Defacement Attack by Anonymous in websites supply chain

On March 2nd a severe defacement attack hit dozens of Israel’s leading sites, leaving them with a new main featured headline: “Jerusalem is the capital of Palestine”. The long list of affected websites including Ynet, Calcalist, Ivrit, Makor Rishon and dozens of others that also suffered identical web-page damages.
The attackers associated with the pro-Palestinian #opJeruslam campaign of the Anonymous group did succeed in causing significant visual damage, but their goals were far more daring. Alongside the online vandalism, the malicious team also tried to lead another attack, one designed to infect end users with ransomware software. It is almost funny that the extended attack failed due to a basic logic error with the attackers’ code. At the end of the incident and a few hours after the attack began, the breach was located and fixed by the vendor.
Defacement Attack hit dozens of leading in Israel
Exploiting third-party and even a fourth party codes to execute supply chain attacks
In recent years there has been a significant increase in supply chain cyber-attacks. These events are characterized by constant attempts to locate security holes in the entire supply-chain, particularly aiming at the very third-parties that are considered as one of the most sensitive links in it.
Third party technology is a code that is not owned by the site. It plays a vital role and is aimed to provide additional functionality to the site, typically by an external service provider – a vendor. Known third-party examples include almost every possible online tag, ad plugins, accessibility, analytical and engagement tools, site widgets, and more.
Hackers do everything in their power to pinpoint the weaknesses of those third parties and even further to its fourth-parties.
The Saturday night attack infected hundreds of thousands of web-pages in dozens of sites via an accessibility component called Nagich. Through it, the hackers succeeded in their scheme and managed to impact the site directly, changing its content and implementing the attack. Because the attack occurred through the supply chain, the change quickly spread and automatically affected dozens of Israeli sites.
On a practical level, the attack effectively bypassed the site’s security circles and its level of protection. This is also where the great danger lies.
Supply Chain Attacks: How It Works?
Unlike previous attacks, the Saturday night defacement hack did not include a direct attack towards the target sites. Instead, it was performed by changing the DNS record of one of the service providers, the third-party vendor, in this case Nagich. The goal was to load a malicious code into a given page instead of the original code. After the modification, the attack literally spilled through the same “new” malicious code, exploiting hundreds of thousands of web pages that were defaced with unflattering headline and suffered a branding blow.
On a more technical level, we shall explain that the intervention in the Nagich accessibility component was a result of a breach to Nagich’s hosting service: a fourth party vendor called Box.co.il, though it is still unclear how it was hacked.
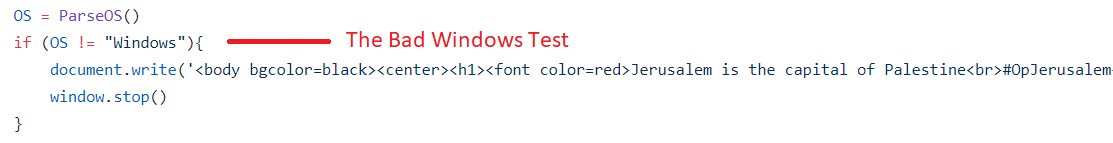
Once the malicious code itself was loaded, the attacker injected a new iFrame to the page, aiming to test and determine which operating system is used. The purpose of this process was to adjust attack scenarios: If the user is using a Windows operating system, a request to download an Adobe update will appear. But in practice, that was not an update, but a ransom file, a Ransomware.
On the other hand, non-Windows computers, were facing the defacement attack, that took its course over the entire site.
In practice, this breach illustrates the difficult challenges that a supply-chain currently poses in the web landscape. The result: sophisticated and threaded attacks with an increasing difficulty of identifying the weakest link that could be the key to a breach.
In this case, it is possible to see how third-party technologies and even fourth-party technology vendors such as Nagish’s hosting company, box.co.il, manage to directly affect the users of the site, avoiding any control options by the affected sites themselves.
Attack indicators
JS Redirected Server: 172.81.182.63
Malicious File Server: 185.163.47.134
Injected Iframe:
https://gist.github.com/ysrael-reflectiz/58d74d7c9174624c409dc1f2083fa3e5
Downloaded File:
http://185.163.47.134/flashplayer_install.exe
Virus Bay Sample:
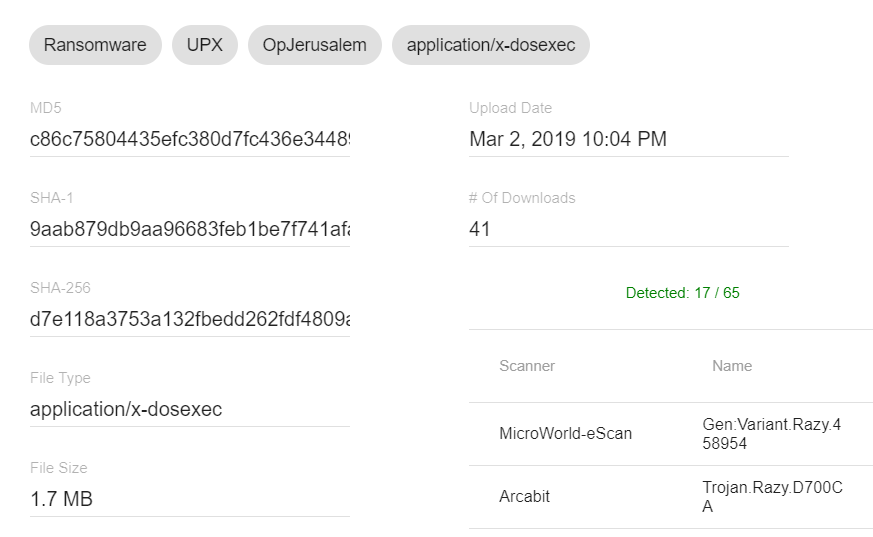
https://beta.virusbay.io/sample/browse/c86c75804435efc380d7fc436e344898
Third parties: it’s all about control
Today it’s almost impossible to find a site that doesn’t use dozens of external scripts massively.
Many sites will find it difficult to survive without these tools, but alongside the benefits, there may also be dangers. Incautious and uncontrolled use can lead to unbearable security threats, information leakage, privacy risks and large number of vulnerabilities.
In fact a third-party code, however useful and safe it may be, is likely to make an independent change to sites pages
Even if it was carefully tested and a security survey or questionnaire was conducted, there is still a chance that the code will undergo an unauthorized change. In most cases the change remains unnoticed, by both development and security teams.
The obvious conclusion points how critical it is to conduct ongoing daily monitoring, at the very least. That way any change in the code is detected immediately, no matter if it’s done due to an error or by deliberate malicious activity while CiSOs and site admins obtain will certainly some peace of mind!
Want to check if your site is exposed to third-party security and privacy risks?
Click here to contact us OR email us: [email protected]
To protect your site and avoid third-party risks, use refSec, our Zero installation solution that allows seamless third-party monitoring from day one!
Reflectiz is cyber-security company that helps online businesses identify security and privacy breaches resulting from third-party technologies installed on their websites.
Subscribe to our newsletter
Stay updated with the latest news, articles, and insights from Reflectiz.
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!