How to Prepare Your Online Business for The New PCI DSS v4

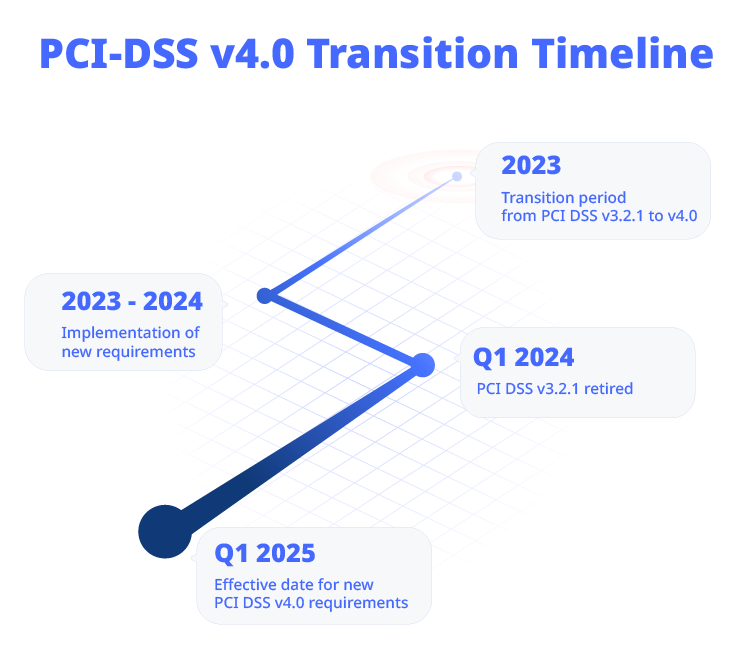
The Payment Card Industry Data Security Standard v3.2.1 will officially be retired on 31 March 2024, and although organizations won’t need to validate the new PCI DSS v4.0 requirements until 31 March 2025, there are two reasons why you need to put in place the security improvements that it outlines.
The first is that implementing the new requirements will ensure that your business achieves a better baseline of technical and operational standards meaning better fraud and data theft protection for your customers. The second is that upgrading your procedures to meet the new requirements now will reveal any areas where you are falling short, but you will still have time to iron them out before the deadline day.
These final months are the time to ensure that you have everything in place, and in this article, we look at how you can best use them to ensure a successful step up to v4.0 for your business.
PCI-DSS v4.0
Hopefully, you already have some sense of what the new standard brings to the table, but if not, you can read our overview of PCI-DSS version 4.0 here to get up to speed.
In short, the new standard brings updates and clarifications for many of the existing requirements and also adds some new ones, including:
• increasing minimum password lengths
• extending the use of multi-factor authentication (MFA)
• broadening the scope to include mobile, Internet of Things (IoT), and cloud applications
• putting greater emphasis on roles, responsibilities, and reporting requirements
But as well as noting these changes, it’s also worth recognizing that they signal a shift in the underlying thinking behind the new standard towards a zero-trust philosophy.
Zero trust is a cybersecurity framework and strategy that operates under the fundamental principle of “never trust, always verify.” It assumes that no user, device, or network component should be automatically trusted, regardless of their location within or outside the network, because cybercriminals will attack using any vector. In a zero-trust architecture, access to resources and data is only granted after they have been thoroughly authenticated and authorized.
As you prepare for v4.0, it’s important to recognize that you’re building the key components of a zero-trust strategy into your business’s DNA, by adding strict access controls, continuous monitoring, identity verification, and the principle of least privilege, which ensures that users and devices only have access to the specific resources they need to perform their tasks.
The Customized Approach
Although the requirements are now more stringent, you also have more flexibility in the way that you meet them. Version 4.0 introduced an alternate option for meeting compliance called the customized approach. This allows businesses to design their security controls to meet the requirements of each objective, which means that you’re free to use solutions such as Reflectiz to help you do that.
You can still use the existing ‘defined approach’ if it suits the business. Organizations have used the defined approach for years to implement and validate PCI DSS requirements and they still can with version 4.0. It may better suit organizations that already have controls in place to meet a requirement and are comfortable with the current methods for validating them. It may also suit organizations that are new to PCI DSS and may be looking for more specific direction on how to meet their security objectives.
If you choose the customized approach it’s important to collaborate with your assessor to ensure that they fully understand your customized controls and that you understand their requirements and what they will be testing.
Resources for change
If you’re ahead of the curve on achieving readiness, the PCI Security Standards Council is encouraging organizations that have already implemented the new controls to have them assessed. Doing so will help you to understand which of your measures are adequate and will also help you to identify and plug any remaining gaps.
If you’re still getting up to speed on readiness, the Council is helping stakeholders understand and respond to the incoming changes through resources on its PCI Perspectives blog.
You can also gain a lot of insight and guidance from in-person events, which is why Reflectiz will be attending the PCI DSS convention. This year’s US event takes place from September 12 to 14 in Portland, Oregon. It’s an ideal opportunity for community members to connect, share knowledge, and discover what’s new from the brightest minds in payment security.
PCI DSS v4 Requirements Updates
You can find all the changes to the requirements listed here. We would also recommend that you review our compliance checklist article here along with our article on the new requirements here. We refer to them as ‘best practices’ in the latter piece (which they are!) but remember that from 31 March 2025, they officially become requirements.
It isn’t necessary to repeat all of the information from those links here, but it is worth highlighting some of the most significant changes that Reflectiz takes care of.
6.4.3 focuses on the management of scripts that are loaded and executed in the consumer’s browser during payment transactions.
According to this section, organizations must manage all payment page scripts that are loaded and executed in the consumer’s browser in the following ways:
• Script authorization: A method must be implemented to confirm that each script is authorized.
• Script integrity: A method must be implemented to ensure the integrity of each script.
• Script inventory: An inventory of all scripts must be maintained with written justification as to why each script is necessary.
These measures are intended to minimize the likelihood of an attack through this vector by ensuring that scripts are explicitly authorized and their integrity is maintained. By maintaining an inventory of all scripts with written justification of why they are necessary, organizations can better manage and control those that are loaded and executed on their payment pages. This helps to protect users against threats such as Magecart or web skimming attacks, which work by tampering with or altering scripts.
The Reflectiz solution helps you meet both requirements by creating and maintaining an inventory of all in-house and third-party scripts and software and it alerts users to any attempt to compromise them.
11.6.1 comes, again, in response to the increasing danger from web-skimming attacks. It calls for a mechanism that can detect tampering with HTTP headers and the contents of payment pages as received by the customer’s browser. It requires this ‘mechanism’ to report any such changes promptly. Again, Reflectiz detects and alerts users to such changes and gives you the control to greenlight appropriate behaviors, block risky ones, and refer others to security teams for further investigation.
Doing the Work
The Transition Process
Here are some pointers for where to begin with the transition process:
• Involve all departments and functions in the transition plan.
• Clearly define roles and responsibilities for each requirement.
• Employ effective project management, maintaining accurate plans and tracking progress.
• Thoroughly document policies and procedures to support security control implementation, including new documentation requirements in PCI DSS v4.0.
Use Trusted Partners
• Educate and train staff on their roles in data security and PCI DSS compliance.
• Partner with qualified professionals (PCIPs, ISAs, QSAs) for security control implementation.
• Utilize technologies and solutions validated against security standards for protecting payment data.
Conduct Your Own Assessments
• Start preparing for PCI-DSS assessment early.
• Conduct gap assessments to identify areas needing improvement.
• Regularly test security controls to ensure proper implementation.
• Establish open communication with the assessment team before the assessment.
Treat Security as a Continuous Process
Recognize that PCI DSS v4.0 supports continuous, long-term security processes. Thinking of every level of your organization needs to be that security is not just an afterthought, but an integral part of every process and an ongoing commitment.
• Choose security controls that align with business and security needs.
• Conduct regular staff training and awareness sessions.
• Integrate security into everyday practices and organizational culture.
• Treat security as an ongoing process to reduce security incidents and breaches.
By following these steps, organizations can enhance their readiness for PCI DSS v4.0 compliance assessments and maintain strong security practices over time.
We can help you
The fact that PCI-DSS v4.0 allows you to take a customized approach to meet its requirements means that you can use innovative solutions such as the Reflectiz platform to manage your security posture and elevate your compliance level before April 2025 rolls around.
Reflectiz is committed to helping you protect your business and your customers by meeting and maintaining the PCI DSS standards, and for the next 30 days, we’re offering you full access to our innovative PCI Dashboard FREE! This powerful, yet straightforward tool takes the guesswork out of monitoring your current level of compliance with the PCI-DSS v4.0 standard, empowering you to identify security gaps and respond effectively.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







