Everything You Need to Know About Port Scanning

Port scanning serves as a method to detect accessible ports on a specific server or network. Through a systematic examination of port ranges, both malicious individuals and security experts can acquire valuable information about potential security vulnerabilities and exploitable weaknesses. Many businesses with an online presence now rely on web applications to deliver the functionality their customers expect, but using these apps has also given threat actors many new avenues to exploit: 65,536 of them in fact. The web app servers which host and deliver web applications offer thousands of entry points called ports that need to be thoroughly scanned to identify vulnerabilities.
Reflectiz, a cutting-edge cybersecurity solution, has recently unveiled its innovative new comprehensive web app server scanning capability. In this article, we will explore what web app servers are, the significance of open ports, the concept of port scanning.
Understanding Web App Servers
Web app servers are software systems responsible for handling requests and delivering web applications to end-users. They facilitate the interaction between client devices (such as web browsers) and the web applications hosted on them. These servers play a pivotal role in processing dynamic content, executing server-side scripts, and managing data transactions to deliver a seamless user experience.

The Significance of Open Ports
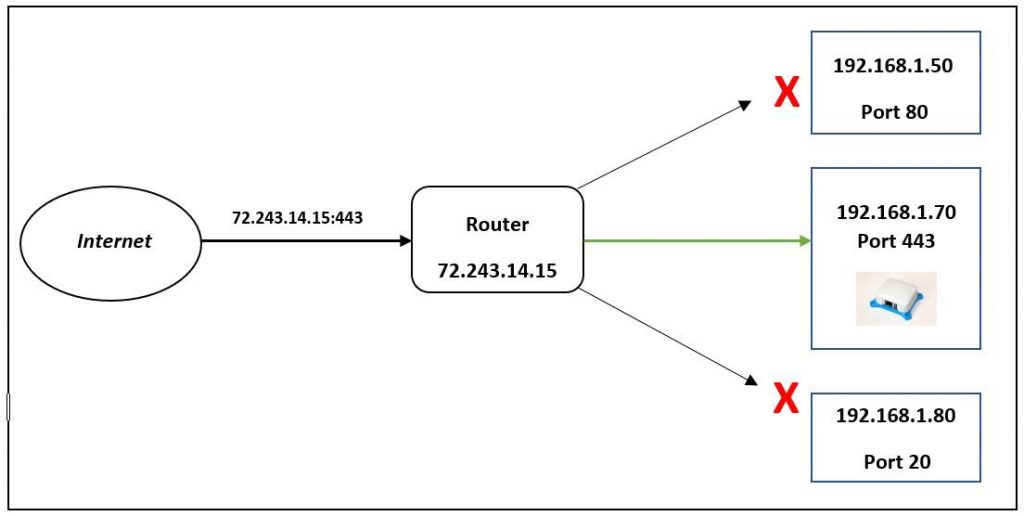
To communicate with web app servers, clients initiate connections through specific ports. These ports act as virtual gates through which data packets flow between different devices. An open port refers to a port that is accessible and actively accepting incoming connections. While some open ports are essential for normal web application functionality (such as port 80 for HTTP or port 443 for HTTPS), others can potentially serve as entry points for unauthorized access or cyber-attacks.
Port Scanning Explained
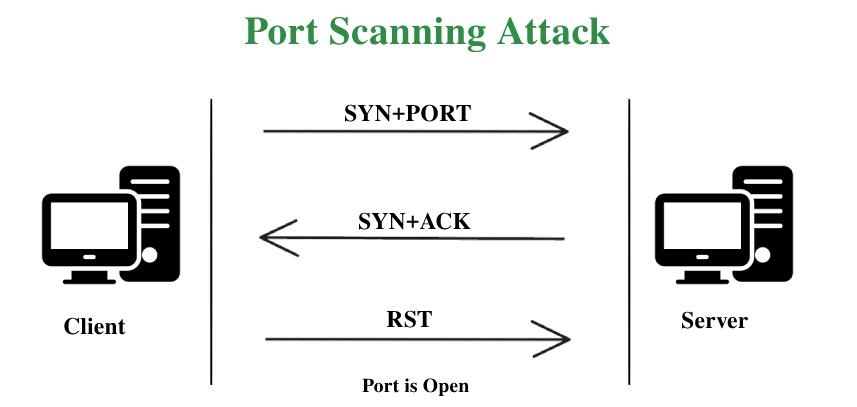
Port scanning is a technique used to identify open ports on a target server or network. By systematically probing a range of ports, both hackers and security professionals can gain insights into potential vulnerabilities and weaknesses that can be exploited. Port scanning provides valuable information about the services or applications running on specific ports, enabling attackers to target known vulnerabilities or administrators to strengthen their defenses.
Port Scanning Techniques
Port scanning uses a variety of techniques to see which data packets are sent to which destination port numbers. Several of these include:
- Ping scans: These are considered to be the simplest of the port scanning techniques and are also known as internet control message protocol (ICMP) requests. Ping scans send ICMP requests to a variety of servers in the hope of getting a response. Administrators can use them for troubleshooting problems, and a firewall can block and disable them.
- Vanilla scan: This is another basic port scanning technique, and it works by trying to connect to all 65,536 ports at once by sending a synchronize (SYN) flag, or a connection request. When the connection is acknowledged or it receives a SYN-ACK response, it reacts by sending an ACK flag. This kind of scan is accurate, but it’s also one that can easily be detected because firewalls always log full connections.
- SYN scan: AKA a half-open scan, this sends a SYN flag to the target and awaits a SYN-ACK response. If the scanner receives one, it doesn’t reply, so the TCP connection does not complete, and it doesn’t get logged. So, the sender can quickly discover if the port is open which is why it’s popular amongst hackers looking to sniff out weaknesses.
- XMAS and FIN scans: XMAS (or Christmas Tree) scans and FIN scans are more surreptitious methods. XMAS scans are so-called because they turn on a set of flags within a packet, and when you view them in a protocol analyzer such as Wireshark, they resemble the blinking lights of a Christmas tree. It sends a set of flags, and when these attract a response, they can give away information about the status of the ports, and also the firewall. FIN flags are frequently used to end an established session, but in a FIN scan the attacker sends one to a particular port. The way that the system responds to this can give the attacker clues about how the organization uses its firewall and how active it is.
- FTP bounce scan: This lets the sender hide where they are by bouncing a packet via an FTP server.
- Sweep scan: This initial port scanning technique sends traffic to a port across several network computers to discover which ones are active. It does not share any information about port activity but lets the sender know if any systems are being used.
Port Scanning Attacks
There have been several examples of cyberattacks that exploited open port vulnerabilities. Open ports lacking sufficient protection can expose your IT environment to serious risk. Threat actors frequently try to exploit open ports and their applications using spoofing, credential sniffing, and other methods.
WannaCry Ransomware
The WannaCry ransomware crypto worm was a global cyber attack campaign that made headlines in May 2017. It targeted Windows computers, encrypted their data, and demanded ransom payments in Bitcoin. It used EternalBlue to spread, an exploit developed by the NSA for Windows systems. This kind of attack begins with port scanning of the target network for devices that accept traffic on TCP port 445, which confirms that the system is running SMB. Once it’s underway, this kind of ransomware attack can be devastating because even after paying the ransom there is no guarantee that the attackers will restore the victims’ data.
Port Scanning Attacks on RDP
RDP is Microsoft’s Remote Desktop Protocol, and it does exactly what the name suggests. It is a tool that allows anyone to control a computer remotely, giving them the same level of privileges that they would have if they were sitting at the actual machine. This is what makes it such an attractive attack vector for ransomware distributors, and why it’s become one of their most popular methods.
Cybercriminals routinely use compromised servers to scan the internet for open RDP ports by trying the RDP default port: TCP 3389. The attackers using the compromised server then try to gain entry using brute force, trying commonly used username and password combinations to discover the RDP login credentials. If you don’t have adequate defenses in place, then there’s a chance that one of these speculative attacks might get lucky and hand control of your machine to an unauthorized person.
Other Port Scanning Targets
Aside from RDP, attackers also do port scanning for a variety of other network protocols, such as FTP, IMAP POP3, SMTP, and SQL. The main reason for doing this is so that they can circulate malware, but another reason is to set up botnets.
Mirai (which comes from the Japanese word for “future”, 未来) is malware that turns Linux-powered networked devices into botnet components for us in large attacks. It primarily targets Internet-connected devices, items like doorbell cameras, printers, and home routers. It exploits security holes in these pieces of equipment and can potentially combine millions of them to launch attacks that bring domains to their knees.
Mirai works by actively scanning the internet for open telnet servers on ports 23 or 2323. When it discovers one, it tries to log in using a long list of default credentials. These can often be something very easy to guess like “admin” for both the username and the password. Customers are supposed to change these as soon as they set up the new device, but not everyone remembers to do this. Once Mirai has successfully logged into one of these devices it can co-opt it for use in the botnet.
Port Scanning Defense
Strengthening Web App Security Through Server Scanning
To combat these vulnerabilities Reflectiz leverages its state-of-the-art port scanning technology to perform comprehensive scans that detect open ports and identify potential vulnerabilities that could be exploited by malicious actors.
Key features and benefits of Reflectiz’s web app server port scanning capability:
- Proactive Vulnerability Assessment: Reflectiz enables organizations to proactively identify and address vulnerabilities in web app servers, reducing the likelihood of successful attacks.
- Open Port Identification: By scanning for open ports, Reflectiz highlights potential entry points for unauthorized access, assisting administrators to implement targeted security measures.
- Patch Management: Reflectiz helps administrators stay on top of security patches and updates for web app servers, ensuring that known vulnerabilities are promptly addressed.
- Enhanced Compliance: By regularly scanning web app servers, Reflectiz aids organizations in meeting regulatory compliance requirements and industry standards, minimizing the risk of data breach penalties, litigation, and reputational damage.
- Real-time Monitoring: Reflectiz provides real-time visibility into the security status of web app servers, enabling users to respond swiftly to incidents and proactively mitigate threats.
Securing web app servers is an indispensable step for safeguarding web applications and protecting sensitive user data. By actively scanning for open ports and identifying weaknesses, Reflectiz enhances an organization’s ability to proactively defend itself against cyber threats, providing peace of mind in an increasingly hostile digital landscape.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Related Articles
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







