JavaScript Obfuscation: The New Guide to Detection, Deobfuscation, and Defense

Executive Summary: Why JavaScript Obfuscation Matters Now
JavaScript Obfuscation is a double-edged sword in today’s web security landscape. While it can protect intellectual property, it is increasingly used by attackers to bypass traditional security tools, leading to costly da ta breaches and compliance violations. Security leaders must act now to strengthen detection, analyst training, and deploy automated deobfuscation tools.
Key Business Impacts of JavaScript Obfuscation
- 25-26% of malicious JavaScript leverages obfuscation to evade detection.
- Average breach cost reached $4.88 million in 2024, the highest on record
- 55% of phishing emails use JavaScript obfuscation to help cybercriminals avoid detection
- Detection delays: On average, It takes 204 days to discover a breach, plus 73 more days to contain it.
Immediate Actions for JavaScript Obfuscation Defense
- Audit current detection capabilities against obfuscated JavaScript threats
- Implement enterprise-grade JavaScript deobfuscation tools for real-time analysis
- Monitor for high-risk indicators: external URLs, DOM manipulation, delayed execution
What is JavaScript Obfuscation?
JavaScript obfuscation is the process of transforming readable JavaScript code into a version that is extremely difficult for humans (and sometimes machines) to understand, while preserving its functionality. This technique is widely used both for legitimate purposes, such as protecting source code from reverse engineering and for malicious purposes, such as hiding malware or phishing payloads.
Obfuscation turns your code into a puzzle: the pieces still fit, but the picture is nearly impossible to recognize.
Common JavaScript Obfuscation Techniques
String Encoding and Hex Escaping
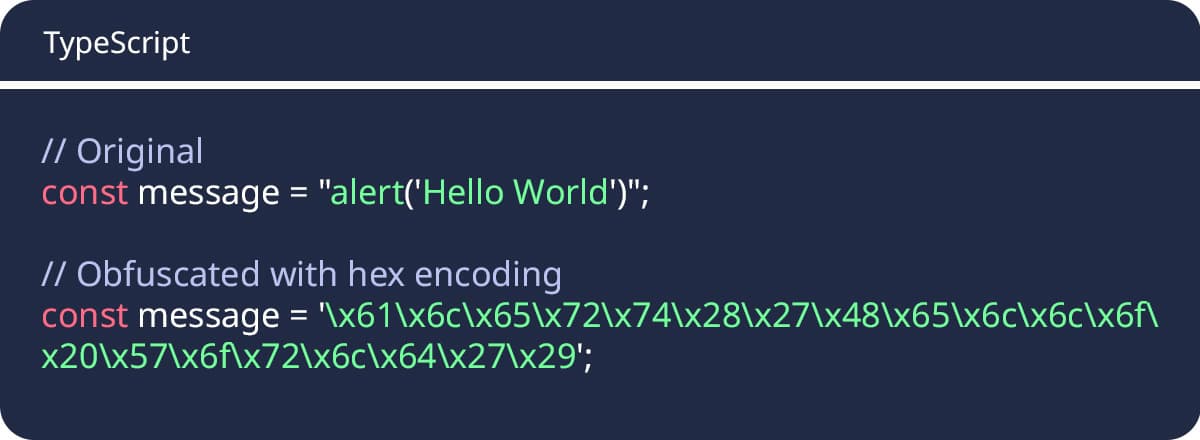
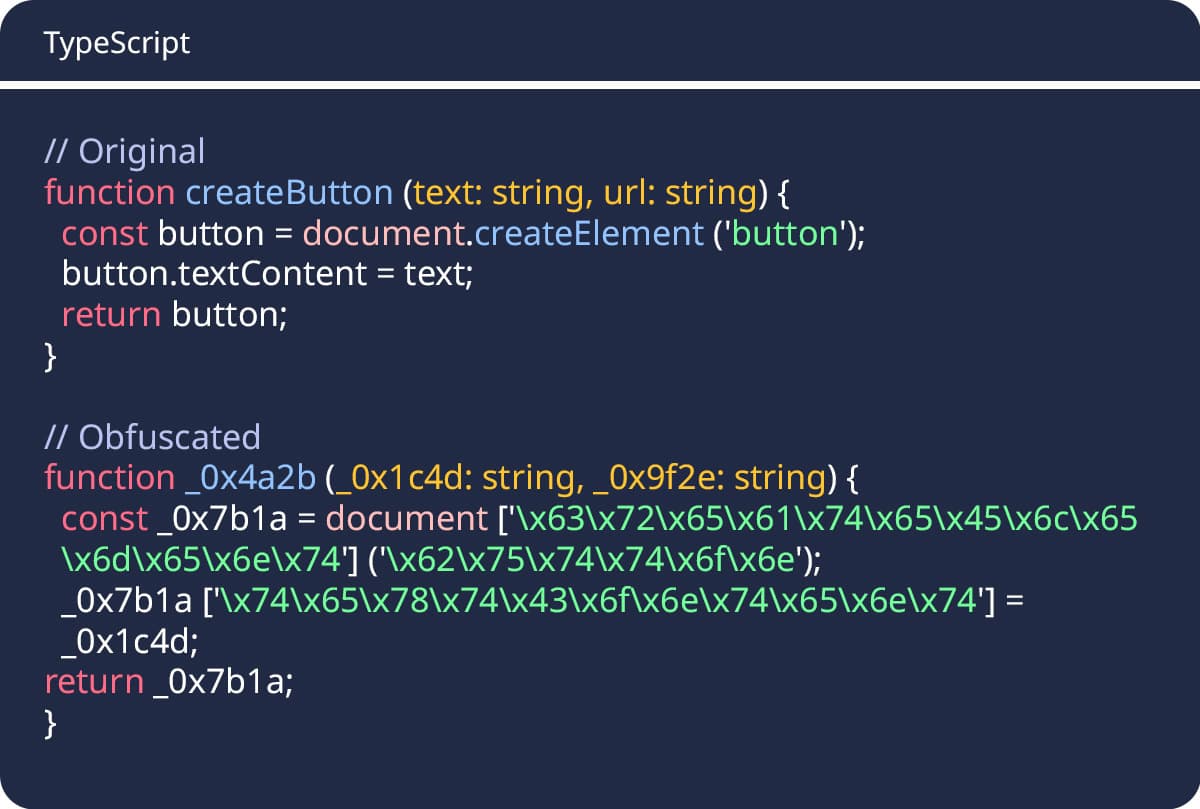
Variable Name Mangling
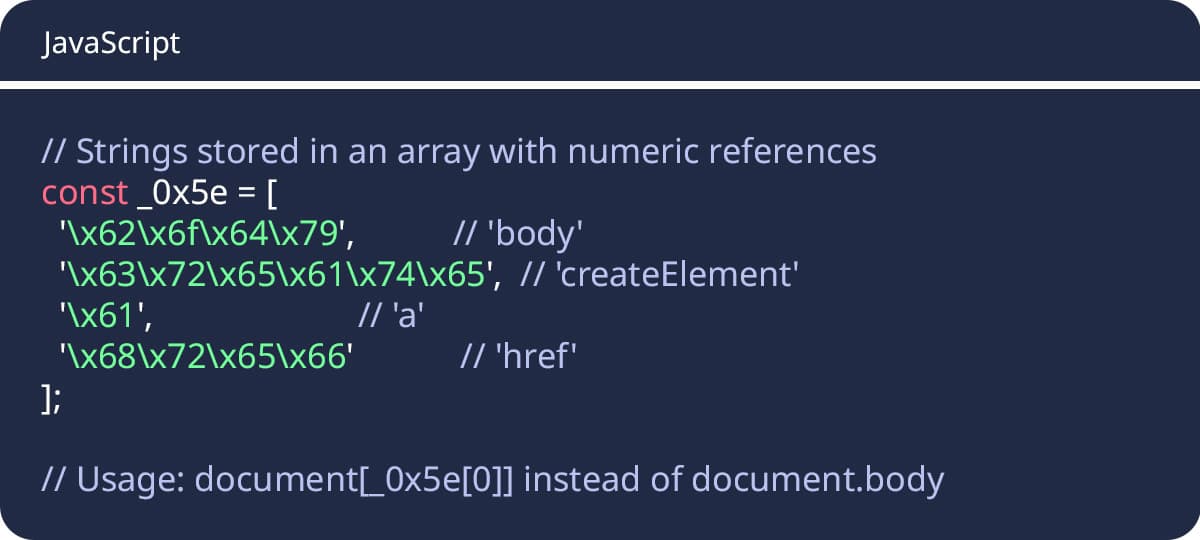
Array-Based String Storage
Advanced JavaScript Obfuscation Techniques
Attackers are constantly evolving JavaScript obfuscation methods. Beyond string encoding and variable mangling, sophisticated techniques include:
- Control Flow Manipulation: Obscuring the logical execution path with dead code, opaque predicates, and function flattening.
- Dead Code Insertion: Introducing code that never executes to mislead analysts.
- Opaque Predicates: Conditional statements that always resolve the same way, but appear ambiguous.
- Function Flattening: Restructuring code execution order to confuse reverse engineers.
Understanding these advanced JavaScript obfuscation tactics is crucial for security professionals.
The JavaScript Deobfuscation Process
Deobfuscation is the reverse engineering process that reveals the original intent of obfuscated code. Security professionals use various techniques and tools to analyze suspicious code.
Real-World JavaScript Deobfuscation Example
Let’s walk through a complete deobfuscation analysis using a real example discovered by security tools. This demonstrates the step-by-step process security analysts use to understand obfuscated threats.
Original JavaScript Obfuscated Code:
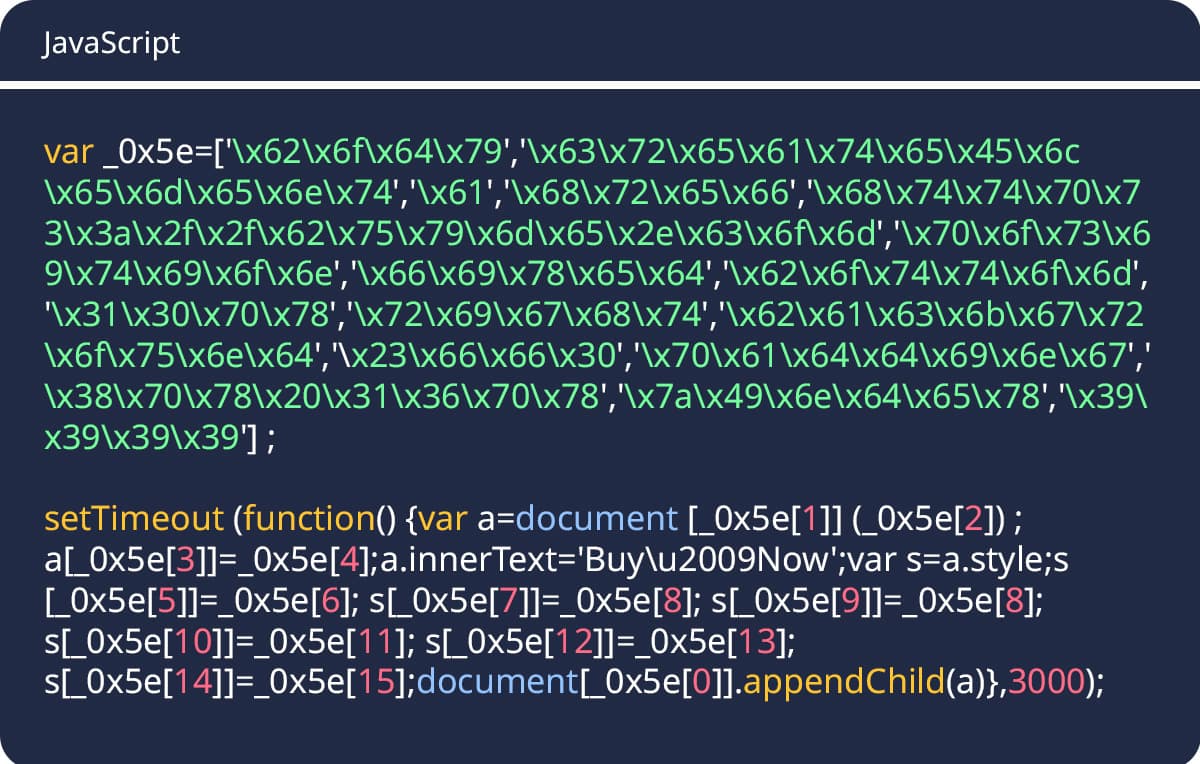
Step 1: Decode the String Array
First, we decode each hex-encoded string in the array:
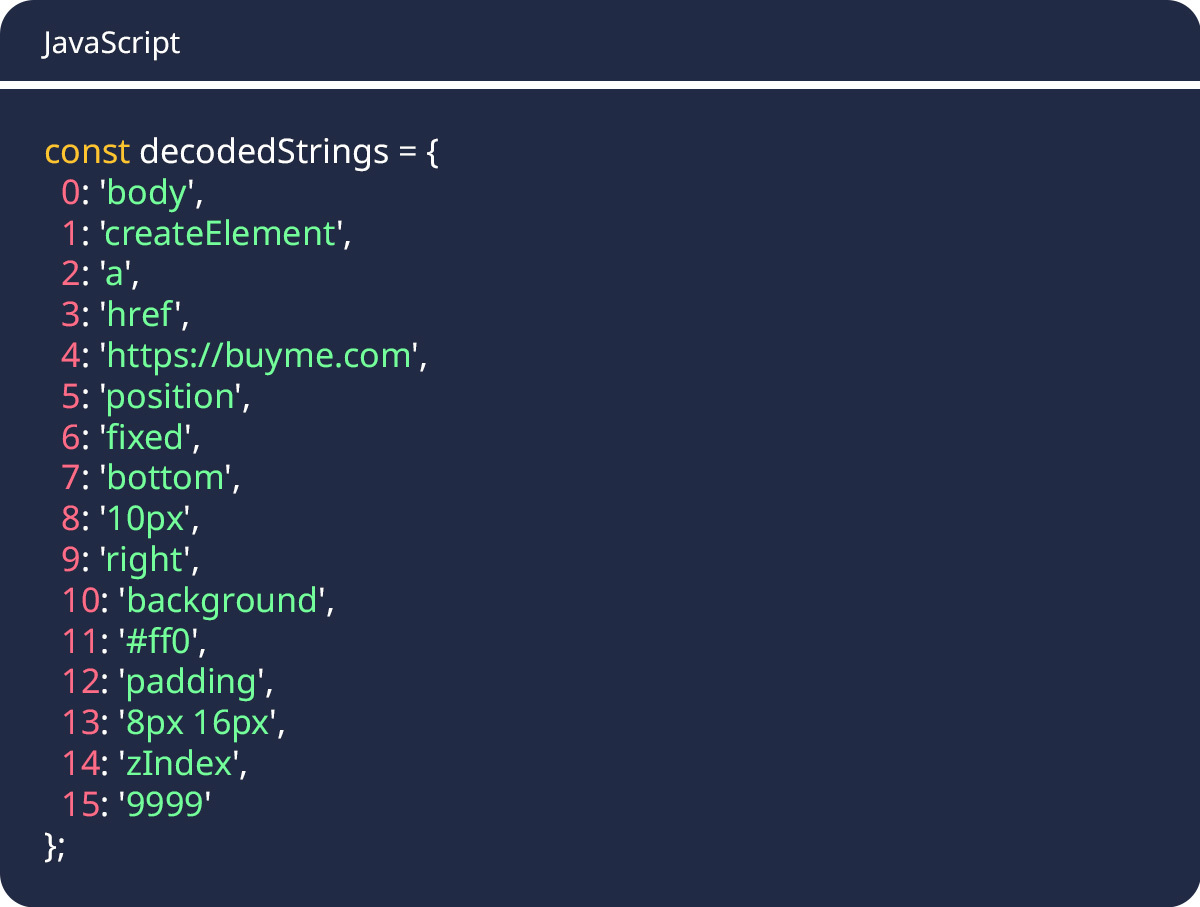
Step 2: Substitute Array References
Next, we replace the array references (like _0x5e[1]) with their actual decoded values. For example, document[_0x5e[1]](_0x5e[2]) becomes document[‘createElement’](‘a’), which simplifies to document.createElement(‘a’).
Here are the key substitutions:
- _0x5e[1] becomes ‘createElement’ (DOM element creation method)
- _0x5e[2] becomes ‘a’ (Anchor tag)
- _0x5e[3] becomes ‘href’ (Link destination property)
- _0x5e[4] becomes ‘https://buyme.com’ (External URL – SECURITY CONCERN)
- _0x5e[0] becomes ‘body’ (Document body for injection)
Step 3: Analyze Control Flow
Finally, we break down the execution sequence to understand the script’s behavior:
- Step 1: setTimeout(() => {…}, 3000)
- Security Risk: Medium
- Explanation: A 3-second delay suggests an evasion technique, attempting to bypass quick scans or human observation.
- Step 2: const ad = document.createElement(‘a’)
- Security Risk: Low
- Explanation: Creating an anchor element for subsequent injection into the DOM.
- Step 3: ad.href = ‘https://buyme.com’
- Security Risk: High
- Explanation: Setting an external URL for the link. This is a critical indicator of potential malicious redirection or content injection from an untrusted source.
- Step 4: ad.style.zIndex = ‘9999’
- Security Risk: High
- Explanation: A very high z-index is often used for overlay attacks (like clickjacking) or to ensure the injected element is visible above all legitimate page content.
Final JavaScript Deobfuscated Result:
Here’s the clean, readable version revealing the true intent of the obfuscated code:
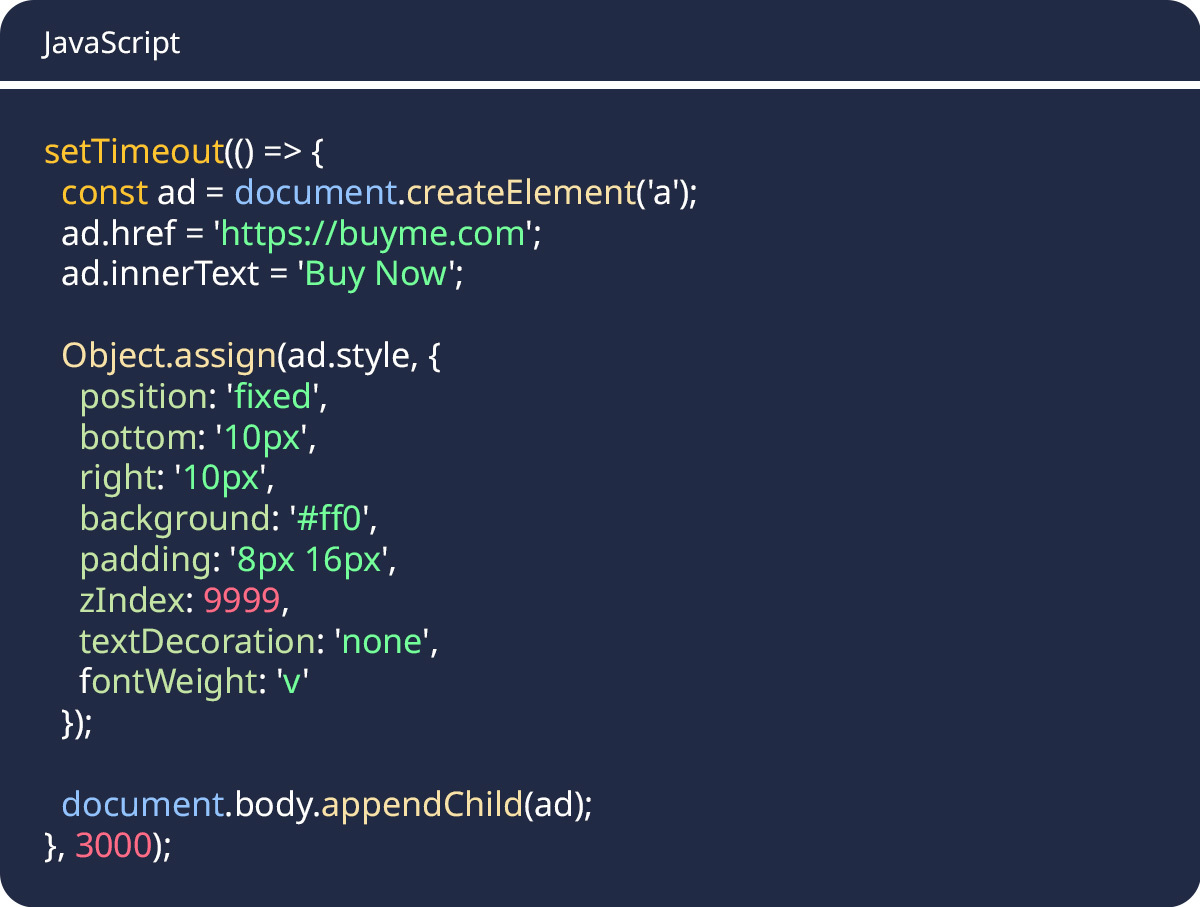
Security Analysis Summary:
This analysis reveals a clear threat of Unauthorized Content Injection.
- Risk Level: High
- Indicators:
- Heavy obfuscation to hide intent
- External URL redirection
- DOM manipulation with high z-index
- Delayed execution for evasion
- Fixed positioning for persistent visibility
- Recommendation: Block execution and investigate the source immediately.
Defense Strategies
Beyond detection, robust defense strategies are essential:
Content Security Policy (CSP) A properly configured CSP can prevent the execution of unauthorized scripts and content injection. Key directives include:
- script-src ‘self’ ‘unsafe-inline’: Restricts script sources to trusted origins.
- object-src ‘none’: Prevents plugin-based attacks.
- base-uri ‘self’: Prevents base tag injection, which can alter relative URLs.
Runtime Monitoring
Monitoring the Document Object Model (DOM) for unexpected changes or the addition of suspicious elements can detect malicious activity even after obfuscation is bypassed.
The code defines a security monitoring tool for web pages that watches for changes in the structure of the page (DOM). Its purpose is to detect potentially malicious behavior, such as suspicious scripts or UI elements being added dynamically.
It continuously observes the page for newly inserted elements. When new elements appear, it checks them for risky attributes (like inline JavaScript event handlers) or if they are styled in a way that could suggest they are trying to cover the page (using a very high z-index). If such suspicious patterns are detected, it logs a warning.
If multiple suspicious elements are found — more than a set threshold — the system triggers a security alert, signaling that the activity might be dangerous or indicative of an attack. This kind of monitoring is useful for detecting things like cross-site scripting (XSS), malicious overlays, or unauthorized dynamic content.
Enterprise-Grade JavaScript Deobfuscation Tools
While manual analysis techniques are valuable for understanding threats, enterprise environments require automated solutions that can handle sophisticated obfuscation at scale. Leading solutions in this space combine traditional pattern matching with machine learning algorithms trained on extensive threat databases.
These advanced deobfuscation platforms often feature:
- Multi-layer analysis methods capable of dissecting complex obfuscation schemes.
- Vast threat databases containing millions of known patterns, continuously updated in real-time.
- AI training, including cutting-edge Large Language Model (LLM) algorithms with specialized deep learning capabilities, for superior threat prediction and analysis.
- High performance, delivering analysis in seconds with high accuracy rates (e.g., 98%) and low false-positive rates (e.g., 2%).
This approach enables rapid analysis that can reveal sophisticated obfuscation techniques and malicious intent in seconds, making it practical for real-time threat detection and client-side security monitoring.
Best Practices for Security Teams
- Automated Analysis Pipeline: Implement enterprise-grade tools that automatically deobfuscate and analyze suspicious code before execution. While free tools exist, they often struggle with sophisticated obfuscation techniques that require more advanced analysis capabilities offered by specialized platforms.
- Behavioral Analysis: Don’t just look at static code – monitor runtime behavior for malicious patterns, especially for third-party scripts.
- Regular Training: Keep security teams updated on new obfuscation techniques and evasion methods.
- Threat Intelligence Integration: Maintain databases of known obfuscation signatures and malicious patterns. The most effective solutions combine human expertise with AI-powered analysis for comprehensive coverage.
- Incident Response: Develop playbooks for handling obfuscated malware discoveries, including escalation procedures for sophisticated threats that require specialized tooling.
Conclusion
Code obfuscation represents a constant cat-and-mouse game between attackers and defenders. While legitimate uses exist, such as protecting intellectual property or preventing code tampering, in cybersecurity contexts, obfuscation often signals malicious intent.
Understanding the techniques, tools, and defensive strategies outlined in this guide empowers security professionals to:
- Quickly identify obfuscated threats.
- Effectively analyze suspicious code.
- Implement robust detection systems.
- Develop comprehensive defense strategies.
The key to staying ahead is continuous learning and adaptation. As obfuscation techniques evolve, so must our analysis capabilities and defensive measures. Modern web exposure platforms, like Reflectiz, are purpose-built to address these challenges by providing real-time visibility, automated deobfuscation, and proactive threat detection for all third-party code running on your website.
Remember: the goal isn’t just to deobfuscate code, but to understand the threat landscape well enough to predict, prevent, and respond to emerging attack vectors effectively.
JavaScript Obfuscation FAQ
Frequently Asked Questions:
How to detect obfuscated JavaScript malware?
Key detection indicators:
- Hex-encoded strings – Look for patterns like \x61\x6c\x65\x72\x74
- Suspicious variable names – Random characters like _0x4a2b or _0x5e
- External URL references – Hidden links to untrusted domains
- Delayed execution – setTimeout() or setInterval() functions
- Unexpected DOM manipulation – createElement() or appendChild() operations
- High z-index styling – Values like 9999 used for overlay attacks
Enterprise tools with AI-powered analysis achieve 98% detection accuracy for these patterns.
What are the best JavaScript deobfuscation tools for enterprise?
Top enterprise deobfuscation tools:
- Reflectiz – Real-time visibility and automated deobfuscation for JS third-party code
- SIEM-integrated platforms – Enterprise security tools with real-time analysis
- JS-Beautifier – Open source basic formatting tool
- JSNice – Machine learning-based deobfuscation
- Synchrony – Academic control-flow deobfuscation tool
Essential features: Multi-layer analysis, low false-positive rates (<2%), threat intelligence integration, proactive threat detection.
Is JavaScript obfuscation always malicious?
No. Legitimate uses include intellectual property protection and license enforcement. However, 25-26% of malicious JavaScript uses obfuscation to evade detection. Security professionals must analyze context, source, and behavior rather than just presence.
What’s the difference between obfuscation and minification?
Minification: Reduces file size for performance (removes whitespace, shortens names) – provides NO security protection Obfuscation: Intentionally hides code logic to prevent reverse engineering – requires specialized tools to analyze
How to prevent JavaScript obfuscation attacks?
6-step defense strategy:
- Implement Content Security Policy (CSP) – Restrict script sources to trusted origins
- Deploy real-time code monitoring – Scan JavaScript before execution
- Maintain third-party script whitelists – Control external dependencies
- Use behavioral analysis – Monitor for suspicious execution patterns
- Integrate enterprise deobfuscation tools – Connect with SIEM systems
- Monitor DOM changes – Track unexpected element injection and high z-index overlays
Can automated tools completely deobfuscate JavaScript?
Automated deobfuscation success rates by complexity level:
- Simple encoding (90%+ success) – Basic hex escaping, string encoding, variable mangling
- Moderate complexity (60-80% success) – Control flow obfuscation, dead code insertion
- Advanced techniques (20-40% success) – Polymorphic obfuscation, custom encoding schemes
Bottom line: Most common obfuscation techniques can be automatically reversed, but complex custom techniques still require manual analysis by security experts.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







