Companies Like eBay are Port Scanning End-users’ Computers: What Does it Mean and How Can You Protect Yourself?

Article updated on July 2022
If you’ve ever heard that a business website is port scanning its online shoppers – you might be interested in exactly what that means. This article will explain what port scanning is, why businesses like eBay port scan their users, and what it means for you from a security perspective.
Understanding the Client – Server Relationship
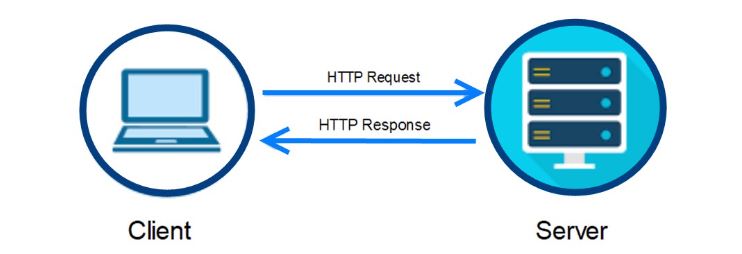
To understand port scanning, we need to understand the client – server relationship when you’re visiting an eCommerce website. The server is the business, which hosts all the online store’s content, and you, as the client, load this via HTML when you visit the website. On eBay, you arrive on the website and you immediately load the product information, all images, the shopping cart, and more. In order for the content to be loaded, the website uses JavaScript code, which runs on the client-side, in your own browser.
JavaScript code has powerful capabilities, and can function without your consent on your computer, according to the rules set by the server – in this case, the website of the business you’re browsing. To give you a better user experience, the JavaScript code will load banners, widgets and popups. So that you can speak to customer support, the JavaScript code will launch a live chat window. It’s responsible for all the dynamic content that we use when we browse. Since HTML5, JavaScript can easily interact with a user’s mobile phone, opening the camera or accessing the microphone, and even reading input from the user.
A Refresher on WebSockets
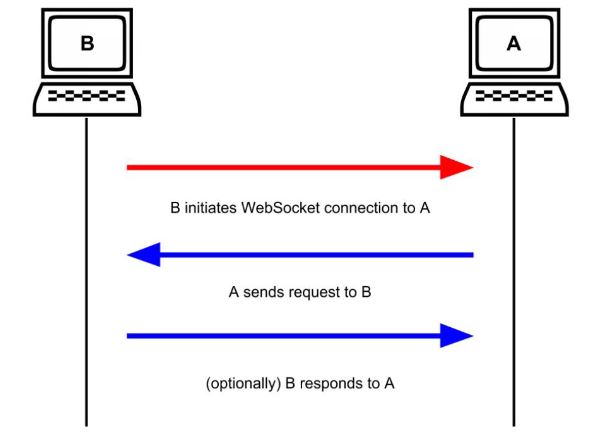
The second part of the puzzle is the use of WebSockets. This is a protocol that more easily allows the client to send requests to the server, for example informing the website that actions have been taken, or asking for more content. Without WebSockets, the user’s browser would need to send HTTP requests with header data every single time they needed more functionality or content from the website. This could quickly become a problem for user experience due to the increase in traffic load.
Instead, WebSockets allow the client to use JavaScript to run a regular TCP request from their browser, so that the server can open a port that has access to the incoming traffic. This is called a socket, and a socket will always require a listening port in order to function.
What’s All of This Got to Do With Port Scanning?
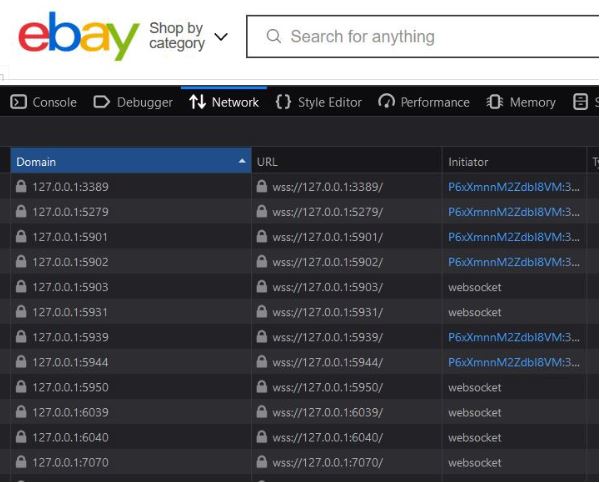
As the JavaScript code can send a WebSocket request to any location, the location can also be a local address. A business might run requests on different local ports and attempt to open a socket for each one of them. By measuring the time it takes to get a response, the server will be able to see if a port is open. An inactive port will take much longer to resolve a request (until timeout), while an active listening port will answer immediately.
You might wonder, why are companies engaging in port scanning in the first place? Most businesses are running port scanning in order to protect their checkout pages. They want to make sure that it is a legitimate user who is sending requests. In order to identify compromised hosts, businesses will test several known ports which are known to be in use by trojans, or by remotely controlled applications. Businesses can obtain a risk score for all services on the client host, and then decide whether they are safe to allow to login or make a payment.
However, just because businesses have a good reason for port scanning, this doesn’t mean there aren’t risks associated with this activity. Websites such as eBay, TD Bank, Walmart, Halifax and more all use port scanning with good intent, but an attacker could use the exact same technique in order to scan all the open services you’re running and find vulnerabilities where they could establish a foothold. In its simplest form, port scanning is reconnaissance – and that information can be used for both good and evil.
How Can Individuals Protect Themselves from Port Scanning?
Port scanning is not an illegal activity unless someone can prove that it was used intentionally to breach privacy or obtain unauthorized access. In most cases as we say above, it’s used to protect a website and increase security.
There’s no doubt that port scanning leaves a bad taste in many users’ mouths however, especially as it’s done without the consent of the website visitors. At the very least, we should expect businesses to alert users to port scanning when they arrive on the website, and update their Terms and Conditions pages and Privacy Policies.
For businesses, remember that every instance of client-side code, especially from third-party and fourth-party applications that run on your website is able to carry out these actions, and port scan your users. If their service or application is breached – this is an open door to your user environments, and you would never notice a thing has changed.
Reflectiz maps all your third and fourth party applications that exist on your website in granular detail, and provides a comprehensive dashboard of all JavaScript code activity. If a digital application changes its behavior, you can spot the issue in real-time, and see exactly what data it is accessing and where it’s being sent.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!