All You Need to Know About Web Skimming Attacks

Web skimming, also known as digital skimming, is a hacking technique that targets digital businesses by manipulating unmonitored and compromised client side web applications. Usually, these attacks are initiated by placing malicious JavaScript (JS) code strategically on payment and checkout pages of the website where unsuspecting users fill in their personal and financial details. Although commonly found on eCommerce websites, banking, finance, healthcare, tourism, and other eService platforms are also being targeted today.
Web skimming attacks have been around for a while, but they took center stage after the 2018 Magecart attack on British Airways, that cost the company more than $1B in mitigation efforts, GDPR violation fines, and other payoffs. While hackers continue to use Magecart scripts to steal payment card information, the newer techniques used by cybercriminals have transformed this malicious activity into a global phenomenon.
Cybercriminals have now started placing web skimmers and Magecart scripts inside images, logos, and favicons to append them to popular JavaScript libraries or in some cases hide them inside website widgets such as the live chat window you can find on every eService website today. The attack vectors are multiplying, forcing CISOs and CIOs to re-think their security strategy. Let’s take a closer look at this worrying trend.
What is Web Skimming?
Before we dive into the specifics of tackling web skimming threats, it’s important to know what they actually are. Web Skimming is a hacking technique where the attacker breaches the payment or checkout page of websites by injecting a malicious script or malware via the third-party apps that are being used by the website. Credit card information and personal information is harvested, often without being detected.
There are multiple variations of web skimming attacks that exploit the complexity of the modern website, but there are two main entry points in use today.
- Direct Attacks – This entry point involves the planting of skimming code (malware) directly on the website that is going to be exploited. The hackers can then exploit zero-day flaws or automate login credentials (also known as brute-force attacks) to locate the right admin details and credentials. It must be said that executing these attacks are not easy and requires a lot of pre-planning and coordination.
- Website Software Supply Chain Attacks – These attacks are becoming popular due to the extensive use of third-parties (over 60 on average on eCommerce sites today). While these third-parties boost functionality fast, they also create new dependencies. Malware is injected into the trusted third-party hosting site, after which the payload is executed via all websites using the web application.
Traditional applications security solutions and tools are not fully effective against these attacks because the malware is baked into the original third-party code. Also, obfuscation methods are evolving and making life harder for CISOs and security teams. The end result – the “action” takes place on the client-side, where the unsuspecting victims are totally unaware of what is going on until it is too late and the breach has occured.
How is Web Skimming Executed?
Web skimming attacks are essentially software supply chain attacks that can reach hundreds or thousands of websites using the exploited third-party web application.
Related: In Retrospect: The SolarWinds Attack
Since third-party HTML/JavaScript code is delivered to the website from a completely different repository that the website owner does not have any control over (and can’t possibly monitor directly), hackers target these very third-party web servers. This gives the attacker unauthorized access to all third-party libraries. It’s then all about injecting the skimming code into one of the existing JavaScript files and hiding it.
Now, when a website user/customer opens the website in a browser or a mobile device, the malicious code gets downloaded to the user’s browser along with the legitimate third-party code. Since the malicious code is downloaded from the third-party servers, the website owner does not have any logs or indications that show the existence of the malicious code or even something suspicious is happening.
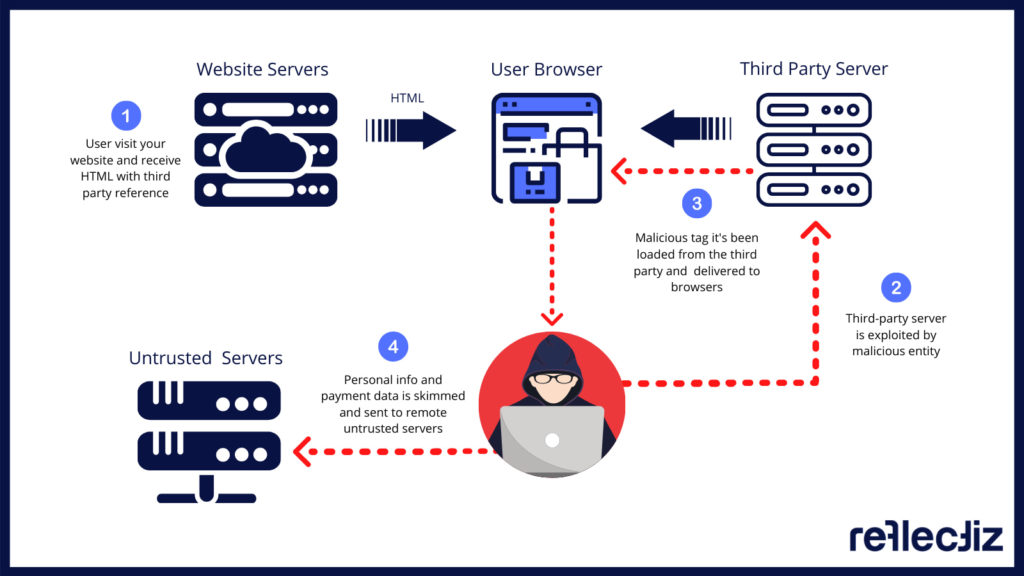
After the payload is executed, the script starts harvesting payment card numbers and personal information of any user data being entered and sends it to the cybercriminals, which is later sold on the dark web. The most common targets – checkout and payment pages on websites. To make matters worse, web skimming exploits often continue to linger for long periods of time before they are discovered by the website owner.
Here are just a couple of “scary” web skimming techniques used recently:
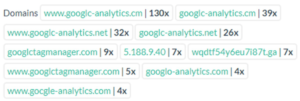
- The Gocgle Campaign – Security researchers exposed the Gocgle campaign in 2020, which has essentially been active starting late 2019, just like the COVID-19 pandemic. This malicious campaign has been tailored around Google products like G-Analytics and uses the uncanny naming similarity to trick users and security teams alike. This skimmer is probably still active on hundreds of websites.
Gocgle Exploits – Imitating the G-Analytics Suite
- Pipka – We can’t possibly continue without mentioning the Pipka exploit, probably the most notorious JavaScript skimmer in recent memory, which was exposed by the Visa Payment Fraud Disruption (PFD) team in late 2019. Why is it so dangerous? This stealthy skimmer has the dangerous ability of removing itself from the HTML code after the execution was complete. A true CISO’s nightmare.
Web Skimming: A Growing Phenomenon
The risk of web skimming attacks continues to plague all online businesses today. Therefore, any digital business that handles personal information and payment card data cannot ignore these multiplying threats anymore. This is before we mention privacy regulations such as GDPR, CCPA, and 23 NYCRR 500, which are now placing a lot of emphasis on optimizing third-party application security standards.
Magecart (a subset of web skimming), is extremely well-known in security circles and has become a global cyber-pandemic today. There are more than a dozen Magecart groups (that we know of officially) that use the illicit Magecart tools that are available on the dark web and coexist under the same group name. There are even politically funded groups that have been traced back to North Korea’s dictatorial regime led by Kim Jong-un.
Did You Know?
As per a recent Symantec report, web skimming attacks are detected after 46 days on average, with many websites staying infected for over a year.
Here are a few of the biggest web skimming cases in recent years:
- Ticketmaster UK Breach In June 2018, Ticketmaster announced that it had fallen prey to a payment-card breach which, upon further inspection, turned out to be a massive web skimming campaign. The attackers compromised Inbenta, a third-party web application vendor, which was exploited to place skimmers on other third-party websites. To make matters worse, traditional security tools failed to detect the issue in real time.The investigation following the Inbenta breach also uncovered pieces of evidence that Magecart group was focusing on compromising other third-party suppliers to steal more payment card data and personal information. In July 2018, Magecart campaign investigations revealed a compromise of more than 800 eCommerce and eService websites from around the world from multiple sectors.
Related: The ICO Fines Ticketmaster UK £1.25 Million
- British Airways (BA)The onslaught continued. In September 2018, BA acknowledged that approximately 380,000 payment card information including names, addresses, bank card details, and CVV codes of 500,000 customers were compromised. This breach, which occurred between August and September 2018, was again attributed to the infamous Magecart group, which added malware to the baggage claim information page on the BA website.The British Airways spokesperson also confirmed that the web skimmer used in the website was also used to exploit the mobile application browser.British Airways’ breach of customer privacy turned out to be a GDPR disaster. The European Union GDPR regulators imposed a fine of $230 million and attributed it to the poor security measures on the British Airways website. The imposition of stringent fines makes the business organizations responsible for any data breach caused by the third-party service providers on their website.
- NeweggWeb skimming was also attributed to the compromise of the popular online retailer – Newegg. Newegg is a popular online merchant website that has millions of registered users. The website sells consumer electronics, entertainment, smart home appliances, and gaming products. The Magecart linked payment card skimmer was found to be active between August 14, 2018, and September 18, 2018.Although the exact number of victims and stolen records is still unknown, the fact that the skimmer was active for almost a month allows us to assume that the attack claimed a massive number of victims. Security experts pointed out that both desktop and mobile application users were affected by the attack, which was also not detected by the traditional AppSec toolkit the company was implementing at the time.
Related: Achieving CCPA with Third-Party Application Security
Third-party Application Security: Making Digital Business Safe Again
Traditional security technologies such as Web Application Firewalls (WAFs), Intrusion Prevention Systems (IPS), and Content Security Policy (CSPs) are failing to detect third-party issues. A further troubling fact is that many third-party vendors incorporate their own third-party applications (fourth-parties) to make use of critical functions. This adds even more dependencies and vulnerabilities into the mix.
Third and fourth parties are helping websites gain out-of-the-box functionality on many levels – analytics, marketing, sales, development, and productivity. But it must be noted that these external applications are also creating serious security blind spots as they are constantly changing and altering the dependency dynamics under the hood, something traditional Application Security solutions can’t monitor due to their static nature.
Continuous third-party application monitoring with real-time insights is becoming the most effective method to gain full visibility and take control of your website. This is the only way to deny web skimming and Magecart attackers from exploiting JavaScript and iFrame codes that are embedded on your website. There is no better way to enforce third-party application security for a safer online experience.
Related: Cybersecurity Effects of Fourth-Parties on Websites
The Bottom Line
As online businesses continue to expand at a rapid pace, with more and more services being digitalized, it has become important to stay secure and compliant (GDPR, CCPA, HIPAA, etc.) at all times. Data security is now much more than just encrypting communications and sharing data safely. eCommerce websites and eService providers need to make sure that their third-party ecosystem is governed and managed properly.
Businesses need to realize that the responsibility for safe third-party implementation falls on the organization and not on the third-party vendors. Traditional AppSec tools and risk management solutions are still good to have around, but only ongoing monitoring and tracking on third-party web applications will help you maintain a solid security and compliance posture against web skimming, Magecart, and software supply chain attacks.
Take control
Stay up to date with the latest news and updates
Your Website looks great!
But what’s happening behind the scenes?
Discover your website blind spots and vulnerabilities before it’s too late!