The Best SCA Tools for 2024

Updated on Aug 1st, 2024
With much of the tech we use every day now relying on open-source code, it’s safe to say that the digital economy runs on open-source, but as widespread and as important as it is, that doesn’t mean everyone knows how to keep it secure.
Part of the problem is sheer volume. There is now too much open-source code available for anyone to check manually. There is an automated method though – Software Composition Analysis (SCA). SCA tools can analyze the open-source software in a codebase to evaluate its security, quality, and license compliance, and we think with cyber-security threats on the rise and competitors chasing ever quicker times to market, this class of tools is indispensable.
In 2024 you need to know that the open-source code your business relies on is fast, secure, and reliable, which is why SCA tools must be a part of your business security toolbox.
Who Needs SCA Tools?
With the growth of cloud-native applications and a rising number of businesses using multiple cloud services, a dependable SCA tool is necessary to protect your business. The emergence of hybrid work structures has created increasingly complex IT systems that make it difficult to monitor every cloud service a company uses. On top of that, employees may add further vulnerabilities to the mix by misusing cloud applications, having lousy password hygiene, or introducing other bad practices that expose a company to further risk.
These vulnerabilities are exactly what cybercriminals are looking for. Hackers often target finance and e-commerce companies because of the gold mine of personal and financial data they hold. In 2023 the banking and finance sectors were the world’s second most popular targets for cybercriminals, attracting 18.2% of all attacks, the retail and wholesale sectors were in fifth place with 10.7%, and the Health care sector what is one place lower with 6.3%.
In 2023, there were 353 million victims of data breaches in the US from 3,205 breaches, so the message is clear. If you want to avoid adding your employees and customers to this year’s total, you must protect them.
Companies of all sizes are targets and given that hundreds of them will often rely on the same software for certain tasks, any attack on those centralized services can allow cybercriminals to harvest data from all of them. That was the case with the MOVEit file-sharing software which was the gateway for 2023’s biggest breach. It affected over 1,000 institutions, including Deutsche Bank, Deloitte, Ernst & Young, and several US government agencies.
Small businesses are at risk too. Nearly 85% of data breaches in the US happen to small businesses, and almost 4,000 attempted attacks happen per day. These attacks cost them an average of $120,000 per incident, and 60% of the companies victimized shut down within six months.
The data on cyber-attacks makes it abundantly clear that companies that neglect cyber security will pay exceptional amounts of money in the long run. In 2023, the global average cost of a data breach exceeded $4.45 million, and this number doesn’t include the potential fines and legal fees that could come in the aftermath due to tightening privacy regulations.
It’s also important to consider the importance of SCA tools in a time of unprecedented development speeds. The DevOps market exceeded $8 billion in 2022 and is projected to grow by 20% per year until 2032 when its estimated worth will be $70 billion. Rising competition has pushed companies to release new software and updates at increasingly faster rates, and DevOps helps meet this demand. However, many organizations don’t have enough security employees to test all of their code thoroughly, which means security can often be an afterthought or even left out of the DevOps flow entirely, leaving potential vulnerabilities unresolved.
With the damage cyber-attacks can do to your company in one hit, it’s vital to be proactive with your protection protocols. Read on to learn how an SCA tool can benefit your business and the top SCA tools to consider.
What Is Software Composition Analysis (SCA)?
Software composition analysis (SCA) is an automatic process that detects open-source software in a codebase. SCA tools scrutinize source code, manifest files, package managers, binary files, container images, and more to compile a Bill of Materials (BoM). This is then compared against numerous databases, such as the National Vulnerability Database (NVD). SCA tools can use BoMs to evaluate overall code quality and compare it against other databases to identify any licenses associated with the code. This allows security teams to identify critical legal or security vulnerabilities so they can act quickly to resolve them.
What Can SCA Tools Do for Me?
Developers and companies use SCA tools to assess vulnerabilities and verify that open-source components within their applications are licensed. Research has found that 97% of codebases have open-source components, 53% of which contain license conflicts, and 81% have at least one vulnerability. SCA tools automatically scan for these vulnerabilities and also check for license compliance. As SCA tools are more rigorous than vulnerability scanner software, they are better suited to helping companies at high risk of attacks, like those in finance, e-commerce, and healthcare.
Key Considerations When Choosing SCA Tools
There are a few important considerations you should take into account when deciding which SCA tool will best meet your needs:
1. Integration
To allow your teams to continue working quickly and efficiently, you need SCA software that seamlessly integrates with the tools your teams already use. A key consideration is ensuring that an SCA tool can be incorporated across the software development life cycle (SDLC). You should also choose an SCA tool that works with your application security testing (AST) tool requirements. Begin your evaluation by considering SCA tools offered by your AST to allow for a more tightly integrated experience.
2. Discovery
You can’t fix the vulnerabilities in your code if you don’t know which part of it is open source. To choose an SCA tool, consider which languages it covers to ensure the ones you code with are included. Be mindful of the languages you currently use and the ones you might use in the future. If you don’t think ahead, then you run the risk of outgrowing your chosen tool.
You must also assess the toolset’s discovery methods for finding open-source code. Some scanning package managers are fast but they can miss open-source code if it’s been copied over in pieces or modified. In these cases you need an SCA with a more sophisticated approach to scanning. You also want to choose an SCA tool that can scan binaries, as you may not always have access to the source code.
3. License Data
While much of the focus with open-source software is on security breaches, license risks can be just as expensive. Look for an SCA tool with extensive open-source license databases to reduce your risk of running into legal trouble.
4. Vulnerability Data
Once your BoM has been compiled, it needs to be compared to known security vulnerabilities. SCA tools that combine a diverse set of data resources with a research team dedicated to expanding that data will provide the most actionable and comprehensive information.
Top SCA Tools for 2024
1. Reflectiz
Reflectiz uses behavioral analysis to identify and mitigate risks on customers’ websites. By mapping out all third-party activity on a website, Reflectiz provides the website owner with data about their potential compliance issues and vulnerabilities so they can be remedied in real time.
Best for: e-commerce, healthcare, and financial services companies
Pros: Monitors network activity to detect client-side attacks, an area traditional security solutions are unable to see
Cons: No on-premise deployment
Review: “Great company and great product. They have helped us so much in tuning their product to help make it as easy to use as possible.” Chris R.
2. Jit
Jit orchestrates npm-audit, an open-source SCA solution, so you can integrate it with your CI/CD to run automatically for every new PR. This makes it easy to scan code dependencies for vulnerabilities and run a security audit of the dependencies configured in your project to your default registry.
Best for: Dev organizations
Pros: Increases Dev velocity in alignment with security principles, simple experience, created by developers and for developers
Cons: Requires Dev experience
Review: “Very easy to onboard with this tool; You get a lot of points for the user experience. I like that the plan configuration corresponds to the code representation–very transparent.” Head of DevOps at a SaaS startup of 120 employees.
3. SpectralOps

The SpectralOps platform integrates with all leading CI systems to prevent leaks caused by bad credentials hygiene and human error. This solution allows developers to focus on coding while Spectral monitors the code for possible mistakes that could lead to expensive vulnerabilities.
Best for: Hybrid work environments that need both a cloud and on-premise solution
Pros: Created by developers, for developers.
Cons: Lacks customization
Review: “Spectral is a reliable gatekeeper for our secrets.” Benny B.
4. Snyk
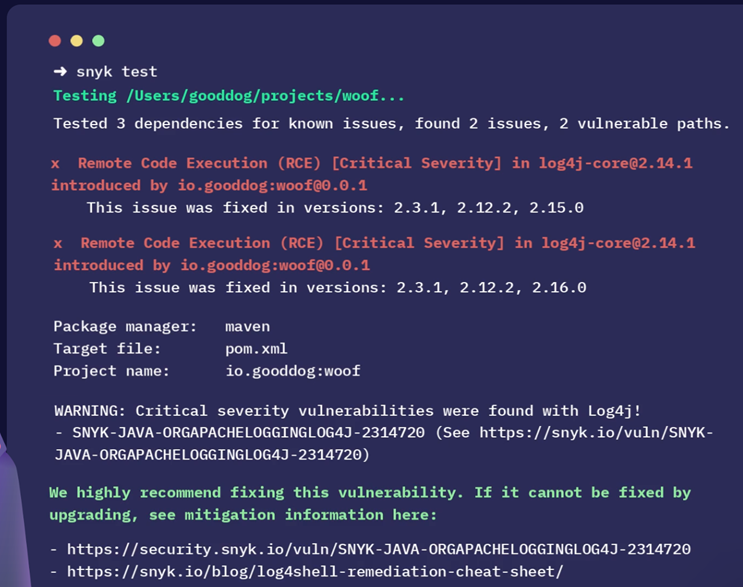
Snyk helps developers to secure custom code, open-source dependencies, cloud infrastructure, and containers from just one platform. Snyk’s solution empowers developers to build security for the whole application.
Best for: SMBs
Pros: Comprehensive and detailed reporting structure
Cons: Expensive for medium-sized businesses
Review: “Powerful analysis to reduce risk in your applications.” Sean P.
5. Black Duck (by Synopsys)
Black Duck helps developers secure code as they write it by automating testing within development pipelines. The solution allows security teams to manage risks throughout the application lifecycle proactively.
Best for: Enterprise and mid-market organizations
Pros: Supports a wide range of languages
Cons: More expensive than other solutions
Review: “It has impressive legal and security third-party software compliance features.” Pratik H.
6. FOSSA
FOSSA is a comprehensive open-source risk management platform used by legal teams to maintain compliance, by security teams to assess and fix vulnerabilities, and by engineers/developers to improve code quality.
Best for: Multiple teams collaborating
Pros: Reasonable pricing
Cons: Lacking license databases
Review: “Easy to use tool to monitor license compliance.” Dhruv B.
7. Wiz
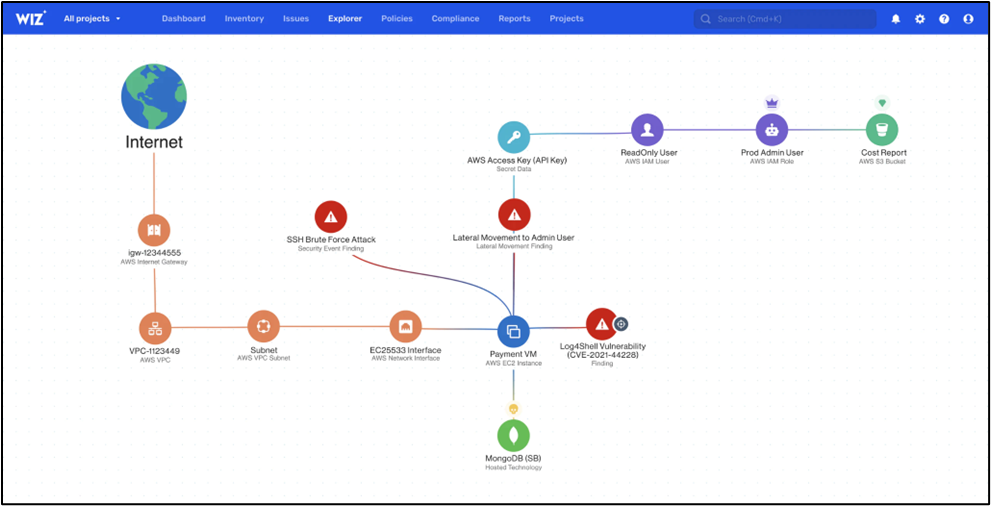
Wiz is a purpose-built platform to handle the complexities of multi-environment, multi-workload, and multi-project cloud estates. Their 100% API-based approach scans every workload and platform configuration for vulnerabilities.
Best for: Multi-cloud and Kubernetes environments
Pros: Fast and simple implementation
Cons: Limited customer support options
Review: “Frictionless Cloud Security for automated visibility and alerting on compliance and vulnerabilities.” Craig S.
8. MergeBase
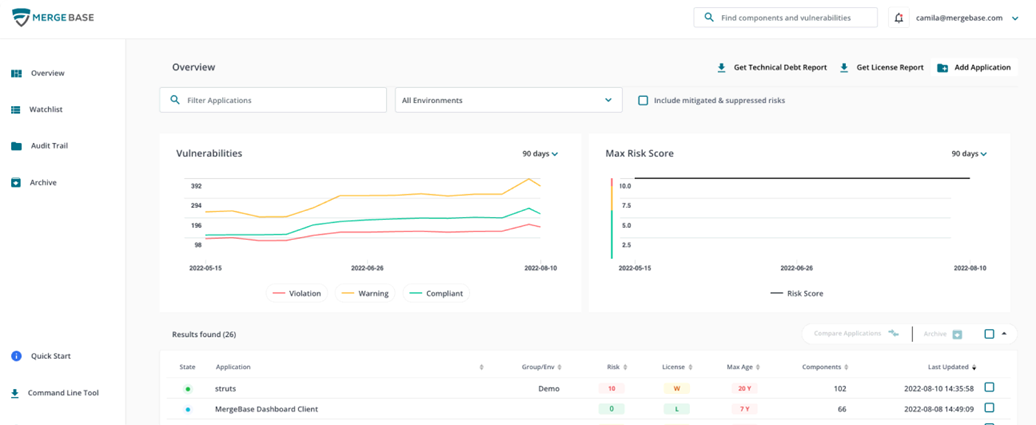
MergeBase offers software supply chain protection that boasts the lowest rate of false positives in the industry and complete DevOps coverage throughout every stage of development.
Best for: Companies with complex supply chains
Pros: Exclusively focused on SCA
Cons: Challenges reading binary
Review: “Excellent for reducing open-source risk.” Gabriela G.
Managing Risks in a Software World
Businesses have become increasingly software-reliant, and many applications they rely on (even in-house ones) involve external code that can expose a company to third-party risk. While SCA tools can help to mitigate these risks, it is also necessary to be vigilant beyond your company’s server. SCA tools should be used in combination with third-party monitoring tools so your business can defend against risks from external parties you lack control over. That’s why the Reflectiz platform expands beyond SCA with continuous web threat management.
Find out how Reflectiz can protect your company by signing up for a free version: https://www.reflectiz.com/registration/
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!







