Instant Justice: WeLeakInfo Hacked with a Ex-domain Reuse Attack

Expired domains (ex-domains) have always been easy targets for hackers and cybercriminal groups. The bad news is that this trend is not going away anytime soon. In a bizarre turn of events, WeLeakInfo, the FBI-seized illegal information vendor, has been hacked via a classic expired domain exploitation attack. Talk about stealing from the bad guys. Let’s dive into it.
Before being shut down by the FBI in early 2020, WeLeakInfo was the go-to website to sell and buy stolen data and personal information. But even the bad guys are not immune to hacks. Over 20,000 cybercriminals who used the once-popular WeLeakInfo platform, have now become victims. Their stolen credentials and personal information is now being sold on the dark web.
This article will touch on what happened and how this can be avoided.
WeLeakInfo: What Exactly Happened?
WeLeakInfo was the ultimate hacker playground. Names, email addresses, IP details, phones numbers – there is no stolen record you couldn’t find on this platform. Estimates say that data from over 10,000 data breaches, including a total of over 12 billion user credentials, has been hosted on WeLeakInfo over the years. Transactions were made via the Stripe payment method.
A well-known hacker (“Pompompurin”)recently made a huge revelation on Raidforums, a popular cybercriminal forum. He exposed his exploit – WeLeakInfo payment and activity logs that were stolen due to the recent domain expiry of “WeLeakInfo.design”. This was a crucial domain as it was used for collecting emails and documenting sensitive payment details.
This expired domain was traced back to 2016, when it was registered with Dynadot, a domain registrar where the main “WeLeakInfo.com” also resided. However, WeLeakInfo.design was later shifted to a different registrar, Namecheap, which eventually expired. “Pompompurin” completed the hack by releasing screenshots of himself logged into WeLeakInfo’s Stripe.com account.
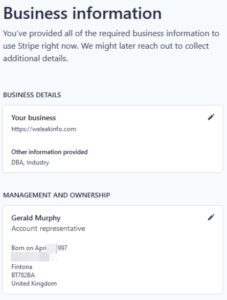
Interestingly, management and ownership details were updated to a U.K-based address. The National Crime Agency (NCA) has already made some arrests.
How Are Ex-Domain Attacks Executed?
The rapid digitalization of retail, banking, finance, insurance, healthcare, and ticketing services have created a complex ecosystem of third-party services and cross-linked domains. Third-party applications help boost time-to-market and productivity, but also create dependencies with external applications and as we are seeing now – with expired domains.
There is bad news. Traditional application security tools and web controls simply cannot detect these dynamics. Your website can be using over a hundred remote domains that are communicating with browsers and allowing hackers to create new attack vectors, but you can not know about it until it’s too late. This is becoming a huge cybersecurity challenge today.
How are attack vectors created with ex-domains? It’s pretty straightforward.
Let’s assume you have a website with a script that is loading information from an expired domain. Assume it’s InstantKarma.com. The script is there, because maybe, someone forgot to remove it, or the company that had control on the script was sold. A hacker now can purchase InstantKarma.com for a small sum of money and he has a potent attack vector to access the website. It’s that easy.
All the hacker needs to do after that is to manipulate the response to when the script is being called. For example, if you have planted a Line of Code (LoC) for the expired domain – <script src=”InstantKarma.com” /> – the hacker can then simply replace this script stored on InstantKarma.com with a malicious one. The new script, or malware, will then execute and enable the hacker to initiate data theft via Persistent XSS or other Phishing actions.
Related: The Risks of Ex-Domain Re-Use on Websites
This cybercriminal activity is made possible by lack of transparency. Online businesses need to know what is going on under the hood of their websites. Also, as seen in the WeLeakInfo case, this is true even when the website is offline or seized by legal entities. In the aforementioned case, none of the involved sides made sure that the seized website was secure. It was just moved offline.
The Ultimate Solution: Ongoing Monitoring
In a nutshell, you should be closely monitoring your digital assets inventory, which includes all domains and scripts in your ecosystem. There are no shortcuts. The challenge lies in the fact that many of those third-parties resources aren’t managed directly by you. This creates security loopholes and blind spots that can be exploited by hackers without being detected.
Here are three top best practices you need to adopt as soon as possible. These are not silver bullets by any means, but can be useful additions to your strategy:
- Creating an Ongoing Inventory – Once you have tracked your assets, create an inventory with ongoing validation of their status. With domains expiring or switching hosts constantly, only proactive domain governance can help you steer clear of trouble and stay on top of things.
- Content Security Policy (CSP) – This security tool has been around since 2004. It helps detect unauthorized and unplanned requests (think payment and checkout pages on websites). But it must be noted that this methodology requires ongoing configuration and maintenance to be effective.
- Subresource Integrity (SRI) – This methodology uses hashes to help the browser verify that the code that it is fetching has not been manipulated. A quick disclaimer. This technique will help if the attacker is considering altering the remote script.
Related: CSP – Not Exactly a Magecart Vaccine
Hosting scripts on your own servers is another important step you can take to be on the safer side and reduce the use of other potentially-exploited domains.
These best practices will help elevate security, but there is no real replacement for ongoing monitoring of remote domain activity and dependencies with external applications. You need dynamic assessment and tracking of your domains (active and expired ones) to stay on top of things and avoid data breaches or leakages. This is the only way to stay safe today.
Ex-Domain Security: No Longer a Choice
Optimized cybersecurity standards require a proactive and dynamic approach. Most businesses invest in traditional AppSec tools, but many fail to address their security blind spots. These blind spots are being created in part due to unmonitored remote domains. This is proving to be an achilles heel when it comes to Ex-Domain security, something only transparency can solve.
Only scanning your website ecosystem and eliminating all redundant remote domain dependencies on an ongoing basis can keep your website safe today.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







