Year in Review: The Most Significant Cyberattacks of 2024

Cyberattacks and data breaches have shown no sign of slowing down during 2024. New incidents have come to light every month, so as 2025 draws near, this seems like a good time to reflect on the most significant cybersecurity challenges organizations have faced this year.
January: Midnight Blizzard
The biggest story of this month was Russian hackers stealing emails from Microsoft’s senior leadership, cybersecurity, and legal teams, in an incident that also affected multiple US federal agencies. The finger of blame was pointed toward a Russian state-sponsored threat actor called Midnight Blizzard (AKA APT29 or Cozy Bear). The hack was detected on January 12, but it’s believed the group had already done the groundwork with a breach in November 2023. Midnight Blizzard had used a password spray attack to infiltrate a legacy test account that lacked multi-factor authentication.
Nation-state actors are well-funded, sophisticated, and persistent, so two-factor authentication should be the bare minimum that any organization should be using to secure their accounts against these kinds of social engineering attacks.
February: Change Healthcare
This month saw the largest-ever US healthcare breach. Change Healthcare suffered a ransomware attack that exposed the records of around 100 million patients. This was causing massive disruption in the healthcare system, preventing pharmacies, hospitals, and healthcare facilities from processing claims and payments. This huge breach will probably affect the lives of its victims for years to come, as thieves use or sell their data for fraud and identity theft purposes.
The company paid ransomware group ALPHV/Blackcat $22 million to get the data back, but its leaders proved there’s no honor among thieves when they failed to pay the people they used to carry out the hack. But these folks still had the stolen data so to recoup their losses they issued a second ransomware demand. If you happen to know where any of them might be hiding the US State Department is offering a reward of $10 million.
This breach was preventable because the hacker stole login credentials that weren’t protected by two-factor authentication.
March: AT&T Breach
A hacker known as MajorNelson released a 5GB archive containing sensitive information belonging to roughly 73 million current and former AT&T customers. This data included full names, email addresses, physical addresses, and in some cases, social security numbers and dates of birth. Initially, AT&T denied it was their data, but later relented. The archive had been available on the Dark Web since 2019 after the Shiny Hunters hacking group first leaked it, so all MajorNelson had to do was make it public.
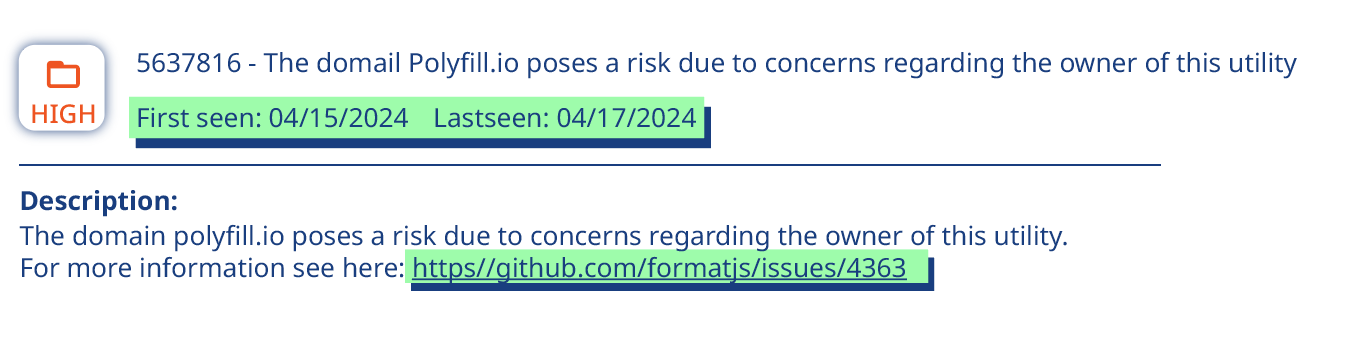
April: Polyfill.io Supply Chain Attack
AT&T revealed even more historical customer data leaks this month (another 109 million records!), but the other big story was the supply chain attack that emerged after a Chinese company called Funnull acquired the domain Polyfil.io in February and the JavaScript resource library that came with it. The new owner had tampered with the code, and it was now redirecting users to gambling and adult sites.
A Polyfill is a piece of JavaScript that adds modern features to older browsers that don’t natively support them, so the library was popular among developers wanting to ensure compatibility across platforms.
Alarm bells began ringing throughout the industry because Funnull was an unknown quantity. It had no previous history with this type of business and speculation began to swirl that it might be up to no good, and it was. Eventually, 380,000 hosts were embedding compromised scripts from the Polyfill.io domain, with notable victims including companies like Warner Bros, Hulu, and Mercedes-Benz. The injected code was designed to generate payloads based on HTTP headers, allowing it to evade detection by activating only under specific conditions (e.g., certain devices or times of day). This stealthy approach made it difficult for site owners to identify the compromise.
May: The Kaiser Permanente Breach
US healthcare conglomerate Kaiser Permanente apologized for leaking the personal details of 13.4 million current and former patients. This was a second offense, as it lost 70,000 patient records in 2022. On that occasion, hackers got into an employee’s email account, but this time, no outside agent was trying to break in. The company said that “certain online technologies,” had mistakenly sent search terms that patients had used on its website to search engines.
While there was no malicious intent behind this breach, the results can be just as serious. Misconfigurations of tracking technologies can potentially trigger data regulation fines and also dent consumer confidence. At the very least, the company had to invest in a cyber security specialist to mitigate the damage, and it covered the ongoing expense of two years of free identity theft protection for all those affected. The true cost isn’t known yet, but the average cost of a data breach in the US in 2024 is $9.36 million.
June: Magcart Attacks Are Back
Magecart attacks returned with a bang in the form of CosmicSting, the nickname for some Adobe Commerce and Magecart vulnerabilities cataloged as CVE-2024-34102 in the National Vulnerability Database. This campaign has so far made 4,275 web stores vulnerable to attack, and seven distinct hacker groups have been seen in the wild attempting to plunder them. Normally, when one group breaks into a site, it locks it against the others, but CosmicSting prevents this, so they’ve been squabbling like hyenas around the same kill.

July: KnowBe4 Espionage
Cybersecurity company KnowBe4 accidentally hired a remote software engineer who was actually working for the DPRK in North Korea. He managed to get on the payroll thanks to a stolen US identity and a doctored photo and somehow managed to get through interviews and pass background checks. Straight away he uploaded malware to his company workstation. As a heavily sanctioned pariah state, North Korea is desperate for foreign cash, so it helps its IT workers trick their way into these lucrative gigs in return for the lion’s share of the pay.
The company contained the incident straight away and said they isolate new workers from key systems to avoid the potential damage caused by this kind of attack.
August: Hacking Continues
A couple of incidents stand out in August. There was the Mobile Guardian classroom management platform breach, in which a hacker gained access to the system and remotely wiped data from at least 13,000 students’ iPads and Chromebooks.
Hackers also leaked 2.7 billion data records containing U.S. citizens’ personal information on a hacking forum, and in Ohio, the Rhysida ransomware group leaked over three terabytes of stolen data from the City of Columbus.
September: 23andMe and More
The UK’s Transport for London suffered a major cyberattack that disrupted services and caused significant operational challenges.
Healthcare nonprofit Planned Parenthood was hit with a 93GB data breach containing its clients’ sensitive personal information. The ransomware group RansomHub threatened to leak the data.
The popular DNA testing company 23andMe agreed to pay a $30 million settlement after a hacker called Golem stole 6.9 million users’ records in 2023. The hack went undetected for months. Brute force attacks using email addresses and passwords leaked in previous, unrelated breaches made the lake possible.
23andMe wrote to victims, blaming customers for negligently recycling old passwords in the wake of previous security incidents that weren’t related to 23andMe.
Telecommunications giant AT&T had to pay $13 million to resolve a Federal Communications Commission (FCC) investigation related to a cybersecurity incident, Lehigh Valley Health Network lost out in a big way too. It agreed to pay $65 million to settle a class action lawsuit brought by 134,000 patients. A hacker called BlackCat Ransomware breached its systems, stole patient data, including images, then demanded a ransom. When the hospital provider refused to pay, the hacker made the information public.
October: Wayback Machine Breach
This month hackers accessed the user authentication database of the Internet Archive’s Wayback Machine, harvesting the login credentials of 31 million users. Additionally, multiple DDoS attacks also hit the site.
Chinese hackers infiltrated at least 20 Canadian government networks over four years and compromised cell phones used by some senior members of the Biden and Harris US presidential campaigns.
November: SSCL UK Breach
A breach at Shared Services Connected Ltd (SSCL), a contractor for the UK Ministry of Defence, exposed sensitive payroll data of up to 272,000 current and former military personnel. The responsible party still remains unknown.
Conclusion
Your web environment with its long list of dependencies needs constant protection from attackers who never sleep. Choose Reflectiz to keep your organization safe in 2025. Sign up today.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!








