Rogue Pixels Make Healthcare Industry Easy Target for Cyberattacks

As HIPAA confirms that more than half of medical organizations have suffered a healthcare third party breach in the past 12 months, it’s time for the Healthcare industry to think again about how to secure their third party apps like Meta and TikTok Pixels.
This year, healthcare data compliance regulator HIPAA announced that 55% of healthcare organizations have suffered a data breach as a result of a third party.
Unfortunately, the onslaught of cyberattacks against the Healthcare sector is a growing concern. Between 2015 and 2019, more than 75% of data breaches were in the medical industry, with over 1,500 overall. Since then, between 2019-2021, we’ve seen the numbers double. No surprises, as medical data is some of the most valuable to steal and sell on the Dark Web, and the fallout from a data breach that concerns Personal Healthcare Information (PHI) can be catastrophic.
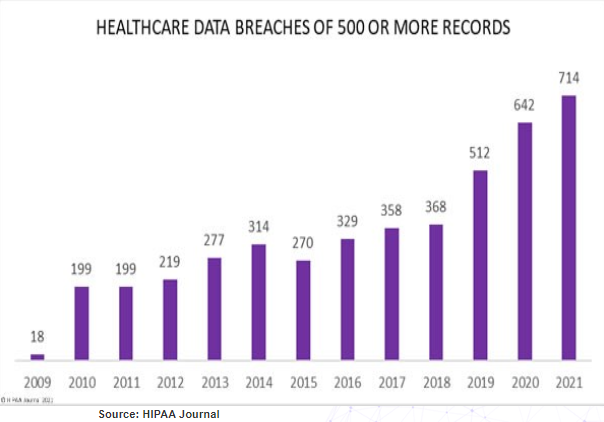
However, in the past few years, a worrying trend is emerging, linking healthcare cyberattacks to the use of third party vendors.
The Growing Use of Third Party Applications
Today, the use of third party applications is ubiquitous across all sectors, and healthcare is no different. These applications are used for a wide range of purposes, such as collecting healthcare data when customers use online systems, tracking behaviors for usage analytics, or integrating with internal healthcare systems to add functionality such as remote healthcare or monitoring.
While third parties may work hard to secure their applications internally, the communication channels between the app and the healthcare organization are less controlled. Last year, a shocking report was released on vulnerabilities in the Fast Healthcare Interoperability Resources (FHIR) standard, which as of 2023, all healthcare IT vendors are required to have in place. While the apps built internally were not found to have vulnerabilities, testing third-party programs allowed the researchers to pull over 4 million patient and clinician records from more than 25,000 providers.
For cybercriminals, it can be far easier and more effective to attack a third party, who often has less robust cybersecurity measures in place, or who can legitimately access a healthcare provider’s data and move unseen or without raising alarm. As permissions are granted to the third party to access, send and even manipulate data, the healthcare organization’s security protocols may not even trigger an alert.
As well as seemingly legitimate access, if a third party does have vulnerabilities, any attack against their organization will lead cybercriminals straight to your own.
Healthcare Third Party Breaches Escalate in 2022
The risk is growing year on year, with 2022 no exception. Here are just a handful of the most prominent healthcare data breaches from the past 12 months, all of which can be traced back to a third-party vulnerability.
Advocate Aurora Health: Wisconsin’s largest healthcare system may have exposed the PHI of up to 3 million patients, due to Google and Facebook Pixel usage on their website. The organization says that these technologies were implemented to gather information to “better understand patient needs and preferences” and they have now been” disabled and/or removed.”
Eye Care Leaders: ECL is one of the top providers of ophthalmology-specific practice management and Electronic Healthcare Record solutions, and 8 different care providers covering millions of individuals may have been impacted by a breach of its cloud-based EMR systems. Due to the connected nature of its products, the data of more than 2 million patients was put at risk.
Shields healthcare services: Shields provides management and imaging services for 60 healthcare partners and 2 million patients, including MRI or PET scans, as well as surgical services. A hack that went unnoticed for 2 weeks disclosed some of the most sensitive data available, such as Social Security numbers, dates of birth, addresses, billing information, and medical treatment information.
Of course, third-party vulnerabilities are not limited to the healthcare industry alone. Recently, large tax preparation services such as H&R Block and TaxSlayer have experienced the negative effects of Meta Pixel, as users’ sensitive financial and personal information has been sent to Facebook. Even daycare apps with the most sensitive information pertaining to young children and their whereabouts has been found to be sent to third-parties such as Facebook and Branch.io because of tracking pixels.
According to Forrester Research in relation to what it calls the “Meta Pixel fiasco”, businesses of all kinds “need to evaluate what data they’re sharing and with whom — and while that may sound like an obvious statement, the examples above show far too many companies are skipping this critical assessment.”
The simple question is, do you know what scripts and tools like Meta Pixel are doing behind the scenes on your website? And are you willing to trust them, sight unseen?
Protecting Healthcare Organizations Means Protecting Against Third-party Vulnerabilities
There is no longer any doubt that the risk of third party vendors is your own risk as a healthcare organization. If a third party is breached, and your own patient or employee data is compromised, the compliance risk and the fallout will land firmly in your own backyard. Today’s healthcare organizations have a responsibility to visualize and secure third-party applications from day one.
The answer cannot be to simply disable third-party applications altogether. After all, digital applications perform essential services such as linking legacy systems of record to the cloud, remote healthcare services, online appointments and scheduling, and facilitating the advent of medical IoT and other critical devices.
Instead of throwing out the baby with the bathwater, healthcare organizations need to get two steps ahead of the risk. It is a legal requirement to have visibility and control over all of the data under their roof, and that includes what is handled by third parties.
Reflectiz provides a full and continuous inventory of all applications that are connected to your website, including both third party apps, and fourth party digital apps which are another step removed. At all times, you can see which applications your website is connected with, who has access to sensitive information like end-users’ PHI, and where they are sending that information, if applicable. You can monitor all of your digital services, and block anything that deviates from normal usage and behavior.
With Reflectiz in place, you’re secure against third-party data breaches, compliant with HIPAA and any other privacy laws, and most critically of all — you’re safe hands for your patients’ trust.
Do you want the confidence that Meta Pixel and other trackers aren’t sending user data to remote servers? Schedule a demo and start proactively managing your data.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







