide ongoing visibility into the health of web applications and prevent future attacks.
- Companies must regularly evaluate their security posture, especially when outsourcing critical website management to third parties.

Watch Graham Peck discuss this incident in detail and share key takeaways for other organizations in our exclusive webinar here
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







